The Active Directory Rights Management Services (AD RMS) is basically a DRM system. DRM is often used by streaming services to ensure that a piece of music can only be played if there is a corresponding subscription. AD RMS uses a very similar concept, files are provided with a license and encrypted. The license controls what a user is allowed to do with a file (Word, Excel) or an e-mail (read, print, forward). The author of an e-mail or document can determine which license is to be used. The license can also be withdrawn at a later date.
AD RMS can also be integrated into Exchange, the next articles will focus on installation, configuration and integration in Exchange Server 2016.
Surroundings
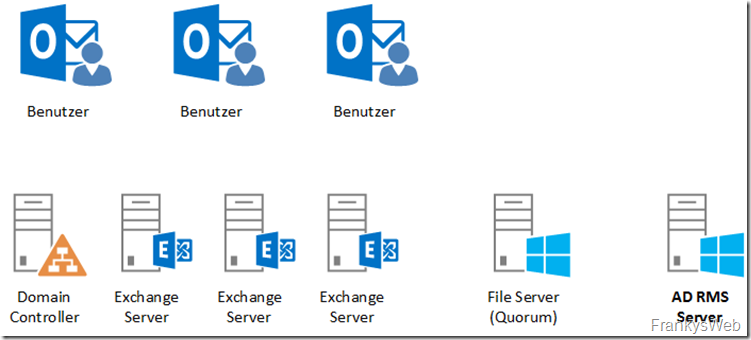
.he environment in which the Active Directory rights management services are installed is as follows:
There are a few users with Outlook 2016, a domain controller, 3 Exchange servers (one DAG), a file server for the quorum and a Windows Server 2012 R2 which is currently only configured as a member server and is to be given the RMS role.
The Active Directory is called frankysweb.de, the users use Windows 10 with Outlook 2016.
Preparation
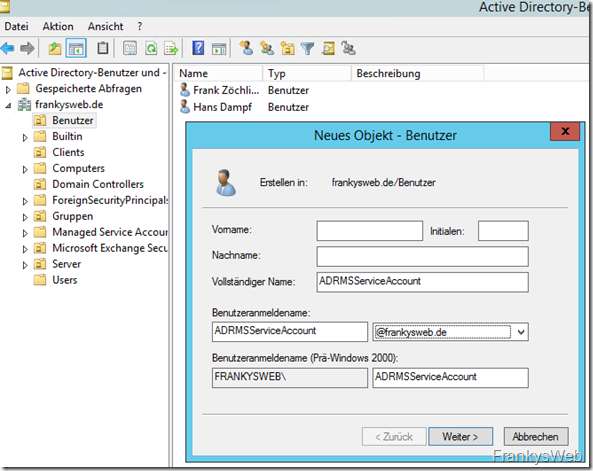
Only a few preparations are required to install the rights management services. A service account can be created in advance, which is used for RMS. The service account is a normal Active Directory user account:
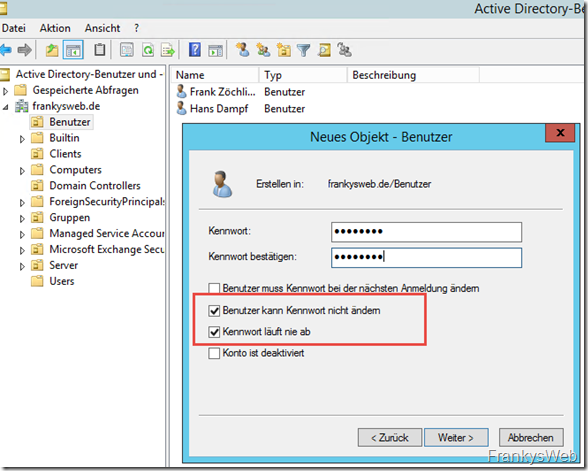
The only important thing is that the password must not expire:
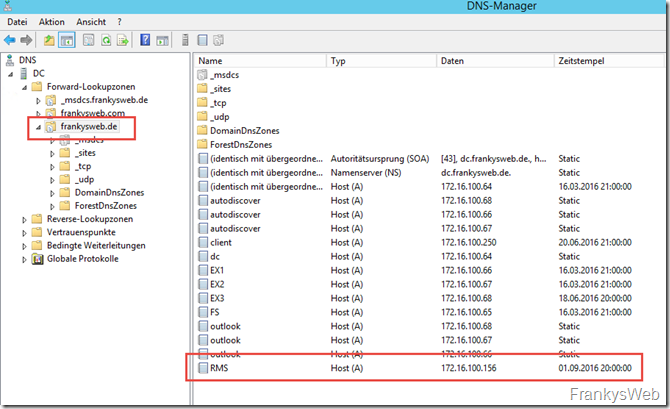
A DNS entry is also required if the RMS address is different from the server name. In my case, the RMS server is simply called "RMS" and my Active Directory is called "frankysweb.de". I therefore do not need to create a DNS entry, as the DNS entry is created automatically when the server is added to the AD:
For example, if the AD listens to "frankysweb.local", split DNS can be used. In concrete terms, this means that if the server name is rms.frankysweb.local, a DNS entry must be created with rms.frankysweb.de and the IP of the RMS server. A DNS name should be used here that can later also be accessed from the Internet.
A certificate is also required for the rights management services. During installation, a self-signed certificate can be installed for test environments. A valid certificate should be used for productive environments. A valid certificate is configured in the section "Intermediate step certificate for RMS". If you are only installing a test environment, you can also use a self-signed certificate at this point and skip this step.
Now the installation can begin.
Installation of Active Directory rights management services
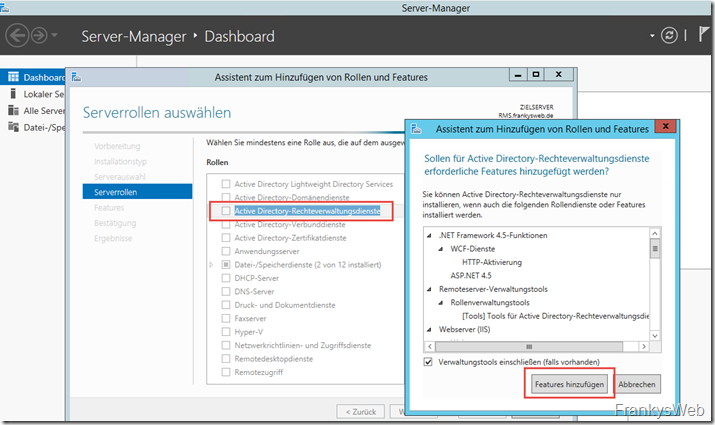
The installation of the rights management services can now be started via the Server Manager. The necessary additional features can also be installed directly:
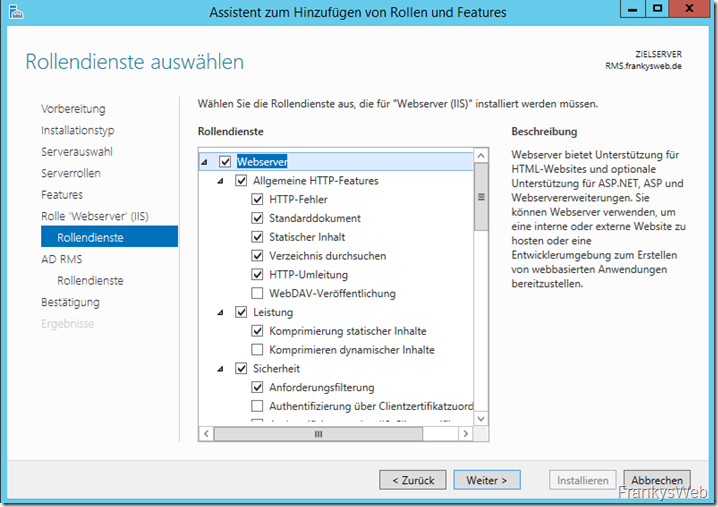
The Server Manager then automatically selects the required IIS services:
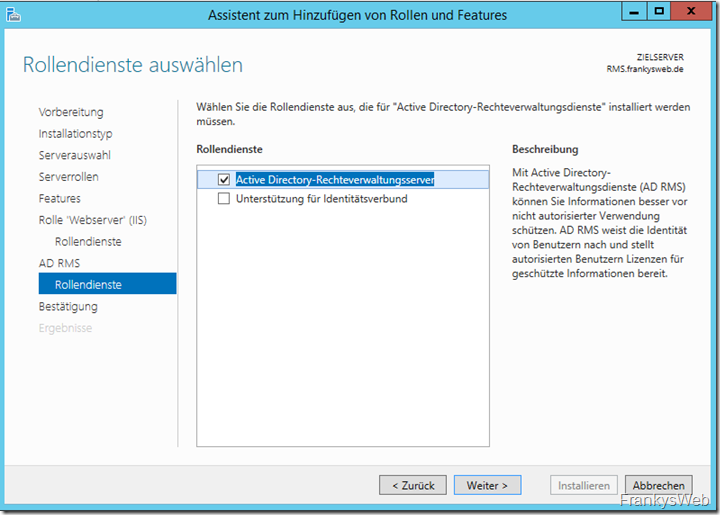
In the next dialog, only the "Active Directory rights management server" is selected.
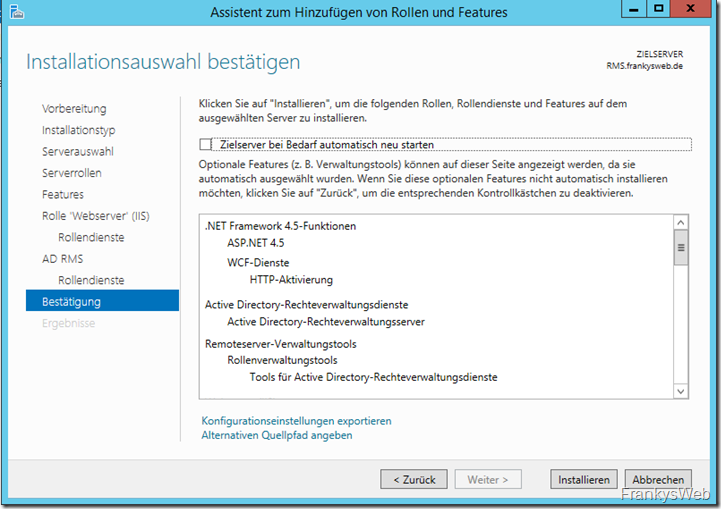
The final step is to install the roller:
Similar to a domain controller, the basic configuration must first be carried out after installing the role:
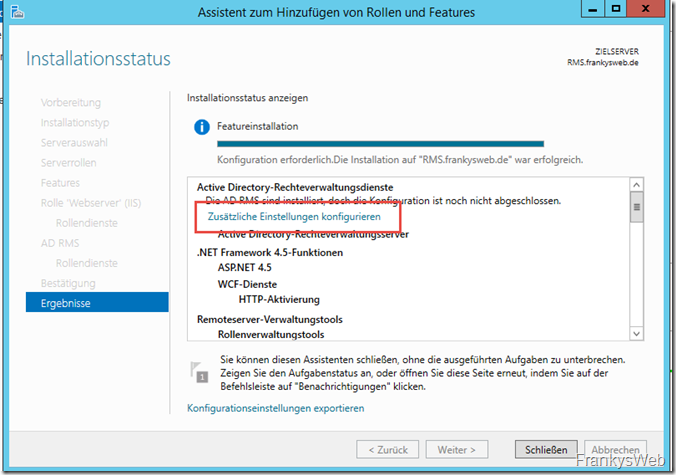
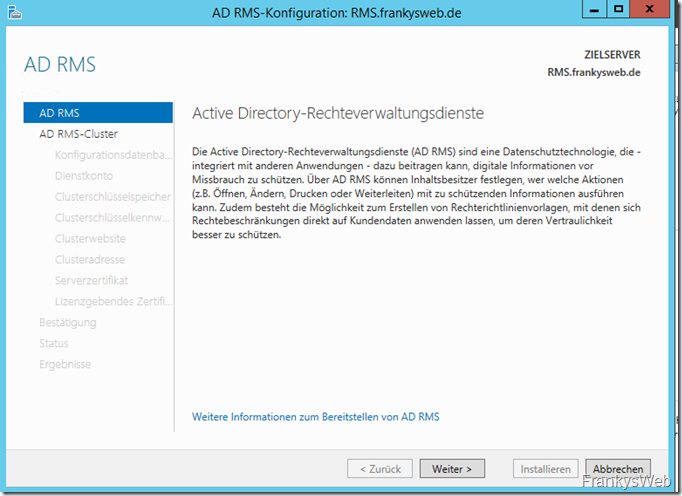
After clicking on "Configure additional settings", the wizard for AD RMS opens:
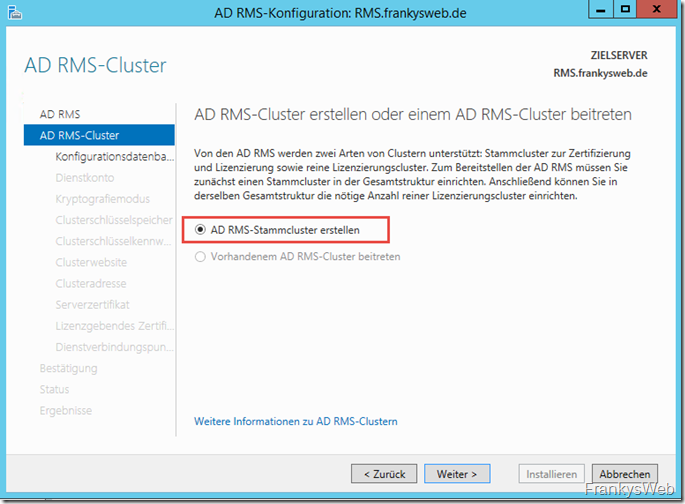
As the first AD RMS server is installed in this case, an AD RMS root cluster must be created:
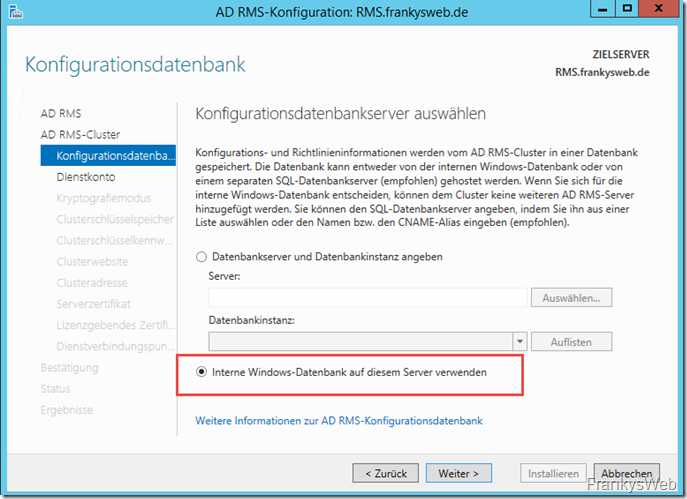
You can now select whether an SQL server should be used for the database or whether the Windows Internal Database should be used. In productive environments, an SQL database with the highest possible availability would be used at this point instead of the Windows Internal Database:
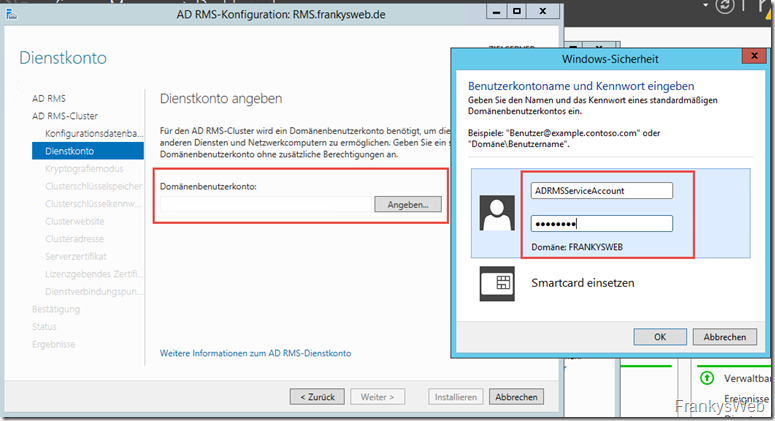
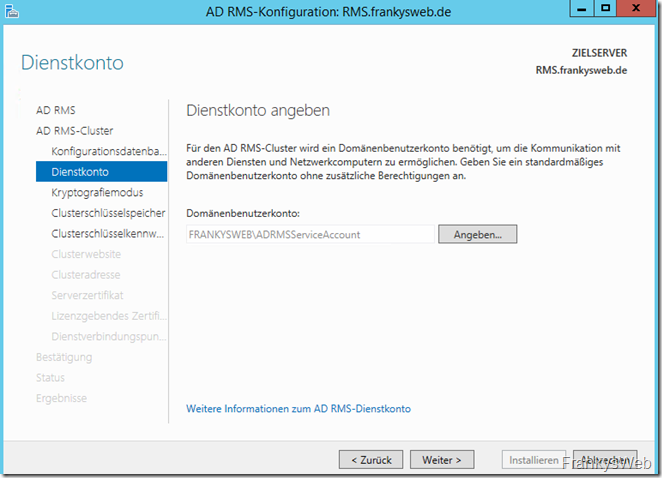
The user that was previously created during the preparations is specified for the service account. In this case "ADRMSServiceAccount":
Once the user has been specified, you can continue:
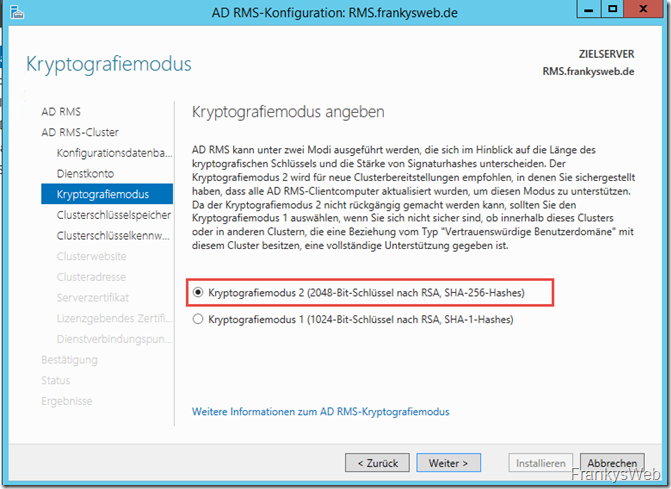
Cryptographic mode 2 (SHA256) is now selected. SHA1 should no longer be used:
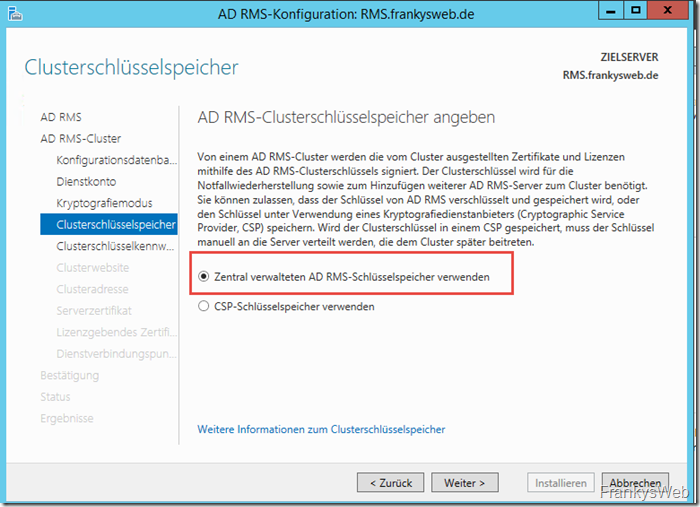
The "Use centrally managed AD RMS keystore" item is selected under "Cluster keystore":
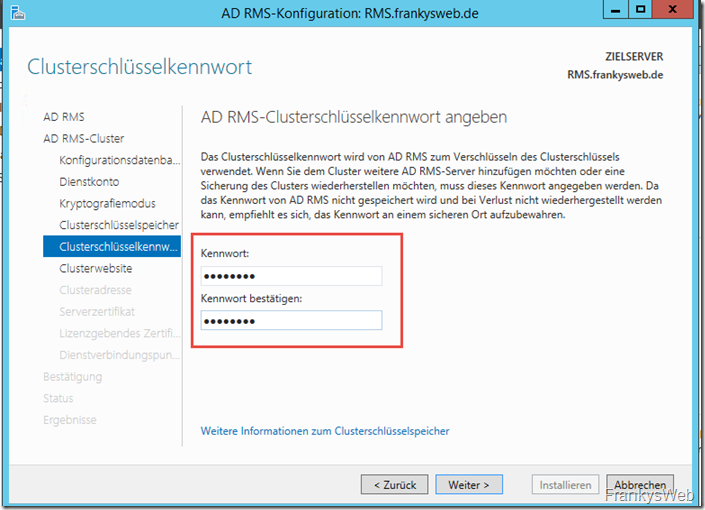
A password must be assigned for the cluster key:
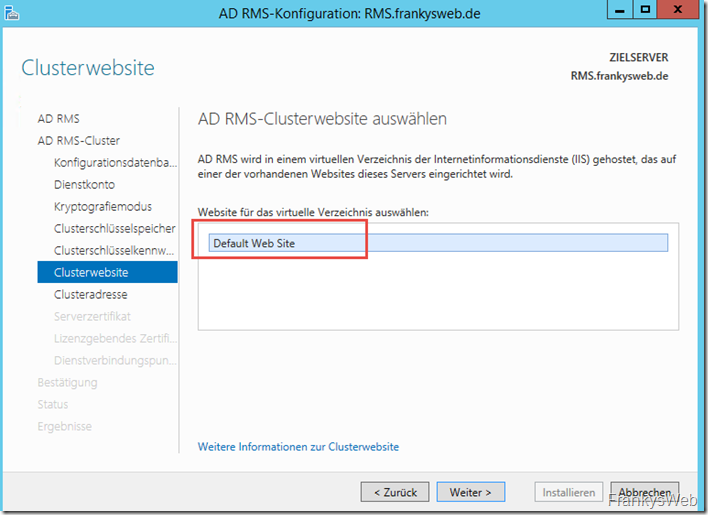
As the IIS has already been installed by the Server Manager, the "Default Web Site" can now be selected:
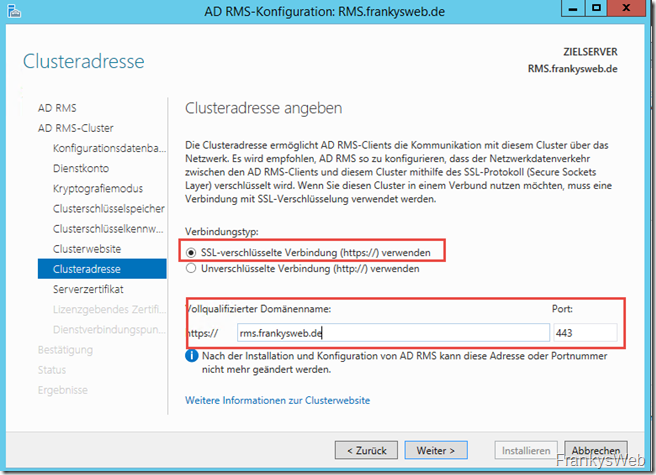
The address for RMS can now be defined. This should not be an internal server name, but an FQDN that can also be reached from the Internet. In my case, it is rms.frankysweb.de on port 443 (HTTPS). The DNS entry has already been created internally under the preparations:
As a certificate is required for HTTPS, either a self-signed certificate can be created in the next dialog or an intermediate step can be taken to configure a valid certificate. The next section can be skipped for test environments.
Intermediate step Certificate for RMS
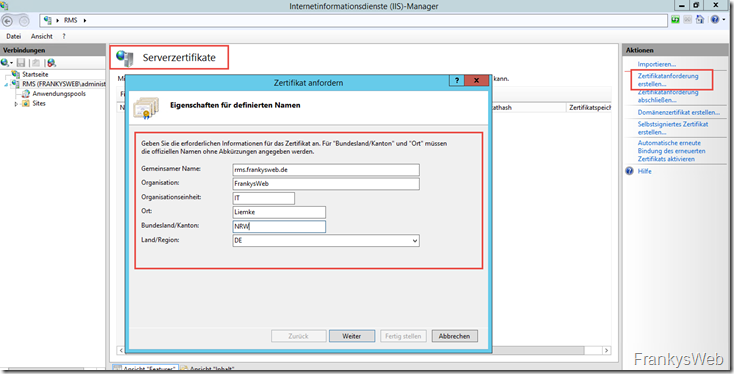
As the IIS has already been installed by the Server Manager, a certificate request can be generated using the IIS Manager:
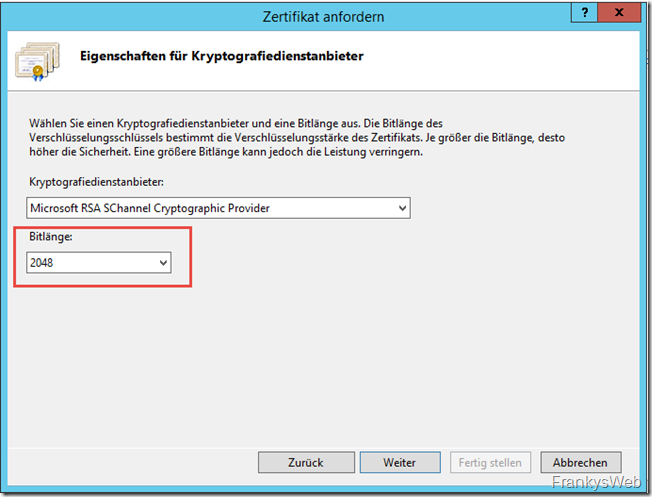
Important: All public CAs now use 2048-bit keys, 1024-bit keys are considered insecure:
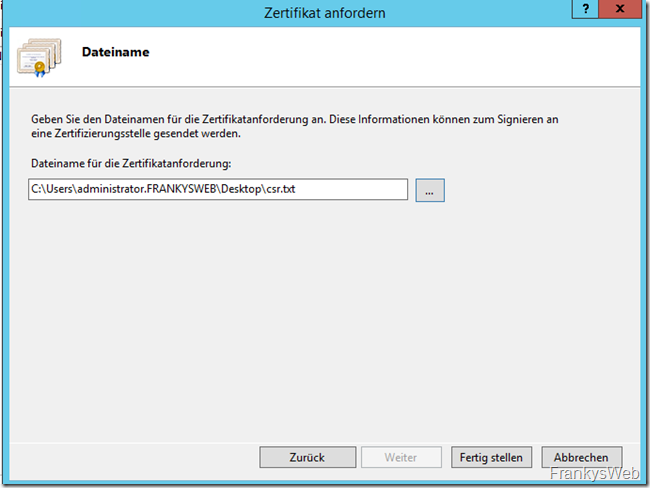
The CSR can now be saved and submitted to a CA of your choice. In my case, I used StartSSL. StartSSL issues a corresponding certificate with a term of 1 year free of charge:
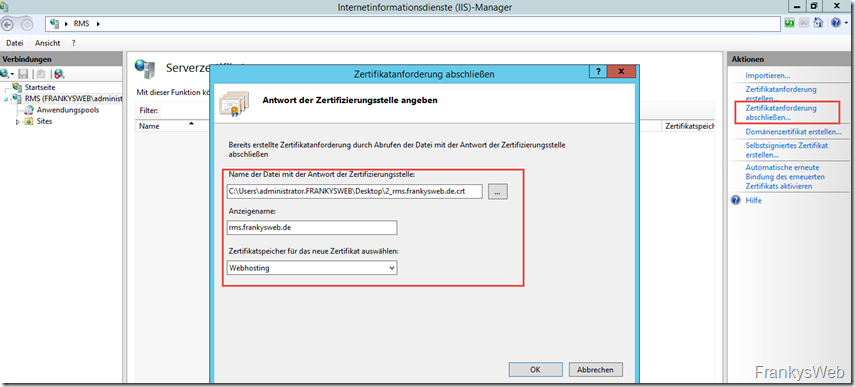
Once the certificate has been issued by the CA, the certificate request can be completed:
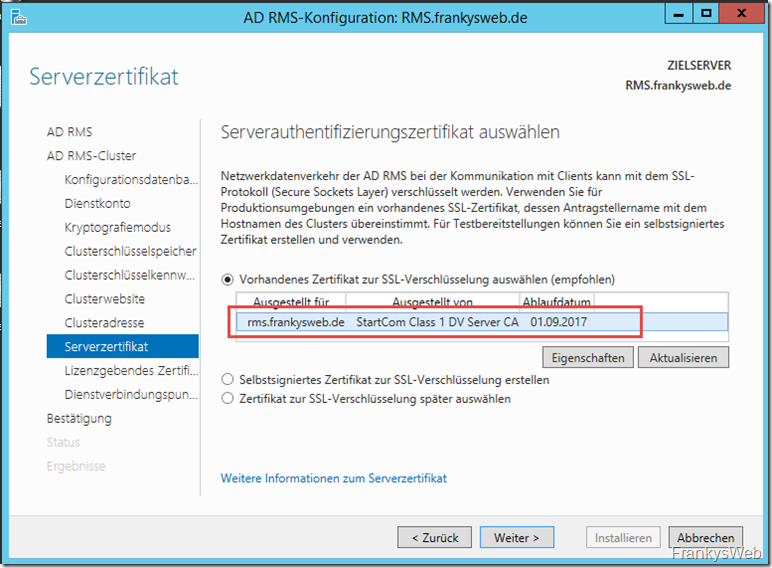
The certificate only needs to contain the name of the cluster address. The installation can now be continued.
Complete RMS installation
A certificate is required for client communication with the RMS server. I use a free certificate from StartSSL at this point. A self-signed certificate can also be used for test environments:
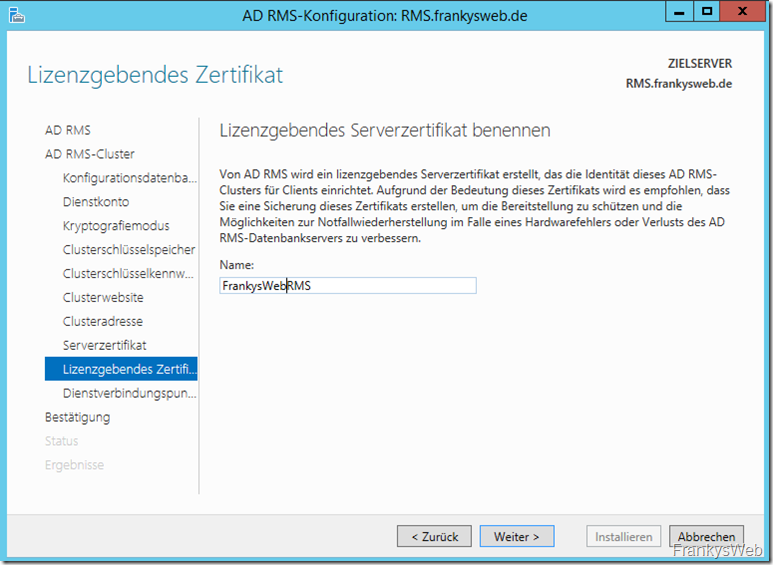
In addition, a licensing certificate is created, here only the name must be specified:
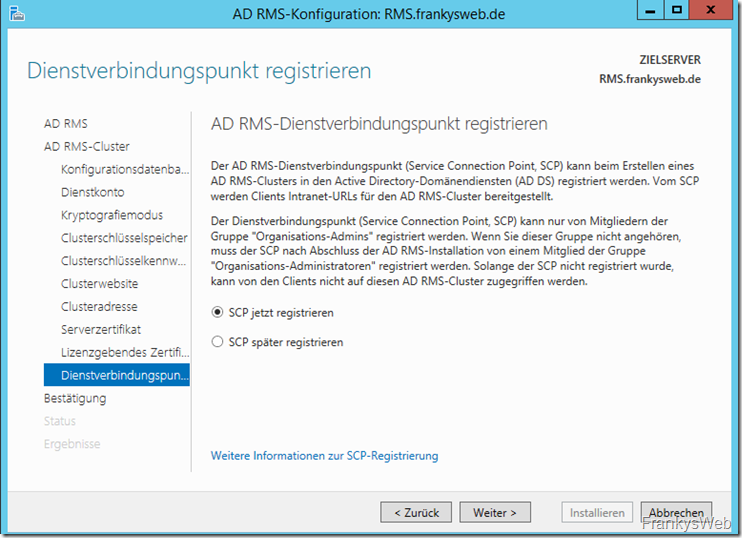
The SCP can be created automatically:
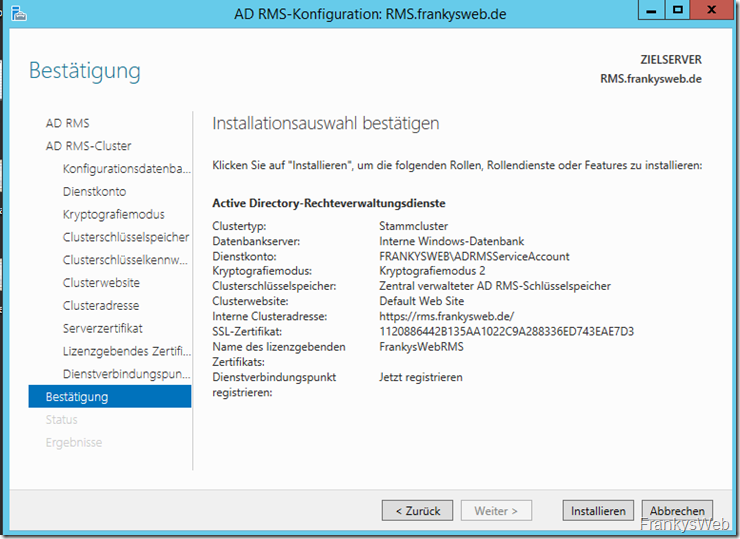
A summary is displayed in the last step. The installation can begin:
It takes a little while until RMS is installed:
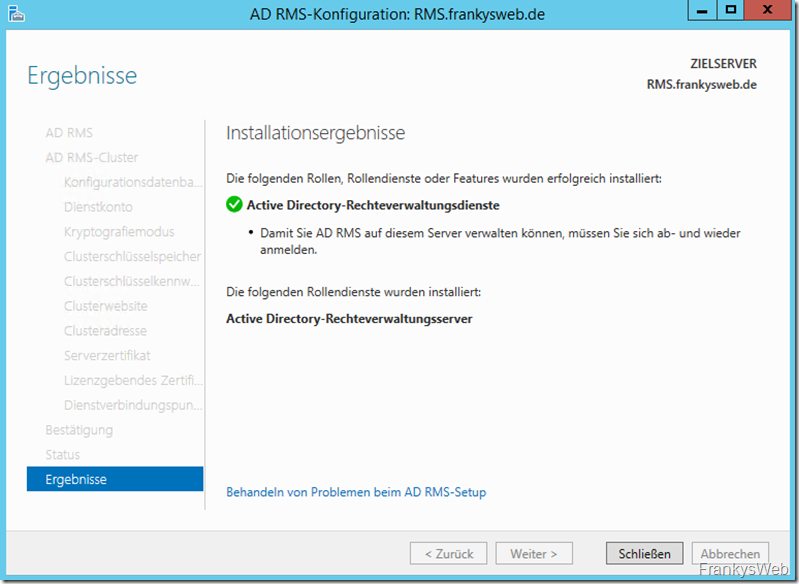
Finally, the installation result is displayed:
The installation is now complete. The next article is about the configuration.
Hallo Frank,
Danke für diesen Step by Step Guide.
Versuche die AD RMS Installation auf einem Domain Controller inkl. einer PKI und bereits installierten und konfigurierten AD FS Service.
Beim Punkt Serverauthentifizierungszertifikat auswählen erhalte ich folgende Warnung:
Für die ausgewählte Cluster-Url ist bereits eine SSL-Zertifikatanbindung vorhanden
IIS Bindung Default Website ist für Port 80 ohne Hostnamen und IP-Adresse mit *
Für https bestehen folgende Bindungen: adfs.xy.com mit IP-Adresse * ,sowie adrms.xy.com mit IP-Adresse *. Die entsprechenden öffentlichen Zertifikate sind jeweils hinterlegt.
Frage mich nun natürlich ob ich hier ohne zukünftige Probleme die Installation abschliessen kann?
Besten Dank für den Feedback.
Gruss, Markus