In part 1 of this article series the RMS server was installed and Part 2 found the configuration took place. Now the integration into Exchange 2016 follows.
A reminder of the surroundings from parts 1 and 2:
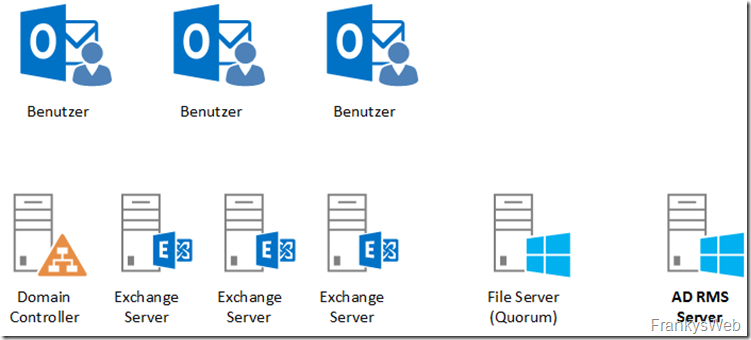
Surroundings
The environment in which the Active Directory rights management services are installed is as follows:
There are a few users with Outlook 2016, a domain controller, 3 Exchange servers (one DAG), a file server for the quorum and a Windows Server 2012 R2 that was installed in part 1 as a rights management services server.
The Active Directory is called frankysweb.de, the users use Windows 10 with Outlook 2016.
Preparation
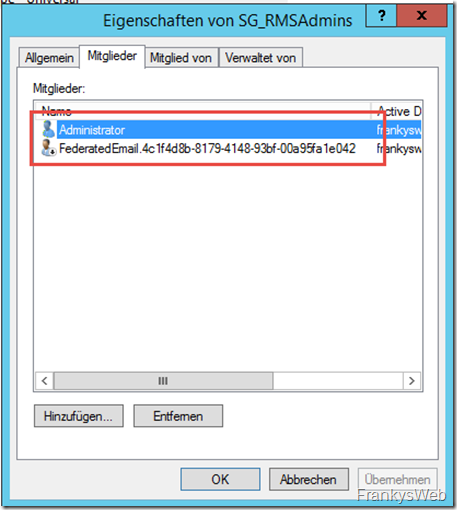
For the integration in Exchange 2016 to work, the Active Directory account of the system mailbox "FederatedEMail" must be a member of the RMS Admin group. In my case, I add the "FederatedEmail" account to the "SG_RMSAdmins" group:
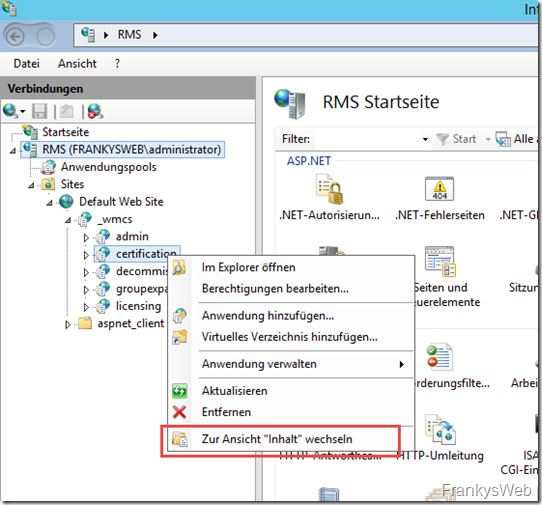
A few additional authorizations must then be assigned again. To do this, click on the "certification" application in the IIS Manager and switch to the content view:
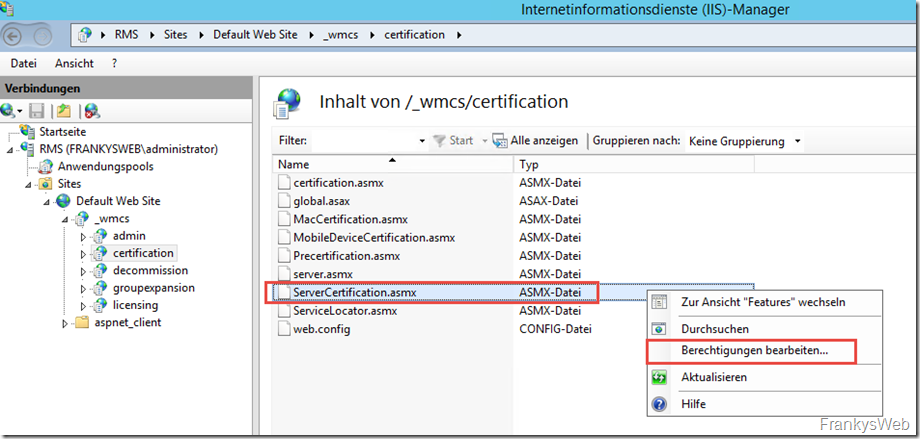
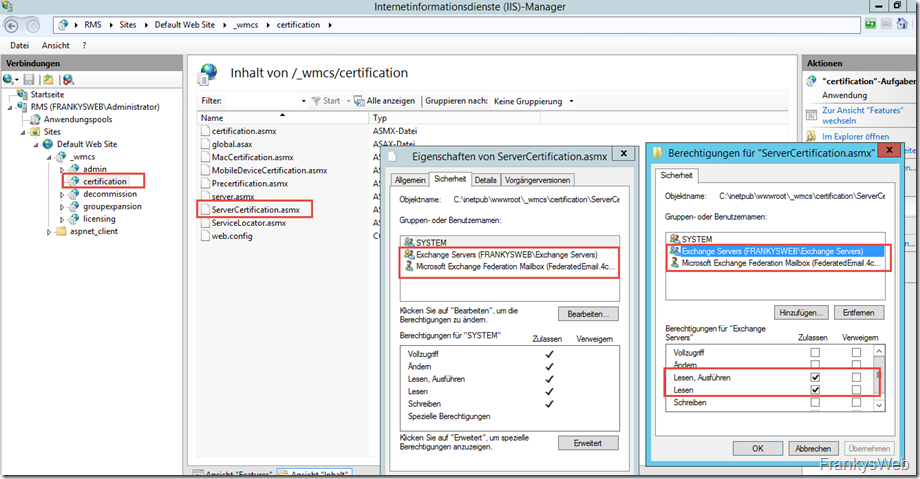
The authorizations for the ServerCertification.asmx file can now be edited:
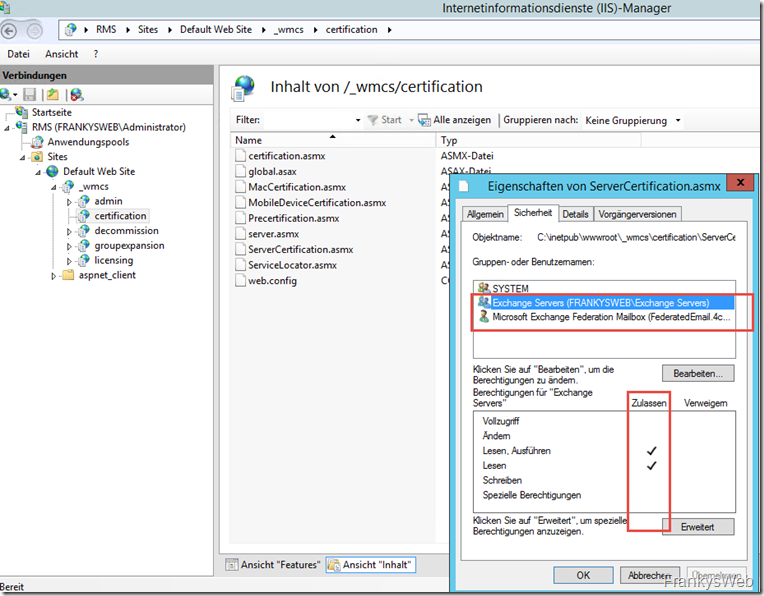
The "Exchange Servers" and "FederatedEmail" groups receive "Read" and "Read and execute" rights:
The authorizations should now look like this:
Continue with the integration in Exchange 2016
Integration RMS in Exchange 2016
AD RMS is referred to as IRM (Information Rights Management) within Exchange Server. The CMDLets and settings are therefore also labeled accordingly with IRM (Get-IRMConfiguration, Set-IRMConfiguration, etc.).
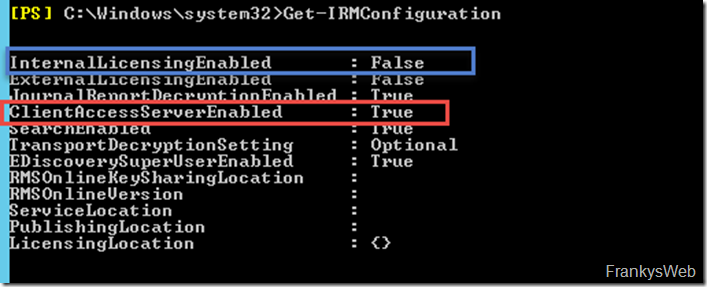
In the default setting, IRM is already switched on for the ClientAccessServer, as in many places "ClientAccessServer" is still a remnant from Exchange 2013, because ClientAccess and the mailbox role have been merged so that only the mailbox role still exists.
However, licensing, i.e. the issuing of licenses for documents, is deactivated in the default setting:
The following command can be used to switch on RMS for internal use:
Set-IRMConfiguration -InternalLicensingEnabled $true
Note: The first step here is to activate RMS internally. In order for it to also work with external recipients, i.e. recipients outside your own Acktive Directory, more is required.
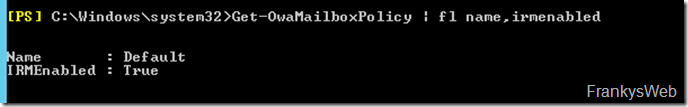
RMS (IRM) is also already activated for OWA:
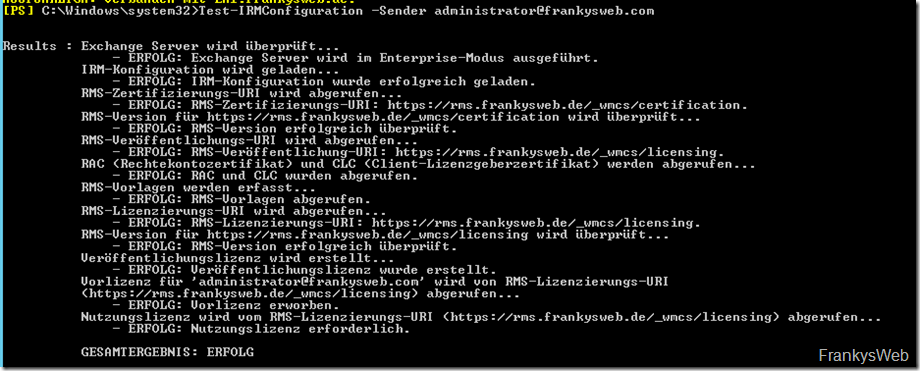
To make IRM available internally, only the "Set-IRMConfiguration" CMDLet needs to be executed first, after which testing can begin:
Test-IRMConfiguration -Transmitter <a href="mailto:administrator@frankysweb.com">administrator@frankysweb.com </a>
A success everywhere, it can be tested.
Outlook and OWA
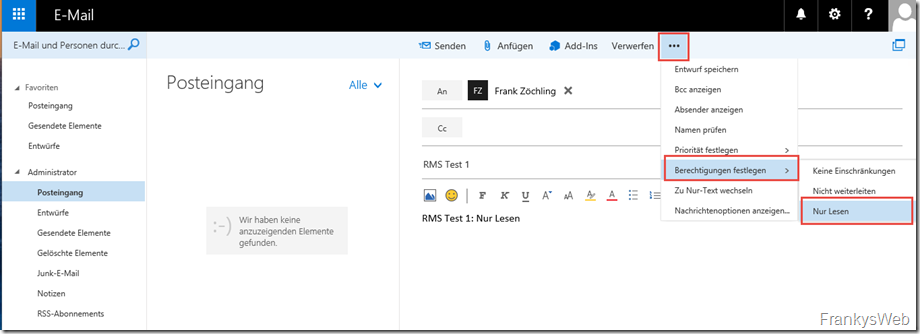
To test this, I create a new email in OWA, the "Set permissions" option is now displayed via the "3 dots" button. The "Read only" policy from part 2 is now visible here. The other two policies are standard Exchange policies:
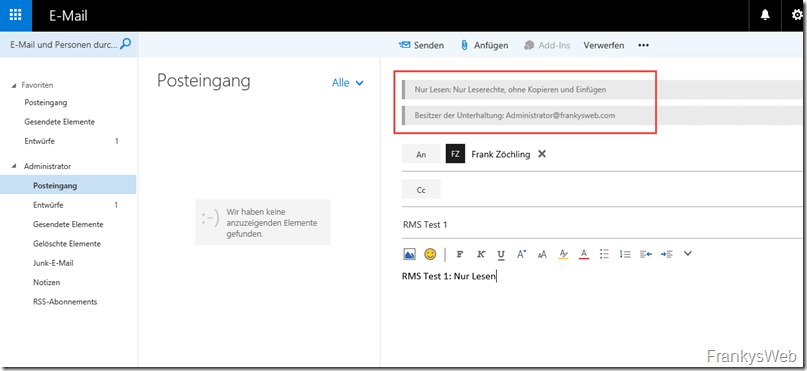
If "Read only" is selected, corresponding mail tips are displayed with the policy information. These were also configured in part 2:
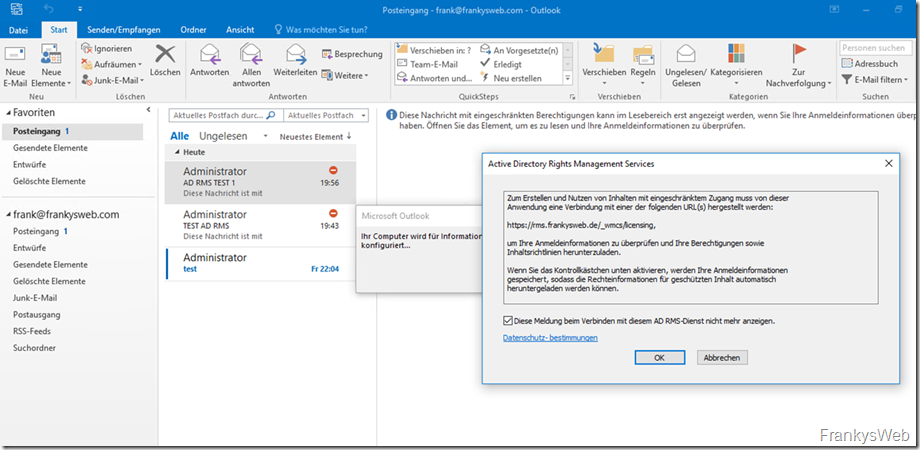
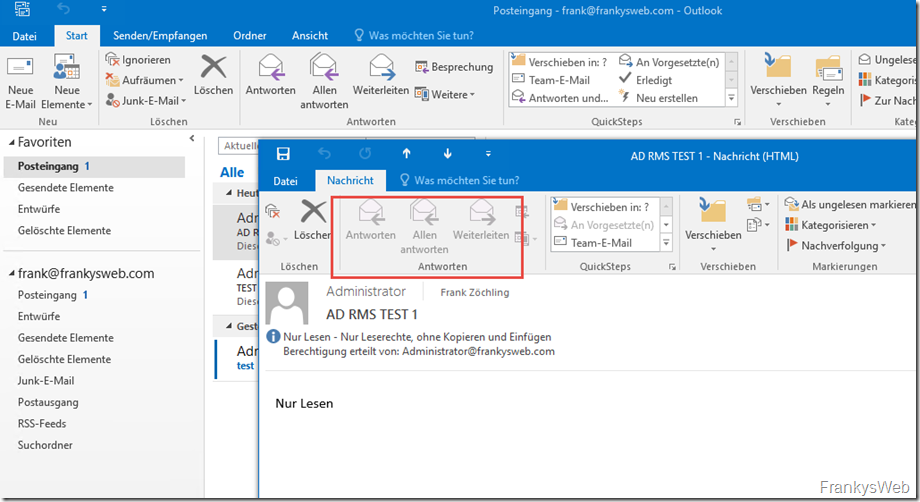
The mail is sent to an internal recipient with Outlook 2016. When the RMS-protected mail is opened, Outlook is first configured once for the use of AD RMS:
The mail can then be read, but the buttons for "Reply" and "Forward" are grayed out, as "Read only" has been defined in the policy.
Note: Try copying and pasting or taking a screenshot...
I have created a short video about this:
Hallo Frank,
erstmal vielen Dank für die Anleitung. Mit dieser Schritt-für-Schritt-Anleitung kommt man wirklich ans Ziel.
Jedem, der über die Fehler
FEHLER: Fehler beim Abrufen eines Rechtekontozertifikats (RAC) und/oder eines Clientlizenzgeberzertifikats (CLC).
In OWA sind die Vorlagen verfügbar, aber Mails werden nicht versendet..
stolpert:
Der Exchange-Server hat zwar alle Berechtigungen, allerdings erbt er diese über Berechtigungsgruppen erst nach einem Reboot. Ich habe mir lange den Kopf zerbrochen, aber Reboot tut gut. Danach ist das „Gesamtergebnis: Erfolg“
1. Opened the location C:inetpubwwwroot_wmcscertification
2. Select ServerCertification.asmx
3. Right click –>properties and click the Security tab.
4. Click the Edit button –> click the Add button –> set From this location field to the local server then type AD RMS Service Group
into the object names field –> then click the Check Names button. Click or
5. Add Read & execute and Read permissions.
6. Also make sure Exchange servers domain group is already added.
7. Did the same on all AD RMS servers
Now we ran the following cmd:
Test-IRMConfiguration –Sender AdminEmailID
Bei den Hinweisen wird erwähnt, dass RMS mit externen Empfängern mehr erfordert.
Leider habe ich bisher nicht herausgefunden, wie dieses „mehr“ zu schaffen ist. Geht es ohne Azure-Dienste?
Bei mir das gleiche allerdings sehe ich noch folgendes beim Test-IRMConfiguration:
Acquiring Rights Account Certificate (RAC) and Client Licensor Certificate (CLC) …
– FAIL: Failed to acquire a Rights Account Certificate (RAC) and/or a Client Licensor Certificate (CLC).
This failure may cause features such as Transport Decryption, Transport Protection Rules, Journal Report
Decryption, IRM in Outlook Web App, IRM in Exchange ActiveSync, and IRM Search to not work. Make sure that
the Exchange Servers Group is granted „Read“ and „Read & Execute“ rights on the ServerCertification.asmx and
Publish.asmx pipelines on your AD RMS server. For details, see „Set Permissions on the AD RMS Certification
Pipeline“ at http://go.microsoft.com/fwlink/?LinkId=186951.
—————————————-
Microsoft.Exchange.Security.RightsManagement.RightsManagementException: Failed to acquire server box RAC
from . —>
System.Web.Services.Protocols.SoapException: System.Web.Services.Protocols.SoapException: Exception of type
‚System.Web.Services.Protocols.SoapException‘ was thrown. —>
Microsoft.DigitalRightsManagement.Cryptography.UnsupportedCryptographicSetException: Exception of type
‚Microsoft.DigitalRightsManagement.Cryptography.UnsupportedCryptographicSetException‘ was thrown.
— End of inner exception stack trace —
at Microsoft.DigitalRightsManagement.Certification.BaseCertificationWebService.Certify(CAType caType,
CertifyParams requestParameters)
at Microsoft.DigitalRightsManagement.Certification.ServerCertificationWebService.Certify(CertifyParams
requestParams)
at System.Web.Services.Protocols.SoapHttpClientProtocol.ReadResponse(SoapClientMessage message,
WebResponse response, Stream responseStream, Boolean asyncCall)
at System.Web.Services.Protocols.SoapHttpClientProtocol.EndInvoke(IAsyncResult asyncResult)
at Microsoft.Exchange.Security.RightsManagement.SOAP.ServerCertification.ServerCertificationWS.EndCertify(
IAsyncResult asyncResult)
at Microsoft.Exchange.Security.RightsManagement.ServerCertificationWSManager.EndAcquireRac(IAsyncResult
asyncResult)
— End of inner exception stack trace —
at Microsoft.Exchange.Data.Storage.RightsManagement.RmsClientManager.EndAcquireInternalOrganizationRACAndC
LC(IAsyncResult asyncResult)
at Microsoft.Exchange.Management.RightsManagement.IRMConfigurationValidator.TryGetRacAndClc()
Weiss leider auch keinen Rat mehr und der Microsoft Support weiss auch nichts mehr….
Die Berechtigungen habe ich gesetzt, TechNet nachgesehen, Federated Postfach usw…
Alles nach Vorschrift gesetzt und er will nicht :(
hm, ich verzweifle gerade..
Ich habe die Konfiguration nachgestellt und bekomme unter Exchange 2016 immer dieselbe Fehlermeldung:
RAC (Rechtekontozertifikat) und CLC (Client-Lizenzgeberzertifikat) werden abgerufen…
– FEHLER: Fehler beim Abrufen eines Rechtekontozertifikats (RAC) und/oder eines Clientlizenzgeberzertifikats (CLC).
In OWA sind die Vorlagen verfügbar, aber Mails werden nicht versendet..