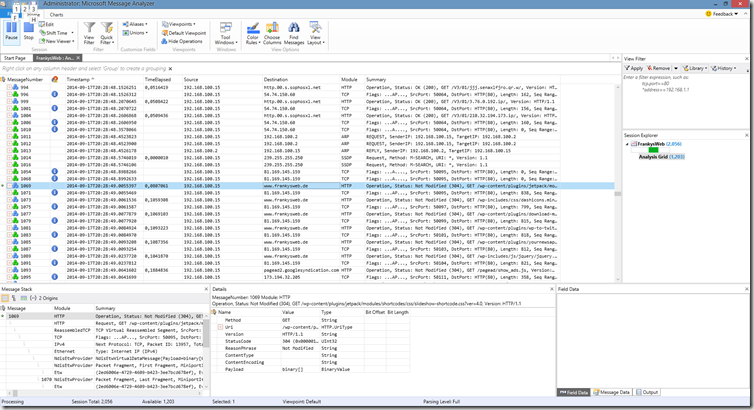
Message Analyzer is the successor to Network Monitor. Do not misunderstand: Message Analyzer is not used to analyze mails, but to see what is happening on the line, similar to Network Monitor or Wireshark.
The big advantage of Message Analyzer is that it can decrypt encrypted connections if the private key is available. This makes Message Analyzer a great tool for error analyzers. Among other things, of course, also for mail problems via encrypted connections.
Click here to download: