In this article I had already pointed out that Office 365 will only support TLS 1.2 from October 2018. However, before switching to the current TLS 1.2 version, the clients / servers with which the local Exchange server does not yet communicate via TLS 1.2 should be identified.
The following small script can be used to determine the TLS versions of the clients and servers that receive / send mails. The script evaluates the logs of the connectors and generates CSV files with the respective TLS version.
The path where the CSV files are saved must be specified in line 1. In line 2, the path to the SMTP connector logs must be specified (already pre-assigned for Exchange 2016):
$LogExportPath = "C:\Scripts\TLSVersion\"
$SMTPLogPath = "C:\Program Files\Microsoft\Exchange Server\V15\TransportRoles\Logs\FrontEnd\ProtocolLog"
write-host "Getting Logs"
$Logs = (Get-ChildItem $SMTPLogPath\*.log -Recurse| select Fullname).Fullname
$TLS12Log = "$LogExportPath" + "TLS12.csv"
$TLS11Log = "$LogExportPath" + "TLS11.csv"
$TLS10Log = "$LogExportPath" + "TLS10.csv"
foreach ($Log in $Logs)
{
write-host "Processing $Log"
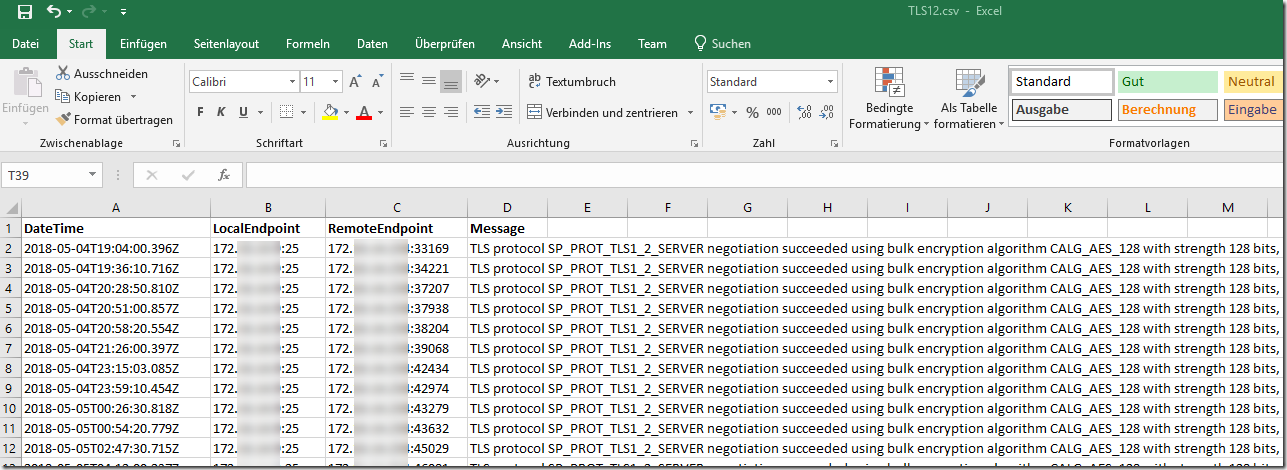
$LogImport = Get-Content -Path $Log | Select-Object -Skip 3 | Out-String | ConvertFrom-Csv | select -property @{N='DateTime';E={$_."#Fields: date-time"}}, @{N='LocalEndpoint';E={$_. "local-endpoint"}}, @{N='RemoteEndpoint';E={$_. "remote-endpoint"}}, @{N='Message';E={$_.context}}
$TLS12 = $LogImport | where {$_.Message -match "SP_PROT_TLS1_2" -and $_.Message -match "succeeded"} | export-csv $TLS12Log -append -delimiter ";"
$TLS11 = $LogImport | where {$_.Message -match "SP_PROT_TLS1_1" -and $_.Message -match "succeeded"} | export-csv $TLS11Log -append -delimiter ";"
$TLS10 = $LogImport | where {$_.Message -match "SP_PROT_TLS1_0" -and $_.Message -match "succeeded"} | export-csv $TLS10Log -append -delimiter ";"
}
write-host "Done"
write-host "For Hosts using TLSv1.2 see $TLS12Log"
write-host "For Hosts using TLSv1.1 see $TLS11Log"
write-host "For Hosts using TLSv1.0 see $TLS10Log"
The script searches the logs for the strings SP_PROT_TLS1_2, SP_PROT_TLS1_1 and SP_PROT_TLS1_0 and saves the entries found in the respective CSV files TLS12.csv, TLS11.csv and TLS10.csv, so that the results can be processed later:
Of course, the script is only meaningful if the Exchange itself receives and sends the mails from the Internet. This is unlikely to be the case in most cases, as an upstream AntiSPAM gateway is used, for example.
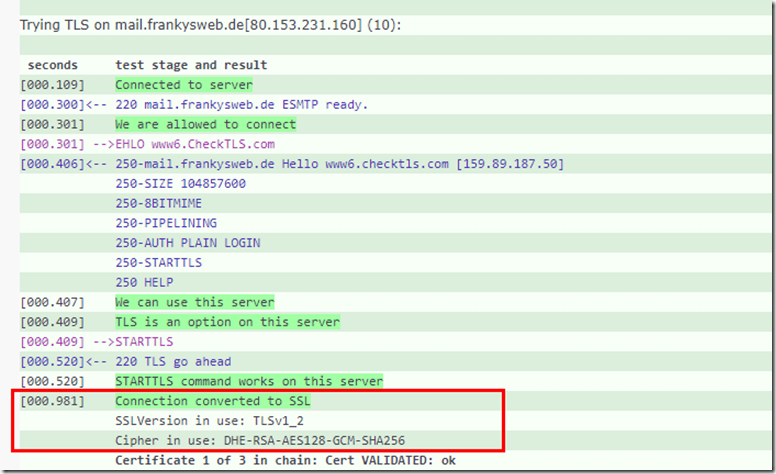
If the AntiSPAM Gateway does not show the TLS version used in the logs, the following test can help:
The test shows the TLS version used in the results, this provides information as to whether the gateway is able to receive mails via TLS 1.2:
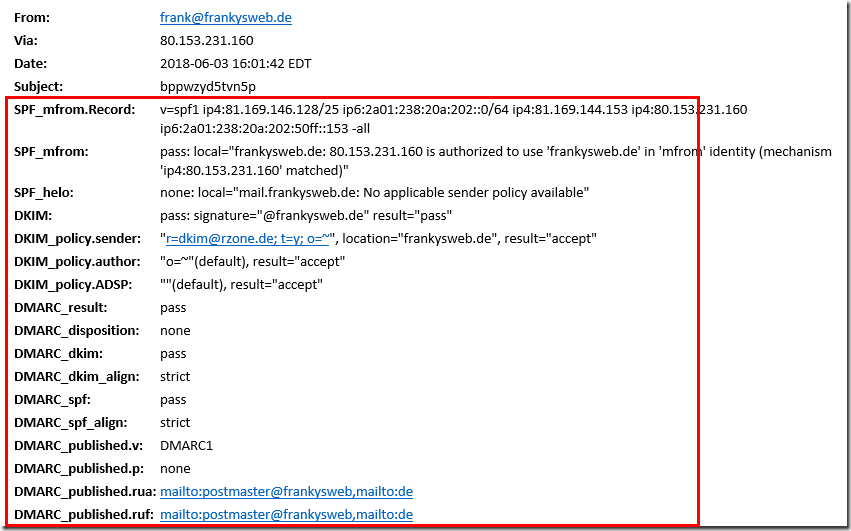
To avoid difficulties with Office 365 and the local mail servers, SPF, DKIM and DMARC should also be implemented accordingly. You can find out whether SPF, DKIM and DMARC are implemented accordingly by sending an email to the following test:
Bekomme bei dem Script leider folgenden Fehler.
export-csv : CSV-Inhalt kann nicht an folgende Datei angefügt werden: C:\Script\TLSVersion\TLS12.csv. Das angefügte Objekt hat keine Eigenschaft, die der folgenden Spalte entspricht: . Soll der Ablauf mit nicht übereinstimmenden Eigenschaften fortgesetzt werden, fügen Sie den Parameter „-Force“ hinzu, und wiederholen Sie den Vorgang.
In C:\Script\TLSCheck.ps1:12 Zeichen:103
+ … age -match „succeeded“} | export-csv $TLS12Log -append -delimiter „;“
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : InvalidData: (:String) [Export-Csv], InvalidOperationException
+ FullyQualifiedErrorId : CannotAppendCsvWithMismatchedPropertyNames,Microsoft.PowerShell.Commands.ExportCsvCommand
Hallo,
kann mir jemand die Quelle für die Voraussetzung von SPF, DKIM und DMARC nennen, ich finde leider keine Informationen dazu.
VG
Jürgen
Hier stimmt doch etwas im Skript nicht:
>>>>>
$TLS12Log = „$LogExportPath“ + „TLS12.csv“
$TLS11Log = „$LogExportPath“ + „TLS12.csv“
$TLS10Log = „$LogExportPath“ + „TLS12.csv“
<<<<<
Müssen die CSV-Dateien nicht ebenfalls die Versionen wiederspiegeln?
Gruß
WW
Hallo Wandrey,
vielen Dank für den Hinweis, ist korrigiert.
Gruß, Frank