Forefront TMG has now been discontinued and a replacement will have to be found sooner or later. There are now several manufacturers who are filling the gap left by Forefront TMG. I will test some promising solutions and publish a howto for each of them. Finally, there will be an article comparing the solutions and listing the pros and cons from my point of view. So much for the plan.
I have therefore created a standard test environment that I will use for all solutions. The test environment has a relatively simple structure:
There is a Windows Server 2012 R2 with the name DC1 on which the Domain Controller role and Outlook 2013 are installed. Exchange 2013 is also installed on Server 2012 R2. The Exchange servers have the names EX1 and EX2. This is always the starting point for all solutions.
I defined a few evaluation criteria in advance in order to be able to draw a conclusion later. Mind you, these are my own criteria, which probably say little about the quality of the individual products. But more on that later.
In part 5, we now come to the cheapest solution by far: Debian and HAProxy, both open source. Using Linux as a reverse proxy is nothing new, Sophos, Kemp, F5 etc. are all based on a Linux foundation. Hence the open source variant for the price-conscious admin ![]()
Let's see how it performs. As usual, the customized test environment again:
So I have created a new VM with Debian 7 (Netinst, only the OS) I have only installed the VMware tools and assigned a fixed IP. That's all. The installation including the VMware Tools took about 30 minutes.
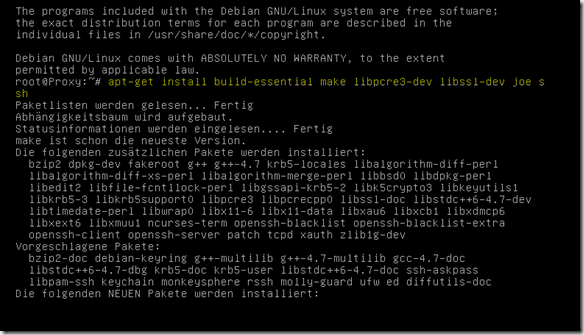
As soon as the Debian is installed and has received an IP, the prerequisites can be installed:
apt-get install build-essential make libpcre3 libpcre3-dev libssl-dev joe ssh
"Joe" is my favorite editor, of course any other editor is also suitable, such as Vi or Nano, I only install the SSH package so that I can manage the VM via SSH, it is not necessary.
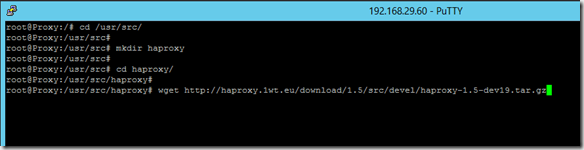
As soon as the packages have been installed, I create a new directory and download HAProxy:
cd /usr/src/
mkdir haproxy
cd haproxy/
wget http://haproxy.1wt.eu/download/1.5/src/devel/haproxy-1.5-dev19.tar.gz
The next step is to unpack the archive
tar -xvzf haproxy-1.5-dev19.tar.gz
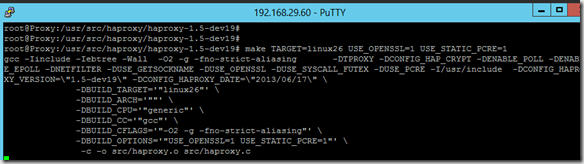
And then compiled
make TARGET=linux26 USE_OPENSSL=1 USE_STATIC_PCRE=1
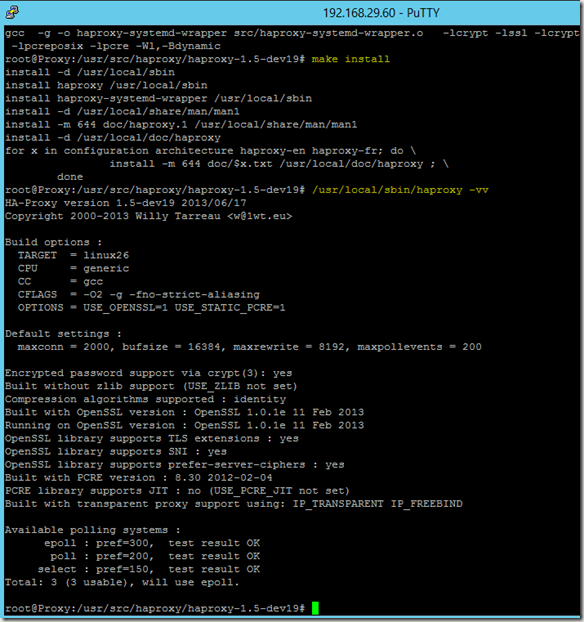
Once the package has been compiled, it can be installed with the following commands
make install
/usr/local/sbin/haproxy -vv
A start script is required so that HAProxy is loaded when the operating system is started. Now the editor "Joe" (or the editor of your choice) is used:
joe /etc/init.d/haproxy
The command creates a new file in the directory /etc/init.d. The following content can be inserted using copy and paste. Adjustments are not necessary:
#!/bin/sh
# /etc/init.d/haproxyPATH=/bin:/usr/bin:/sbin:/usr/sbin
pidfile=/var/run/haproxy.pid
binpath=/usr/local/sbin/haproxy
options="-f /etc/haproxy/haproxy.cfg"test -x $binpath || exit 0
case "$1" in
start)
echo -n "Starting HAproxy"
$binpath $options
#start-stop-daemon -start -quiet -exec $binpath - $options
echo "."
;;
stop)
echo -n "Stopping HAproxy"
kill `cat $pidfile`.
#start-stop-daemon -stop -quiet -exec $binpath -pidfile $pidfile
echo "."
;;
restart)
echo -n "Restarting HAproxy"
#start-stop-daemon -stop -quiet -exec $binpath -pidfile $pidfile
kill `cat $pidfile`.
sleep 1
$binpath $options
echo "."
;;
*)
echo "Usage: /etc/init.d/haproxy {start|stop|restart}"
exit 1
esacexit 0
Now the authorizations for the script must be adjusted, then the start configuration can be updated:
cd /etc/init.d
chmod +x haproxy
update-rc.d haproxy defaults
The path for the configuration file can now be created
mkdir /etc/haproxy
cd /etc/haproxy/
The certificate for the virtual service is now stored in the "/etc/haproxy" directory. The certificate must be in PEM format. I use my wildcard certificate from part 4. Windows cannot export certificates directly into the PEM format, but there are online services that can do this, or you can convert the PFX format into the PEM format with OpenSSL. You can find an online service here:
https://www.sslshopper.com/ssl-converter.html
I create the file "proxy.pem"
joe proxy.pem
And copy my certificate in PEM format into the file. HAProxy expects the private key first, so the order of the "Private Key" and "Certificate" blocks may have to be changed after conversion to PEM format. In my case, the content of the "proxy.pem" file looks like this:
--BEGIN PRIVATE KEY--
MIIEvwIBADANBgkqhkiG9w0BAQEFAASCBKkwggSlAgEAAoIBAQC9ztT1wfXB4q9x
Fliku9hSypzhqniJnuPOPhU6eWSNaE+fFAExpHRsxswQ5fUvYda/SyFKrifObiW/
<snip>
lqxeTvT7wje1xC0i+zdE1qzeQIUaM10HiZ7qMTKUszuaGtPEqLixboNNPGTTk+EE
PdJ0mlf4fzlaWL7Hoyrx8eESvcfPKkUkQ3TibgQJSs3iQT24eVX3xRd5LrFTi52c
5urvkjJYAVZwK54siKK2UiUm5w==
--END PRIVATE KEY--
--BEGIN CERTIFICATE--
MIIGXzCCBUegAwIBAgITbAAAAA2h0EEH1sCQ3AAAAAAADTANBgkqhkiG9w0BAQUF
ADBLMRUwEwYKCZImiZPyLGQBGRYFbG9jYWwxGjAYBgoJkiaJk/IsZAEZFgpmcmFu
<snip>
0pIVjEX/lcVYXr9M5yRAx6GRnoey3Hcpsl/bXU3nXNwU4rDv4LikOprn7Ekdsutj
pB+a
--END CERTIFICATE--
--BEGIN CERTIFICATE--
MIIDcTCCAlmgAwIBAgIQEIssKWSPtKpA5a1u5my3MzANBgkqhkiG9w0BAQUFADBL
MRUwEwYKCZImiZPyLGQBGRYFbG9jYWwxGjAYBgoJkiaJk/IsZAEZFgpmcmFua3lz
<snip>
EuIYUsfGlCd5OoakwC52bYXvekaXeCJNN1fSxUSmGIWyezdy80m09J8OBAxkPexy
lhcd/r70BKBzs5ohipZ2AM98U68V
--END CERTIFICATE--
The configuration file can now also be created in the "/etc/haproxy" directory:
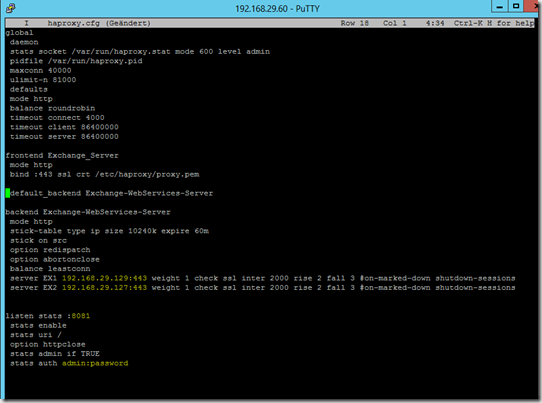
joe haproxy.cfg
My "haproxy.cfg" has the following content, the parts marked in blue must be adapted to the corresponding environment:
global
daemon
stats socket /var/run/haproxy.stat mode 600 level admin
pidfile /var/run/haproxy.pid
maxconn 40000
ulimit-n 81000
defaults
mode http
balance roundrobin
timeout connect 4000
timeout client 86400000
timeout server 86400000frontend Exchange_Server
mode http
bind :443 ssl crt /etc/haproxy/proxy.pem
default_backend Exchange-WebServices-Serverbackend Exchange-WebServices-Server
mode http
stick-table type ip size 10240k expire 60m
stick on src
option redispatch
option abortonclose
balance leastconn
server EX1 192.168.29.129:443 weight 1 check ssl inter 2000 rise 2 fall 3 on-marked-down shutdown-sessions
server EX2 192.168.29.127:443 weight 1 check ssl inter 2000 rise 2 fall 3 on-marked-down shutdown-sessions
listen stats :8081
enable stats
stats uri /
option httpclose
stats admin if TRUE
stats auth admin:password
The entries after "Server" represent the Exchange servers, EX1 and EX2 are only "display names", the servers are addressed via the IP.
Behind "listen stats" a port is required for a simple status and maintenance interface. I have set the graphical interface to port 8081, the port is freely selectable as long as it is not 443 ![]()
"Stats auth" expects the user name and password for the user of the graphical user interface.
The configuration is now complete. The service can be started with the following command:
service haproxy start
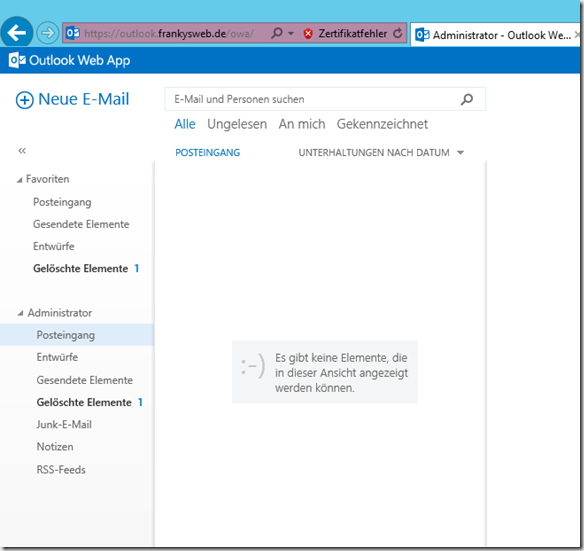
Here is a screenshot of the graphical user interface:
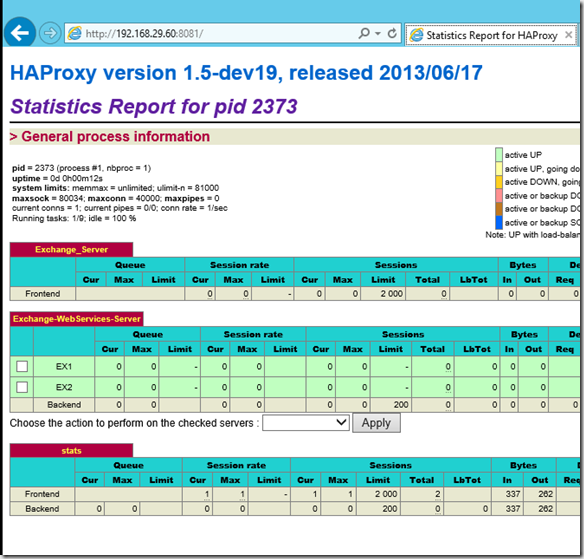
and OWA also works:
So the basis is running, I'm now playing around a bit and maintaining my table, I think the solution has potential. Let's see what we can do with it...
HAProxy lässt sich unter Debian Jessie sehr viel einfacher per „apt-get install haproxy“ über das Repository installieren und muss nicht extra kompiliert werden. Ein Initskript ist auch dabei, sodass nur noch das Zertifikat eingerichtet und die Konfiguration angepasst werden muss.
Hi Frank, ich bin scheinbar zu blöd und bekomme es nicht hin.
Entweder werden alle Anfragen nach dem / an den Exchange weitergegeben (also auch die IIS Startseite) oder ich bekomme Fehlermeldungen zur Konfig.
Mein Ansatz war je ein Frondend pro URL anzulegen und darin die entsprechende ACL zu definieren. Also so:
# Weiterleitung für OWA URL
frontend Exchange_Server_OWA
mode http
bind :443 ssl crt /etc/haproxy/Exchange_Zertifikat_haproxy.pem
default_backend Exchange-Nirvana
acl is_owa path_beg /owa
use_backend Exchange_OWA if is_owa
# Weiterleitung für Autodiscover URL
frontend Exchange_Server_Autodiscover
mode http
bind :443 ssl crt /etc/haproxy/Exchange_Zertifikat_haproxy.pem
default_backend Exchange-Nirvana
acl is_autodiscover path_beg /autodiscover
use_backend Exchange_Autodiscover if is_autodiscover
# Backends
backend Exchange_Autodiscover
mode http
stick-table type ip size 10240k expire 60m
stick on src
option redispatch
option abortonclose
balance leastconn
server ex2010.testdom.local 192.18.0.210:443 weight 1 check ssl inter 2000 rise 2 fall 3 on-marked-down shutdown-sessions
backend Exchange_OWA
mode http
stick-table type ip size 10240k expire 60m
stick on src
option redispatch
option abortonclose
balance leastconn
server ex2010.testdom.local 192.18.0.210:443 weight 1 check ssl inter 2000 rise 2 fall 3 on-marked-down shutdown-sessions
# Anfragen auf allen anderen URLs ins Nirvana leiten
backend Exchange-Nirvana
mode http
stick-table type ip size 10240k expire 60m
stick on src
option redispatch
option abortonclose
balance leastconn
server Nirvana 172.17.0.1:443 weight 1 check ssl inter 2000 rise 2 fall 3 on-marked-down shutdown-sessions
Der HAProxy kann so aber offenbar kein BIND bei den anderen Backends machen, da die auf die gleiche IP verweisen.
Es wäre echt gut, dass hinzubekommen, da gerade für kleinere Umgebung ein Balancer wie KEMP ( der sehr gut funktioniert) etwas Overkill ist.
Hallo Frank,
danke für die schnelle AW. Leider ist das mein Problem. Ich habe keine Ahnung, wie ich das in die Konfig. bekommen. Hatte mich schon mit der Verwendung von „acl“ versucht, jedoch ohne Erfolg.
Ich bin also für jeden Hinweis offen.
Danke, Sven
Hi, ACL ist schon der richtige Weg, hier gibt es ein Beispiel:
http://serverfault.com/questions/306968/haproxy-route-requests-based-on-url-substrings
Du musst die Backends und Frontends dann entsprechend der Exchange vDirs anlegen, bzw eben ins leere laufen lassen oder umleiten.
Hallo Sven,
ja, das lässt sich machen, du müsstest dann mehrere Front End und Backend Server anlegen und die jeweils auf eine URI laufen lassen. Ich meine im Netz gibt es genug Anleitungen dazu, im Prinzip ist das alles gleich :-)
Gruß, Frank
Hallo Frank,
super Anleitung bzw. Serie. Eine Frage hätte ich noch.
Kann man den Zugriff auf die Website snoch weiter einschränken in der HAProxy Konfig?
Mit dieser Konfig sidn ja alle Websites des Exchange inkl. der IIS Startseite erreichbar. Das muss ich vermeiden bzw. möchte ich nur Website sfür OWA und EAS veröffentlichen.
Danke und VG
Sven