The DXXD ransomware apparently attacks Windows servers directly. Like other ransomware, DXXD encrypts files and appends the extension .dxxd to the encrypted file.
Until now, an attack on Windows Server usually started from an infected client, which then encrypted files on network drives. In the forum of Bleeping Computer However, it is suspected that brute force attacks are being carried out on the RDP service in order to infect the servers directly.
Whether RDP is actually used is still unclear at present. However, I would like to take this opportunity to point out that RDP must not be directly accessible on the Internet. Unfortunately, I know some people who use a simple port forward to access servers quickly.
It would be much better to configure a VPN, even the cheapest router supports this and is still better than making RDP directly accessible on the Internet. And no: changing the port from 3389 to anything else makes no difference.
A policy that blocks accounts after a certain number of incorrect passwords is also not a good idea. In the worst case scenario, a brute force attack could result in quite a few accounts all being blocked.
Much better: VPN with 2-factor authentication. At least that's my opinion on the subject. RDP is a nice way to manage servers within your own network, but not suitable for remote maintenance from the Internet. Nobody would think of making their management interfaces (vSphere, iLO, DRAC etc.) directly accessible from the Internet. Or would they? Does anyone feel addressed? If so, finding such interfaces on the Internet is as easy as finding this website, just enter "iLO" or "vSphere" as a search term here: https://www.shodan.io
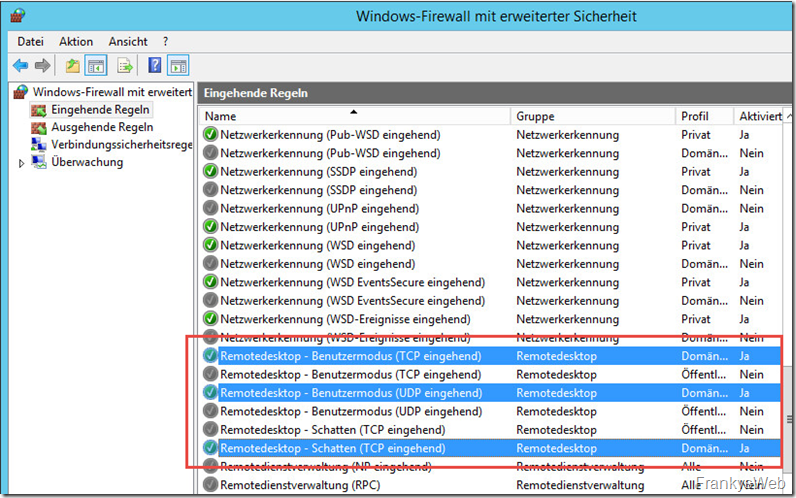
Anyway, I digress. So don't make RDP accessible on the Internet. Period. Even in the internal network, RDP should not be accessible to everyone, but should be restricted accordingly. This can be done quickly with the Windows firewall by searching for the appropriate rule:
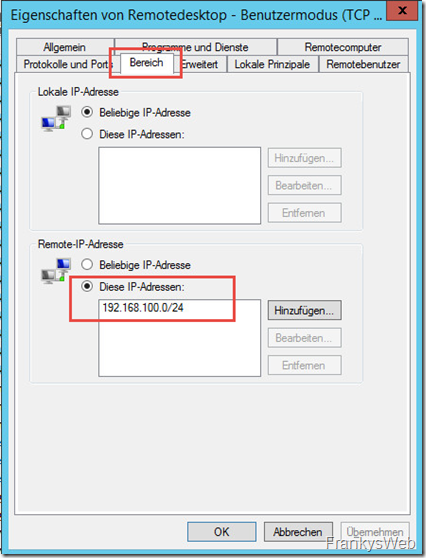
And in the "Range" tab, specify a subnet, range or IPs that are allowed to use RDP:
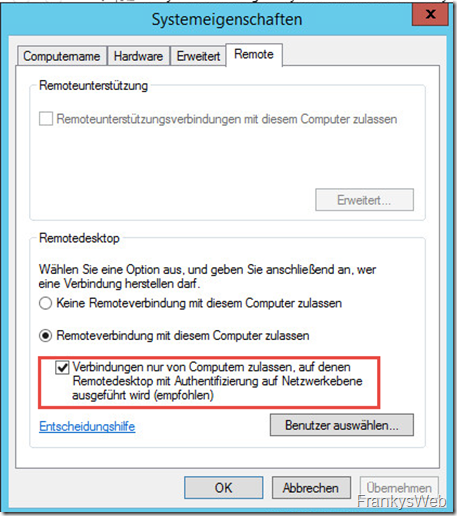
Also important: Please do not remove the small tick here:
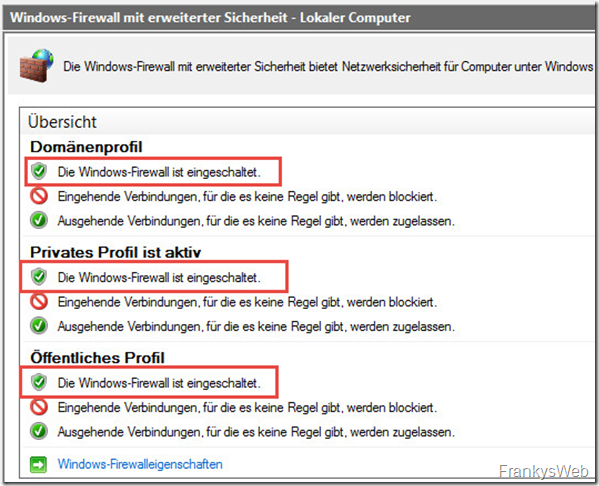
And the following always applies to the Windows Firewall:
Always!
Hallo Frank,
guter Hinweis :-)
Was mich wundert, auf meinem Server 2012 R2 habe ich die o.g. Einstellung übernommen. Das ist mein HyperV Host.
Auf diesem läuft ein 2012 DC und ein 2012 + Exchange 2016 in einer HyperV VM.
Bei den letzteren Servern sind die o.g. eingehenden Regel im Default gar nicht aktiviert (grün).
Sie sind ausgeschaltet und grau.
Ist das in einer HyperV Umgebung so gewollt oder warum sind die Regeln nicht aktiviert?
Grüße
Martin
ergänzend zu Deinem Beitrag sei erwähnt, dass das Publishing von RDP (User und ggf. Admin) via Remotegatway Server auch als sicher gilt und nicht schwer einzurichten ist.