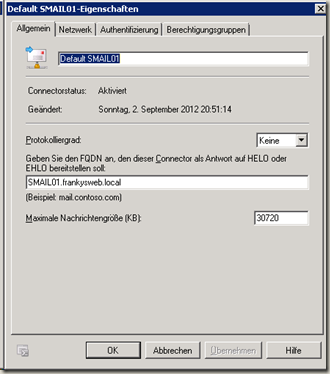
Today, for the first time in a long time, I came across an Exchange server that was configured as an open relay. I actually thought that such configuration errors were a thing of the past. Apparently, however, some people are still making this nasty mistake, so here are the default settings of the receive connectors so that the settings can be corrected.
By default, there are 2 connectors with the names "Default SERVERNAME" and "Client SERVERNAME". The default connector is responsible for all mail traffic from the Internet to the Exchange Server
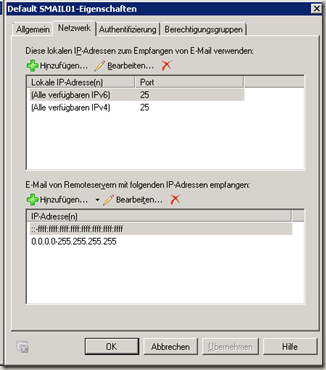
The default connector has therefore entered all IPv4 and all IPv6 addresses as remote servers:
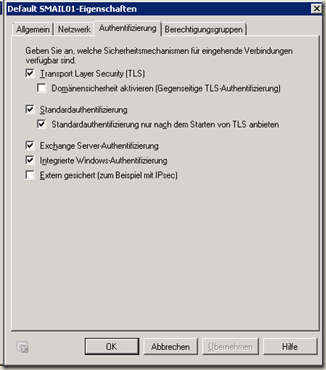
Here are the authentication methods in the default setting
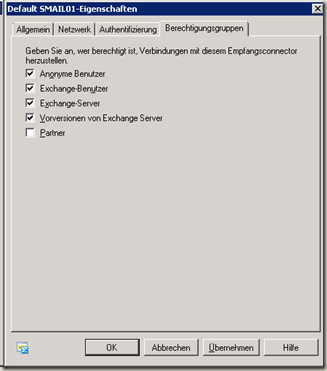
And here are the authorization groups
Only on the default connector is the "Anonymous users" box checked, mail servers from the Internet will not authenticate themselves to Exchange Server if they want to get rid of a mail.
The second receive connector is the client connector, which is responsible for the users' mail traffic to the Exchange Server.
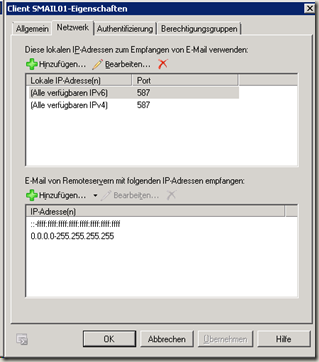
The Client Connector does not listen on port 25 but on port 587. Here too, all IPv4 and IPv6 addresses are permitted in the standard setting; this can be restricted to the local subnets if desired
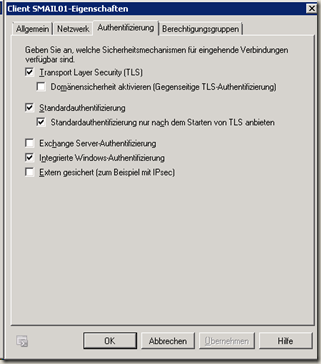
Here are the authentication methods
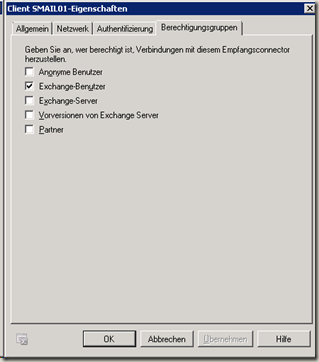
And here are the authorization groups for which only "Exchange user" is selected.
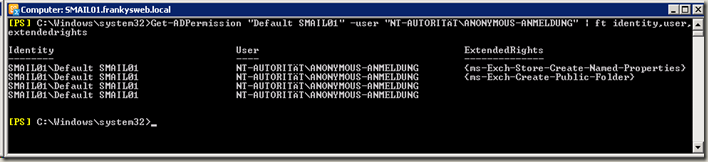
And now the nasty trap: the "Accept-Any-Recipient" right must not be assigned to anonymous users on the default connectors. This can be checked with the shell:
Get-ADPermission "Default SMAIL01" -user "NT-AUTHORITY\ANONYMOUS-ANMELDUNG" | ft identity,user,extendedrights
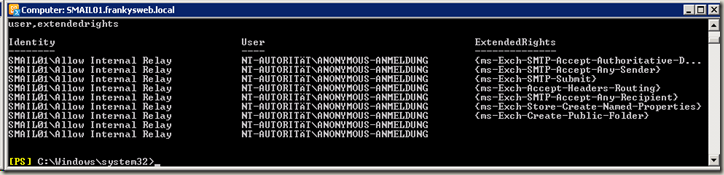
The picture above shows the standard rights. The image below shows a connector on which anonymous relay is permitted:
So it's nice to see in the shell: "Accept-Any-Sender" and "Accept-Any-Recipient". This is a very bad idea if you don't want to end up on a blacklist.
However, some applications require a way to relay their mails anonymously via Exchange. If you need this feature, you should create a separate connector and only allow anonymous relay for the one server with the application. I have described how to do this here:
https://www.frankysweb.de/?p=180
welche Einstellungen beim Exchange Server 2010 genau verhindern, das externe Emails mit der internen Domain an diese gesendet werden?
Beispiel:
Extern sendet von Mailadresse „kopierer@meineDomain.com“ an einige Mitarbeiter des Unternehmens „user@meineDomain.com“ .
Erkennt der Exchange Server nicht automatisch das die Adresse des externen Mailservers nicht die korrekte IP zu der Mail-Domäne ist?
Hi Jochen,
das wird nicht über IP-Adressen geregelt, sondern über Berechtigungen auf den Empfangsconnectoren. Ich schreibe dazu noch einen kleinen Beitrag. Hier aber schon einmal der entsprechende Befehl:
Get-ReceiveConnector „Name des Empfangsconnectors aus Richtung Internet“ | Get-ADPermission -user „NT-Autorität\Anonymous-Anmeldung“ | where {$_.ExtendedRights -like “ms-exch-smtp-accept-authoritative-domain-sender”} | Remove-ADPermission
Gruß, Frank
Hallo Franky,
welche Einstellungen beim Exchange Server 2010 genau verhindern, das externe Emails mit der internen Domain an diese gesendet werden?
Beispiel:
Extern sendet von Mailadresse „kopierer@meineDomain.com“ an einige Mitarbeiter des Unternehmens „user@meineDomain.com“ .
Erkennt der Exchange Server nicht automatisch das die Adresse des externen Mailservers nicht die korrekte IP zu der Mail-Domäne ist?
Vielen Grüße Dank im voraus
Seidel