E-Mail Made in Germany, NSA scandal, Warning for mail server operators etc etc etc... Encryption is currently on everyone's lips. But it's not enough just to quickly attach a certificate to the Exchange server. If you want to have a secure environment (according to the current definition...), you have to think about a few more things. One consideration should be the certificate itself and the various encryption options. Also PFS (Perfect Forward Secrency) is currently a hot topic. To test its certificates, SSLLabs offers a free test that checks the certificates and their checkpoints.
https://www.ssllabs.com/ssltest/
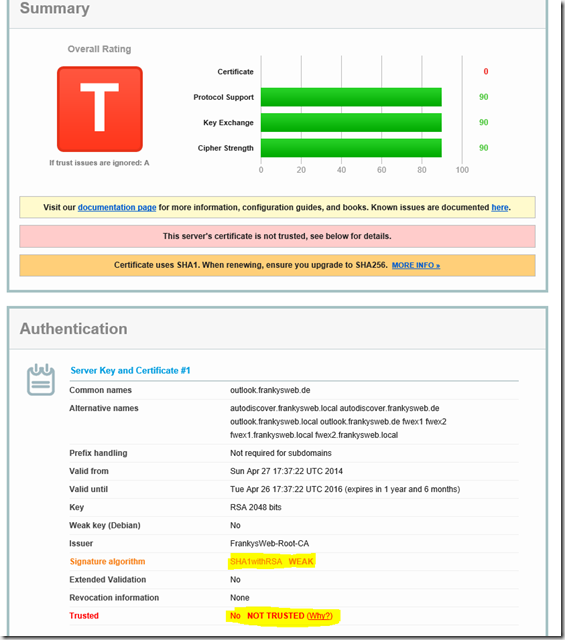
Here is an example of an Exchange 2013 on Windows Server 2012 R2 that is directly accessible via NAT on the Internet:
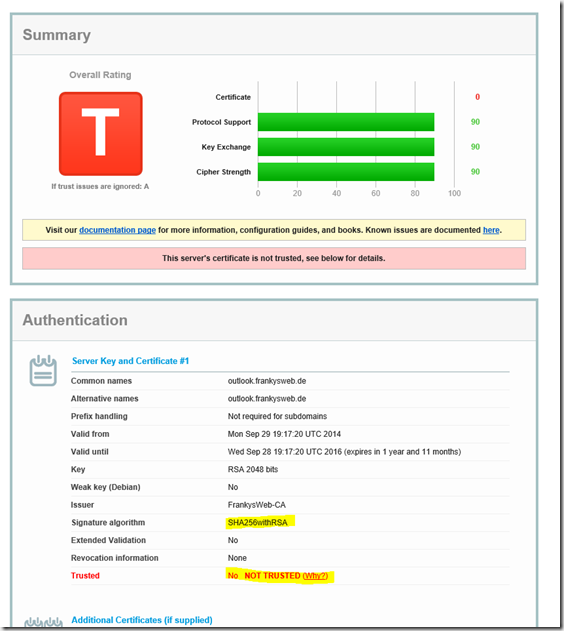
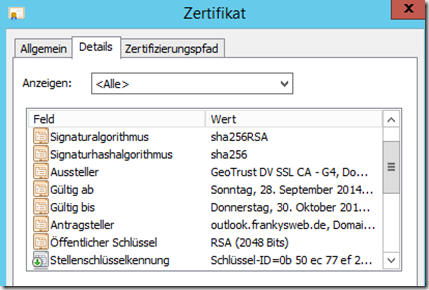
The next screenshot shows the result with a certificate that uses SHA2 (SHA256), the certificate also comes from an internal CA, the red common "T" remains, is also completely OK, but at least one error less:
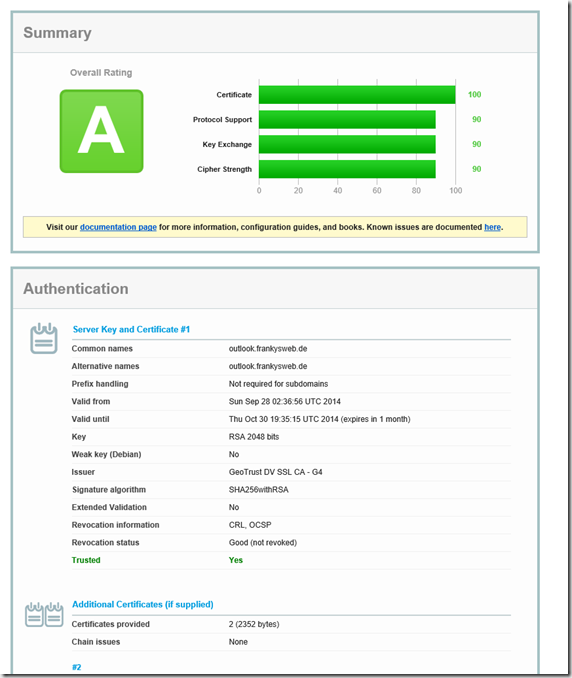
And now once with a valid certificate from a public CA. I used GeoTrust because GeoTrust issues SHA2 certificates for 30 days for testing purposes
https://www.geotrust.com/de/ssl/free-ssl-certificate/
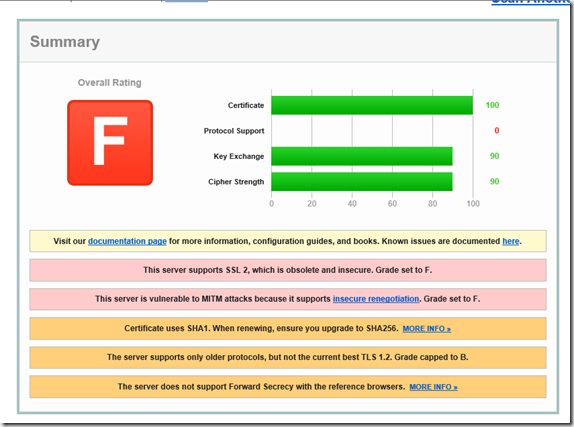
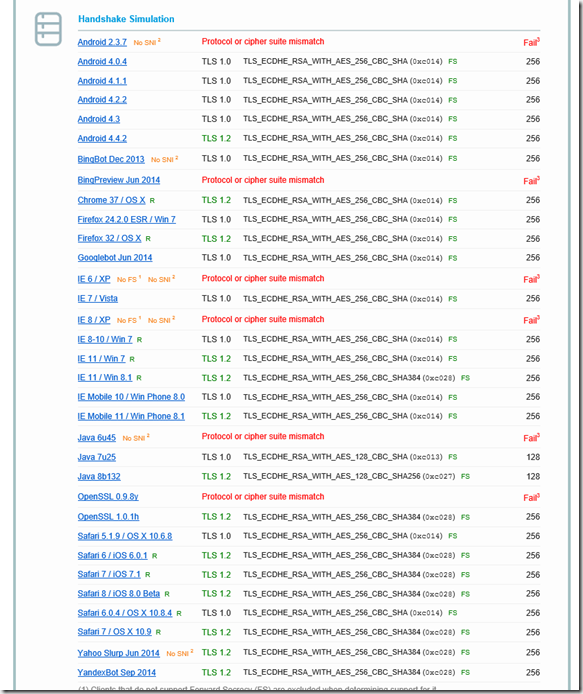
Here is an example of a server that does not use PFS (and also does a few other things wrong), in this case it is a Server 2008 R2 with a relatively old certificate. The certificate comes from a public CA and is therefore valid, but uses SHA1. The server also offers old SSL versions.
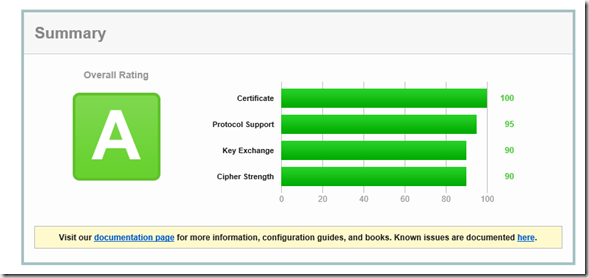
However, the rating can still be improved with a few optimizations, but this will also lock out a few older clients, but everyone else will use PFS:
The rating rises slightly as a result:
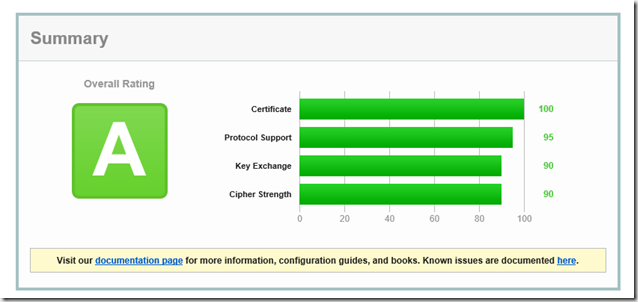
It is therefore always a compromise between safety and convenience (or which devices are supported). Here is a description of how an A+ rating can be achieved:
I think an A+ rating in connection with Exchange is hardly enforceable, because most clients will really be locked out.
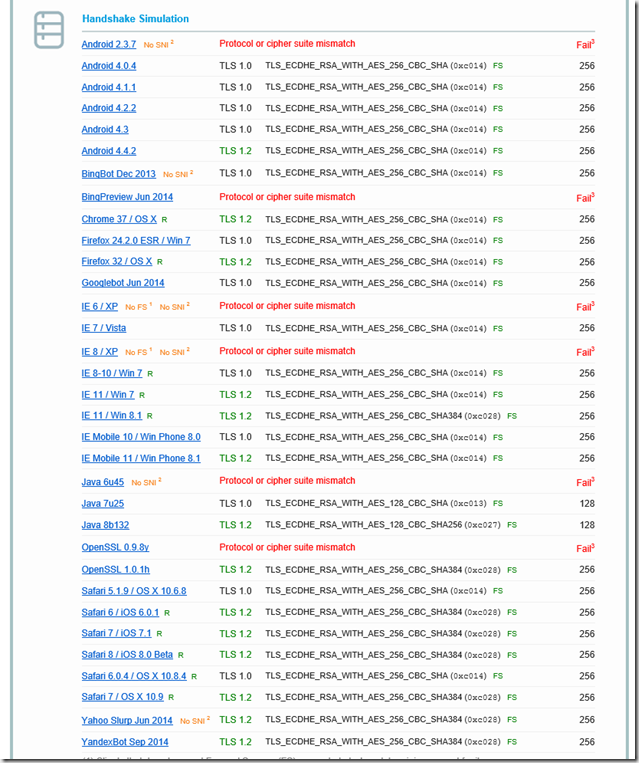
With a public certificate and reasonably up-to-date clients, however, an A rating including PFS can be achieved without major restrictions, which is accompanied by an increase in security:
As mentioned above, I use a public certificate that uses SHA2 (SHA256) and a key length of 2048 bits
A key length of 4096 bits leads to a significantly higher CPU load, which the Exchange server can easily cope with, but smartphones either no longer manage this or do not support it at all.
However, the certificate alone is not enough: Exchange uses the functions of the operating system for encryption. The operating system (in my case Server 2012 R2) therefore specifies which protocols, cipher suites and key exchange procedures the client can use.
The handshake between client and server determines which cipher suite is used. The client and server try to negotiate the best cipher suite that is supported by both. The cipher suite determines which protocol, which hash algorithm and which key exchange procedure is used.
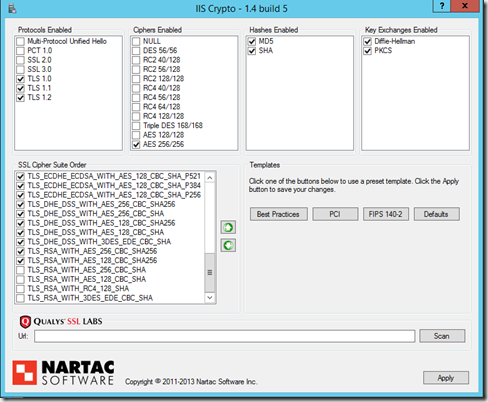
To force clients to use PFS (Perfect Forward Secrency), the respective operating system can be adapted so that it only offers cipher suites that support PFS. The IIS Crypto tool helps to set the appropriate settings:
https://www.nartac.com/Products/IISCrypto/Default.aspx
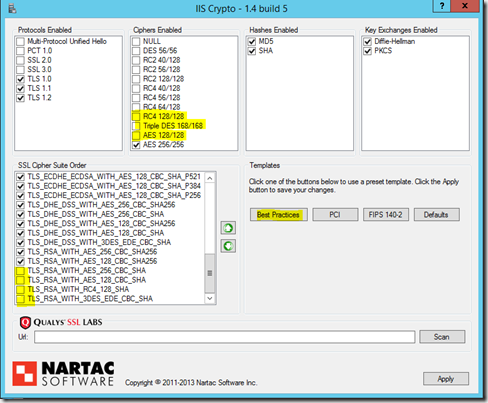
To make the settings for PFS as shown in the screenshot above, click on "Best Practices" once and then deselect RC4, Triple DES and AES128 as ciphers. In addition, the last 4 cipher suites are deactivated.
Restart the server and only PFS will be used. This example is of course dependent on the respective environment. For my tests, I simply forwarded port 443 to the Exchange server. If a web application firewall or a reverse proxy is used, the corresponding settings must of course be made there.

Moin Moin,
sobald ich das „Best Practise“ anwende, bekommt kein Outlook 2016 eines Laptops (W7) / einer RDS (2012R2) Sitzung eine Verbindung in Outlook zum Exchange 2016 mehr zu Stande.
Muss es denn nicht über TLS 1.1 / 1.2 laufen?
Beste Grüße
Jens
Moin Frank,
kannst du mal nen Artikel zur einrichtung von DANE samt DNSSEC machen?
Ein kleines How-To wie und wo man es einrichtet. Das wäre klasse!
Beste Grüße
Daniel
Hallo Frank,
das ist eine wirklich schöne Beschreibung und hab mit deinen Tipps nun auch ein grünes A beim SSL Test. Es funktioniert alles prima.
Seit dem wird allerdings auf meinem Mail-Server leider das Eventlog mit immer der gleichen Fehlermeldung vollgemüllt und ich hab bis jetzt noch keine Lösung gefunden. Vielleicht hast du einen Tipp für mich?
Es ist ein Exchange 2010 SP3 mit RU8v2 auf einem Win2008R2 Server. Der Fehler ist ein Schannel-Fehler mit Event-ID 36887 – Es wurde eine schwerwiegende Warnung empfangen: 40.
Mehr Details gibt es zum Fehler leider nicht, nur das er unregelmäßig alle paar Minuten im Eventlog eingetragen wird.
Vielen Dank schon mal
Grüße Matthias
Hi Matthias,
der Fehler im Eventlog wird generiert wenn das SSL/TLS-Handshake fehlschlägt. Ursachen können folgende sein: Uralt Browser, MTA der keine aktuellen Ciphersuiten unterstützt, Smartphones etc etc.
Mann kann die Schannel Meldungen abschalten:
https://support.microsoft.com/en-us/kb/260729
Gruß, Frank
Schöner Artikel!
Eine Anleitung wie ich ein solches SHA2 (256) Zertifikat mit einer normalen Windows Zertifizierungsstelle als selbst signiertes Zertifikat für Exchange 2010 / 2013 erstellen kann wäre super! Mit dem normalen Prozedere bekomme ich immer nur ein SHA1 Zertifikat und habe nirgends die Auswahl …
Danke und Gruß
Hallo Steffen,
danke. Es gibt bereits einen Artikel dazu, um Zertifikate mit SHA256 auszustellen, muss auch die CA mit SHA256 signiert sein. SHA256 lässt sich entweder bei der Installation auswählen, oder beim Erneuern des CA Zertifikats:
https://www.frankysweb.de/exchange-2013-san-zertifikat-und-interne-zertifizierungsstelle-ca/
Gruss, Frank