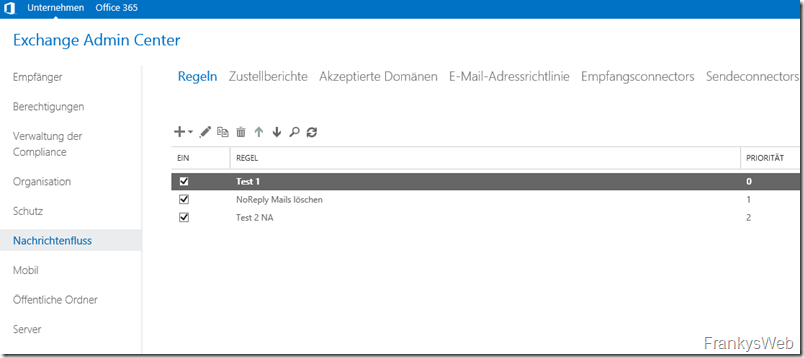
Exchange transport rules can be used to perform certain actions when receiving or sending emails. For example, mails can be redirected, rejected or provided with a disclaimer using a transport rule. There are many ways to implement certain actions for mails using transport rules, but with many transport rules it quickly becomes somewhat confusing and it is not always clear which rule is executed when. If there are only a few transport rules, it is still easy to keep an overview, here you can quickly go through and check which rules are still relevant.
With a large number of rules, however, it can quickly happen that some rules are superfluous and are no longer executed. This often occurs with mail redirection using transport rules. Unfortunately, it is not trivial to find out which transport rule is still in use. This information can only be determined quite covertly from the message tracking logs.
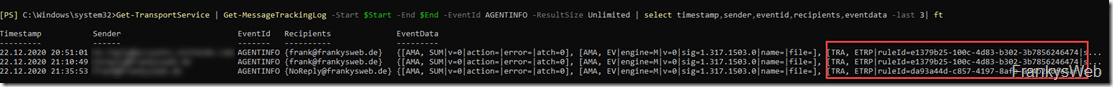
As an example, the following command can be used to determine from the message tracking logs which transport rules have been applied to a mail:
Get-TransportService | Get-MessageTrackingLog -Start $Start -End $End -EventId AGENTINFO -ResultSize Unlimited | select timestamp,sender,eventid,recipients,eventdata -last 3| ft
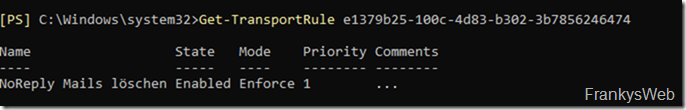
The Eventdata field now contains several details, including information on the transport rules. The "RuleID" specified in the "EventData" field can at least be used to find the transport rule:
Get-TransportRule e1379b25-100c-4d83-b302-3b7856246474
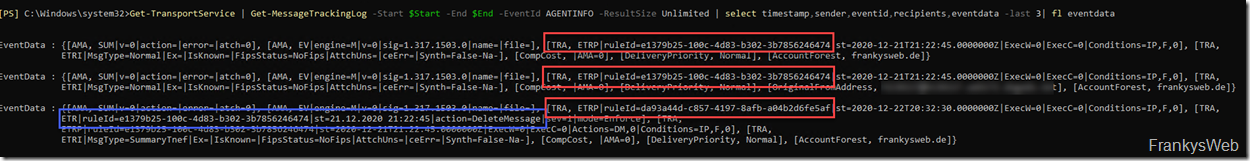
One small hurdle, however, is that specifying a RuleID within EventData does not necessarily mean that the transport rule has been executed. This becomes visible when you look at the complete "EventData" field:
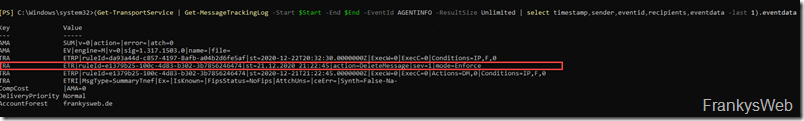
Get-TransportService | Get-MessageTrackingLog -Start $Start -End $End -EventId AGENTINFO -ResultSize Unlimited | select timestamp,sender,eventid,recipients,eventdata -last 3| ft eventdata
In the screenshot you can see the 3 mails again, all 3 mails have at least one RuleID in the field EventData, but only the last mail also shows an "Action". If you now take a closer look at the "EventData" field, you can see that the value "ETRP" and "ETR" are different. A transport rule is therefore executed if "ETR" (not "ETRP") and also an "Action" is specified within EventData.
It becomes a little easier to read if you display "Eventdata" for a specific mail:
(Get-TransportService | Get-MessageTrackingLog -Start $Start -End $End -EventId AGENTINFO -ResultSize Unlimited | select timestamp,sender,eventid,recipients,eventdata -last 1).eventdata
This overview makes it easier to recognize which entries within "EventData" belong to each other. As a reminder, only the transport rule that contains "ETR" and an "Action" is executed, the other rules are not applied.
It is therefore not so easy to find out which transport rules are in use and are applied to mails. I have therefore created a small script to create an overview of which transport rules are being executed:
#Time Range for Searching Message Tracking Logs
$Start = (get-date).AddDays(-1)
$End = (get-date)
#Search MessageTracking Log in specified Timerange
$MessageTrackingLog = Get-TransportService | Get-MessageTrackingLog -Start $Start -End $End -EventId AGENTINFO -ResultSize Unlimited | select eventdata,MessageId
#Get all Mails where a Transport Rule was applied
$MailsWithTransportRules = $MessageTrackingLog.EventData | where {$_.key -eq "TRA" -and $_.Value.StartsWith("ETR|") -and $_.Value -match "action="}
#Get Transport Rule GUID from Mails with triggerd Transportrule
$TriggeredRules = @()
foreach ($MailWithTransportRule in $MailsWithTransportRules) {
$TriggeredRules += $MailWithTransportRule.Value.Split("|")[1].Split("=")[1]
}
#Get All TransportRules
$AllTransportRules = Get-TransportRule -ResultSize unlimited
#Group Triggerd Rules and Count Trigger Count
$TriggeredRulesGroups = $TriggeredRules | group | select count,name
#Loop all TransportRules and check if it was triggerd
$TriggeredRulesOverview = @()
foreach ($TransportRule in $AllTransportRules) {
$TransportRuleGUID = $TransportRule.Guid
$TransportRuleName = $TransportRule.Name
$TransportRuleState = $TransportRule.State
$TransportRuleDescription = $TransportRule.Description
#If Transport Rule was triggerd, update $TransportRuleCount, else set $TransportRuleCount to 0
if ($TriggeredRulesGroups.Name -contains $TransportRuleGUID) {
$TransportRuleCount = ($TriggeredRulesGroups | where {$_.Name -match $TransportRuleGUID}).Count
}
else {
$TransportRuleCount = 0
}
$TriggerdRulesOverview += New-Object -TypeName psobject -Property @{RuleID="$TransportRuleGUID"; RuleName="$TransportRuleName"; RuleState="$TransportRuleState"; RuleDescription="$TransportRuleDescription"; RuleCount=$TransportRuleCount}
}
#Output Results
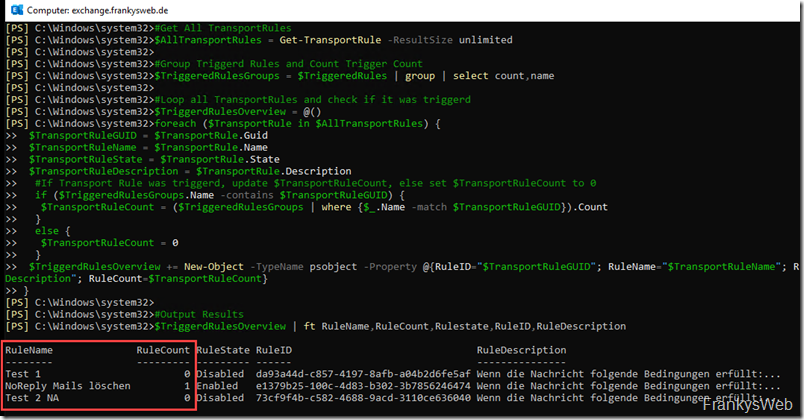
$TriggerdRulesOverview | ft RuleName,RuleCount,Rulestate,RuleID,RuleDescription
The script provides an overview of which transport rules have been executed within the last day:
The time period can be adjusted using the "Start" variable in the first line. With a longer time period, you can shed some light on the transport rules. Hopefully only a few rules will then remain, which can then be checked manually. Alternatively, the script can also be easily adapted to your own requirements, for example to find out which mails a particular rule has been applied to.
Hallo,
Ich hatt das selbe Probem, man muss das Audit dazu aufdrehen, ansonsten wird die Action nicht geloggt – siehe auch
https://docs.microsoft.com/de-de/archive/blogs/eopfieldnotes/auditing-transport-rules
lg,
Hallo, das habe ich immer schon gesucht. Leider wirft das Skript bei mir nichts raus, auch nicht mit größerem Zeitraum.. obwohl täglich Regeln angewendet werden. Ich bräuchte da mal einen Tipp, was da falsch läuft.
Hi,
falls man die Nachricht zur Hand hat (ist nicht immer der Fall) hilft es auch – und das machen wir gerne: Jede Transportregel wird so konfiguriert, dass Sie einen Header einfügt und den Namen der Regel beinhaltet (Oder ein Kennzeichen). Damit sieht man das sehr schön, welche Regeln angewendet wurden.