In the previous articlesA very small Exchange organization was set up and the question arose as to whether an environment for a higher number of users and better availability could be subsequently created. A higher number of users can of course also be mapped with a Singe Server solution if the resources are sufficient. In the event of a defect, the failure would of course affect all users or at least a large proportion of them.
To briefly repeat the question once again:
I would like to rebuild the environment like this, at the moment we are only a small company with a relatively limited budget for IT, we have so far managed with a NAS as a "server", but we are slowly reaching its limits and want to buy a corresponding server. However, as we are also growing rapidly and may buy another company, I wonder whether it is possible to expand this example configuration even further in terms of availability and a higher number of users?
The answer to this question is: Yes, it is possible. The following articles show how.
The following articles refer to the previous articles on setting up a small Exchange 2016 organization. Therefore, please read these articles first:
- Part 1: Installation Active Directory and configuration DNS
- Part 2: Installation Exchange Server 2016 CU 2
- Part 3: Exchange Server configuration incl. certificate
- Part 4: Configuration Sophos UTM 9.4 and Exchange Server for receiving / sending e-mail
- Part 5: Configuration Exchange Webservices, Sophos UTM, Fritzbox
Foreword
Availability is always an issue. Every company defines the availability requirements differently, which is only logical and also correct, because in every company there are services that are important, because they may be critical to production, and services that are less important. The category in which the company classifies its Exchange Server therefore depends on the company.
However, there is a lot to consider in a highly available Exchange environment, as many different components are involved: Network infrastructure (Internet connection, routers, switches, firewalls, antiSPAM gateways), server hardware, Active Directory, DNS and finally the Exchange servers themselves.
Unfortunately, I cannot provide the complete "all-in-one" solution at this point, as I do not have the necessary hardware. The following articles will therefore deal less with the network infrastructure, but there will certainly be one or two tips.
The surroundings
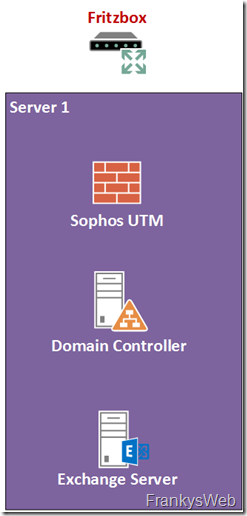
The small Exchange environment basically looks like this:
There is one physical server (Server1), this server is home to 3 virtual machines: Sophos UTM as firewall / antiSPAM gateway, domain controller and Exchange server. Internet access is via a Fritzbox.
Server1 is a normal server with local storage, whether Hyper-V, VMware ESXi or whatever is used as a hypervisor is irrelevant, because if Server1 fails, it goes dark.
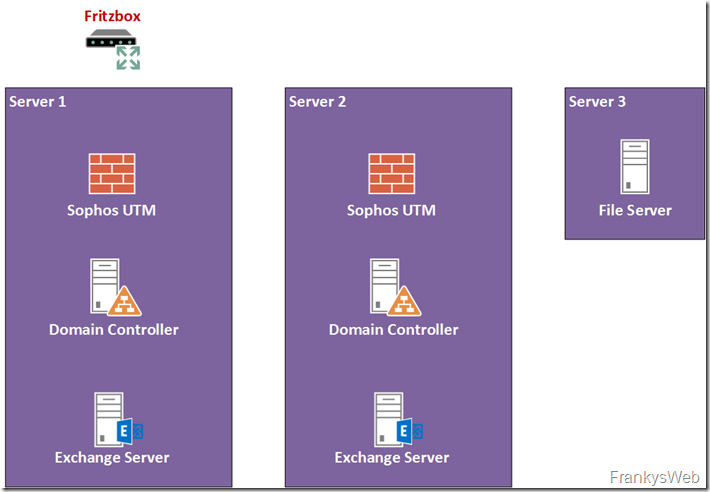
For this reason, the small Exchange organization is expanded somewhat to be able to absorb a server failure:
Two additional servers are required for this. Server2 will also be home to 3 VMs, just like Server1 also a UTM, a domain controller and an Exchange server. Server2 should therefore have at least the same hardware equipment as Server1. Server3 does not necessarily have to be a HyperVisor, which is why it is also "smaller". For Server3, a Windows Server with FileServer role is sufficient to provide the Witness for Exchange later on. I will go into this in more detail in the following article.
Preparations
In preparation, I created two virtual Windows 2012 R2 servers on Server2 and added them to the existing Active Directory.
The names of the VMs are as follows:
- dc2.frankysweb.org
- exchange2.frankysweb.org
The VM for the UTM will be added later. Only the Windows updates were installed on the Windows servers and added to the domain.
The virtual resources are the same as the VMs on Server1.
Configuration of second domain controller on Server2
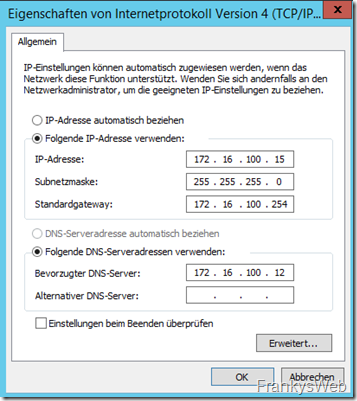
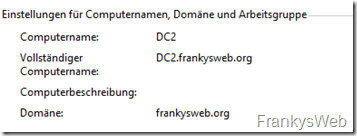
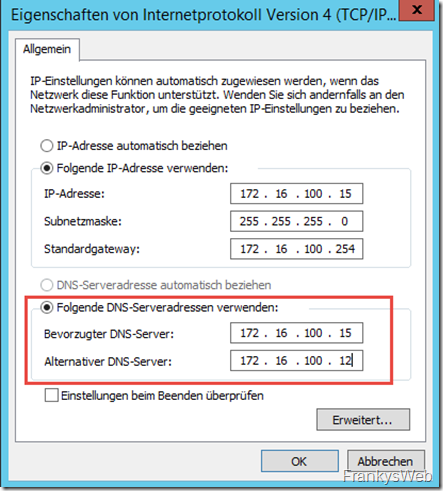
The heart of the small Exchange organization is the Active Directory. It is always advisable to install at least two domain controllers per domain, otherwise the entire environment will quickly come to a standstill if one domain controller fails. Fortunately, it is quite easy to set up the Active Directory redundantly. In principle, it is sufficient to add an additional domain controller. In the case of the small Exchange organization, an additional server with the name "DC2" was installed. DC2 has the following network configuration:
The server with the name "DC2" is currently only a member of the Active Directory. Apart from the operating system and Windows updates, nothing has been installed yet.
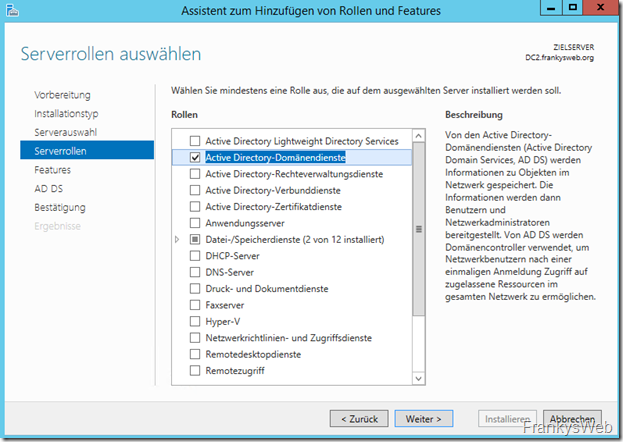
To turn the server into a domain controller, the roles must first be installed:
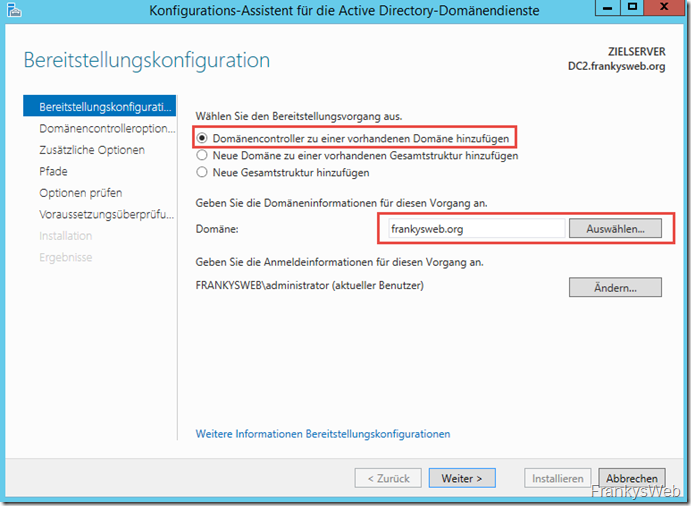
After installation, the server can be upgraded to a DC. DC2 is installed as an additional domain controller in the existing Active Directory:
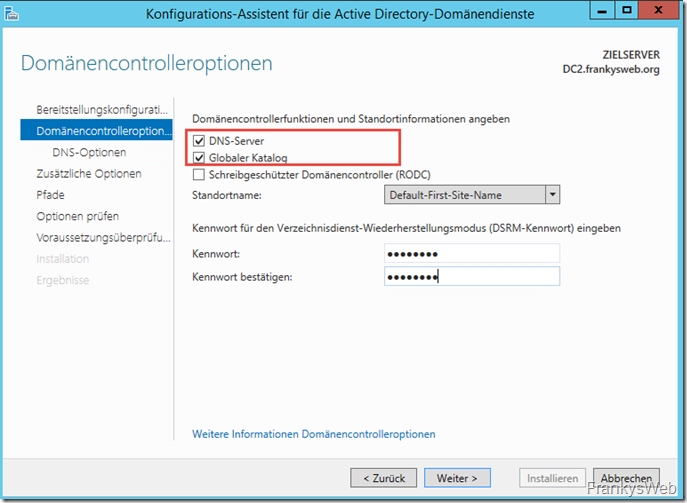
The new Domain Controller will also be DNS and Global Catalog, the remaining dialogs can be confirmed with "Next":
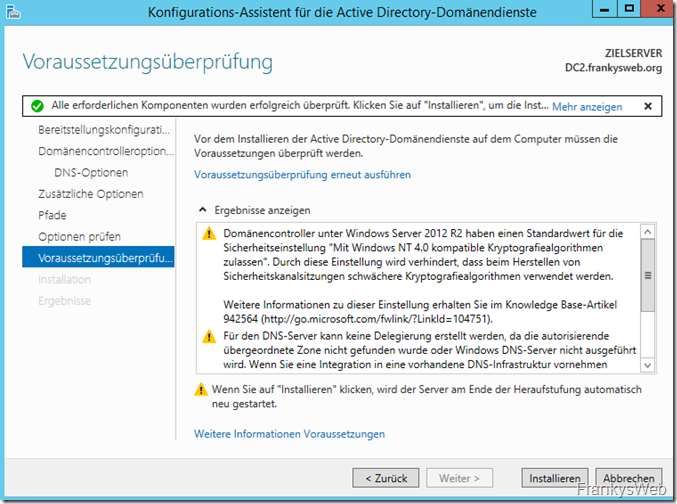
The warnings in the prerequisite check are normal, as mentioned in the previous posts.
After the restart, there are still a few small configurations to be made. The network configuration is changed as follows:
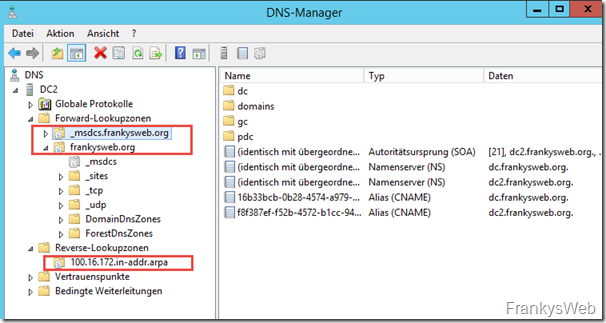
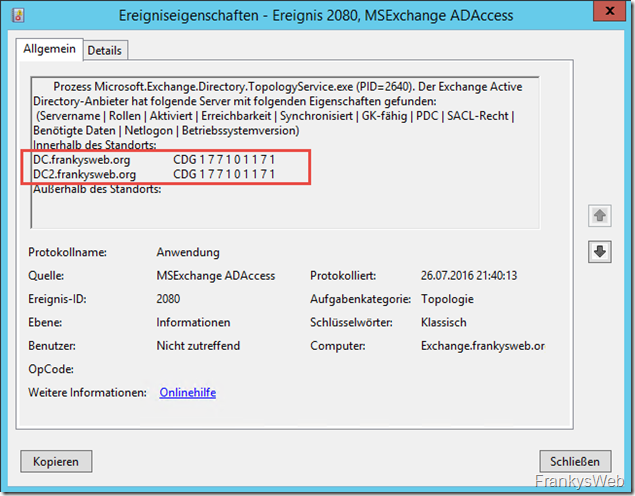
This means that DNS records can also be resolved by this server if a DNS server fails. DC2 should now have already received the DNS zones through Active Directory replication:
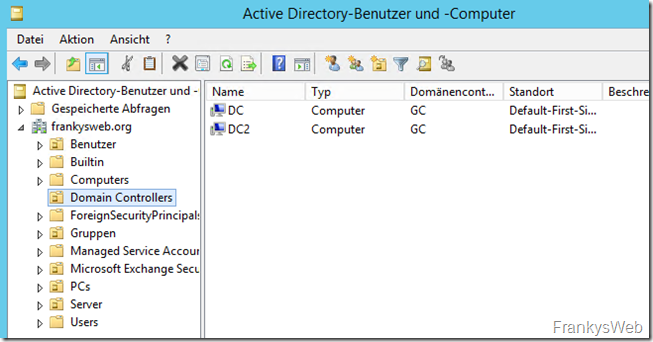
There should now also be a corresponding computer account in the "Domain Controllers" OU in the Active Directory:
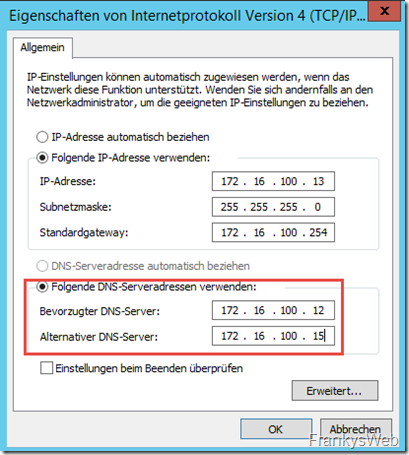
All other servers and clients (possibly via DHCP) must now have the additional DNS server configured. Here is an example of the existing Exchange server with the name "Exchange":
Important: In addition to the preferred DNS server, all clients and servers must also have the alternative DNS server configured; in principle, it does not matter which DNS server is named first. If the preferred DNS server fails, the system waits for a timeout and then uses the alternative DNS server. If the preferred DNS server fails, there may be waiting times, but the important thing is that it continues to work. You could also configure the clients/servers 50/50: 50% of the clients/servers use "DC" as the preferred DNS, the other 50% use "DC2".
Exchange also finds the second DC and logs this with EventID 2080:
Configuration Sophos UTM
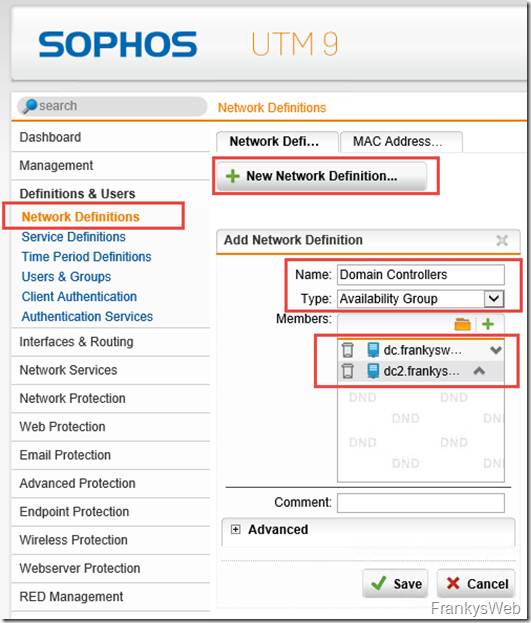
In order for the Sophos UTM to be able to use both domain controllers, an "Availability Group" must first be created. Both domain controllers are then added to this group:
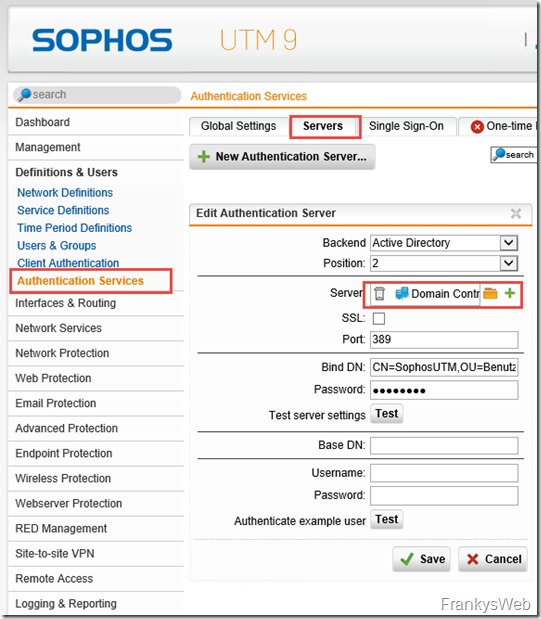
The new group is now used for the Authentication Services:
This means that the UTM is also able to tolerate the failure of a DC.
Summary
Making the Active Directory redundant is the easiest part. In principle, it is sufficient to configure an additional DC. It is important at this point that all clients and servers also have the second DC configured as a DNS server. In this way, the Active Directory can already intercept the failure of Server1.
Ich denke mal einige Admins bauen sich zum Lernen und testen so eine kleine virtuelle Umgebung in der Fa oder zu Hause auf … als MS Partner oder als Student kommt man ja an die Software ran … Mit den Artikeln gelingt ein Nachbau hervorragend und es auch noch einige klarer und wird erklärt … Danke .. Klasse Vorarbeit, was uns viel Zeit spart.
Es gibt nichts unsicheres im Web als Email und sie wurden seit jeher in der Cloud gespeichert, nur nannte man das früher nicht so.
Wenn man Herr über seine Daten sein will, hilft nur konsequente Verschlüsselung. Ende-zu-Ende bei Mails und Dateien. Aber dafür braucht man keine teure Infrastruktur. Erst wenn nicht mal mehr der interne Admin fremde Dateien oder Emails lesen kann, ist man Herrscher über seine Daten.
Hi,
naja, ganz so schlimm sieht es dann doch nicht aus. Die meisten Mail Server kommunizieren verschlüsselt miteinander, der Transportweg der Mails ist also in vielen Fällen verschlüsselt. Natürlich kann man nach dem Versenden einer Mail (ohne entsprechende Maßnahmen) nicht mehr kontrollieren was mit den Daten passiert, hier hilft aber auch nicht zwingend Verschlüsselung der Daten weiter, denn ich kann gar nicht mit Sicherheit sagen ob eine Verbindung/Mail Ende-zu-Ende verschlüsselt ist, denn beim Empfänger könnte ein E-Mail Gateway sein, welches Ver- und Entschlüsselung am Gateway übernimmt. Auch eine Verschlüsselung der Mail würde nicht weiterhelfen, wenn ein User fälschlicherweise sensible Informationen per Mail an den falschen Empfänger schickt. Aber auch dafür gibt es Lösungen, nennt sich dann AD RMS.
Gruß, Frank
Da stimme ich Ulrich zu, aber nicht jeder möchte seine Emails in der Cloud haben.
Und wenn jemand alleinig Herr über seine Daten sein möchte muss halt ein wenig in die Tasche greifen :-)
Ich möchte Frank nochmals zu seinen sehr guten Anleitungen gratulieren, weiter so :-)
Ich würde dem Fragesteller empfehlen einen der Exchange Online bzw. O365 Pläne zu nutzen. Das senkt die Komplexität und den Administrationsaufwand deutlich. Wenn man bedenkt, dass man min. 3x Windows Server+CAL, 2x Exchange+CAL, eine Exchange Backup Lösung braucht, verschlingt sowas recht viel Geld, von dem know how, dass man braucht ganz zu schweigen.
Oder sehe ich das falsch?
Hi,
ich mag das nicht mit Ja oder Nein beantworten, ich möchte die „Cloud“ weder verteufeln noch als Allheilmittel darstellen. Es kommt hier wie immer auf das Unternehmen an, was sind die Anforderungen, was ist bereits vorhanden, was muss gekauft werden usw. Exchange Online Plan 1 kostet für 100 Benutzer auf 3 Jahre gerechnet auch schon 12240 EUR. Allerdings war das auch mein erster Gedanke: Warum nicht Office 365!?
Bitte diese Artikel aber auch nicht falsch verstehen, hier geht es um die Möglichkeiten und die Konfiguration, nicht darum das es für alle wie die Faust auf das Auge passt. (Und Office 365 kommt auch noch dran ;-) )
Gruß, Frank