In addition to Let's Encrypt, StartSSL also offers free SAN certificates for up to 5 domains with a term of 1 year for free. The certificates are supported by all common browsers and devices.
The advantage of StartSSL over Let's Encrypt is that the certificates are valid for 1 year, whereas with Let's Encrypt they are only valid for 3 months. This means that the certificates do not need to be replaced quite as often.
StartSSL also offers a client that automatically configures the IIS and requests and installs the certificate. However, this method should be used with caution on Exchange servers. Simply binding the certificate to the IIS is not enough, it must also be stored in the Exchange configuration.
I therefore advise against using the client. StartSSL, like every other CA (unfortunately not Let's Encrypt), also offers the option of submitting a CSR and thus obtaining the certificate. I still think the CSR option is the best, as you can be sure that the private key will not leave the server. In addition, no complicated firewall adjustment (WAF) is required, nor does a tool have to be used to configure the IIS server.
Small Howto StartSSL SAN certificates and Exchange Server
An account with StartSSL is required (free of charge) so that certificates can be requested via CSR. An account can be created here:
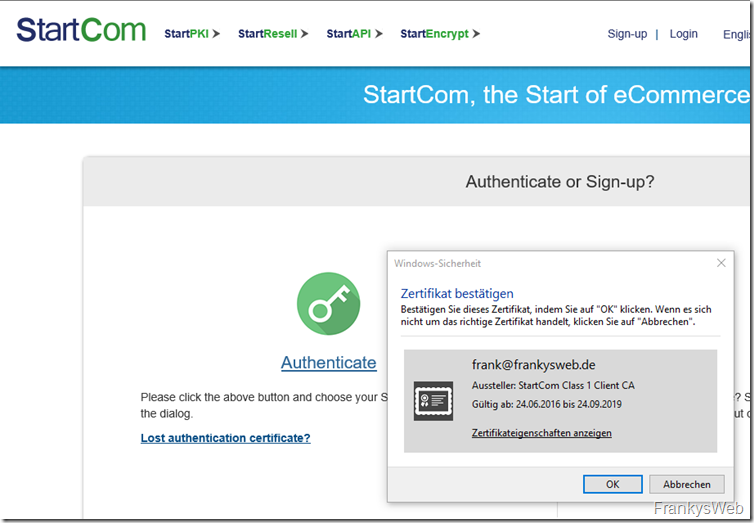
Once the account has been created and the client certificate for logging in has been installed, you can log in with the account here:
Note: StartSSL requests a client certificate here, which is issued when the account is created. Users of firewalls with SSL inspection must therefore configure a corresponding exception.
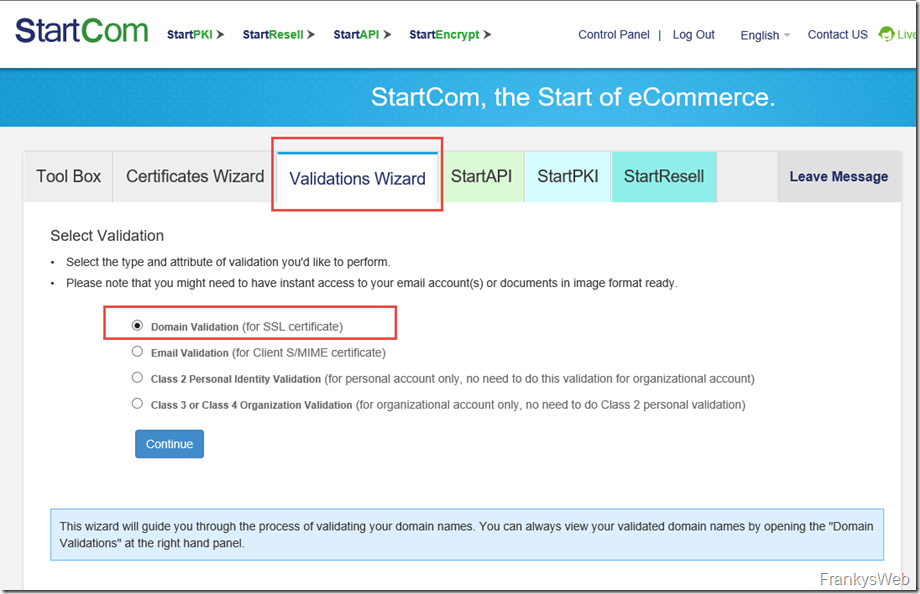
To obtain a certificate, the domain must first be validated. Domains can be validated under "Validation Wizard":
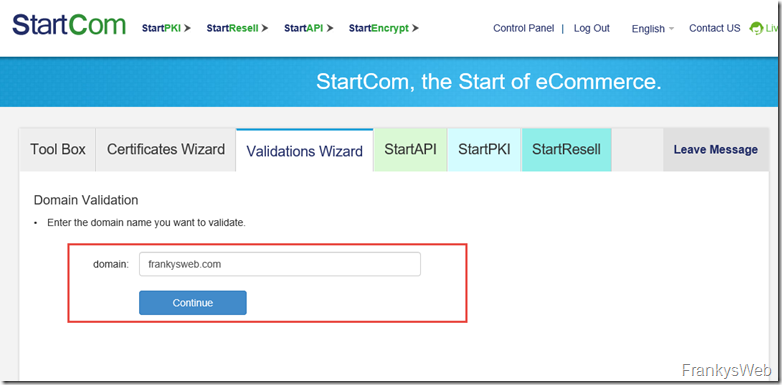
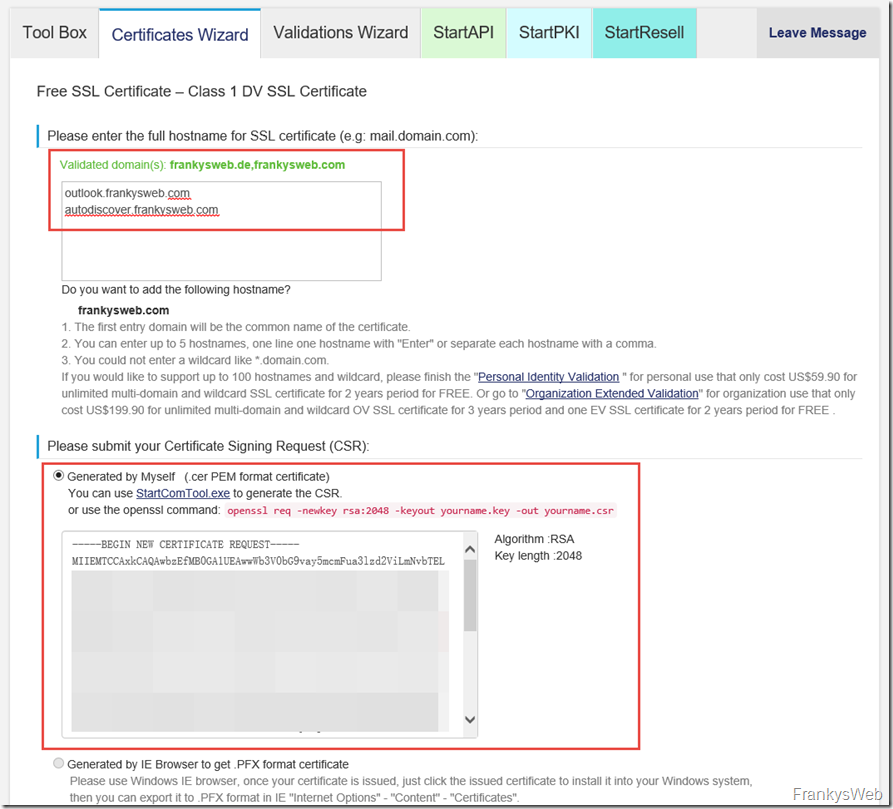
In this example, the domain "frankysweb.com" is validated so that a certificate with the names "outlook.frankysweb.com" and "autodiscover.frankysweb.com" can be requested later:
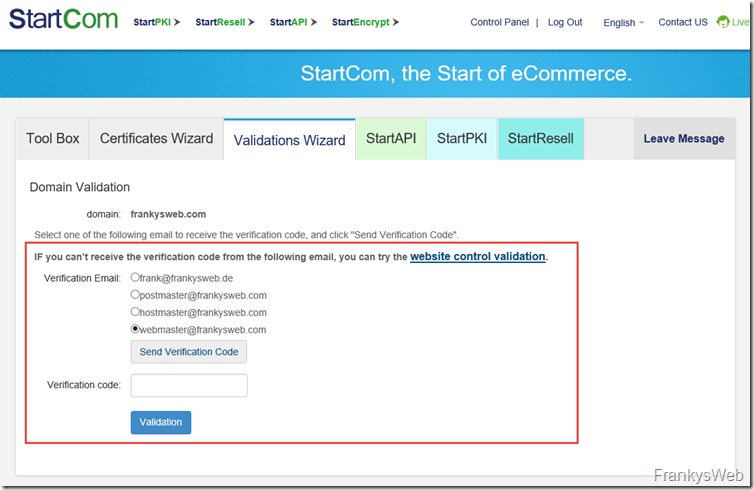
You can now select the e-mail address to which the code should be sent for verification:
Once the code has been entered, the domain is validated and a CSR can be generated on the Exchange server:
New-ExchangeCertificate -Server "Servername" -GenerateRequest -FriendlyName "Exchange certificate" -PrivateKeyExportable $true -SubjectName "c=COUNTRYCODE, s=COUNTRY, l=CITY, o= COMPANY, ou=ORGANIZATION, cn=ALLEGMEINERNAME" -DomainName outlook.frankysweb.de,autodiscover.frankysweb.de -RequestFile "\\SERVERNAME\C$\Request.csr"
-Friendlyname is the display name of the certificate in ECP, the name is freely selectable
-SubjectName determines the properties of the certificate:
"c" stands for the country code, for example "DE"
"s" stands for the federal state
"o" stands for the company
"ou" stands for the organizational unit (IT, Exchange, EDP...)
"cn" stands for the common name, the common name should contain the FQDN for OWA
-DomainName: All alternative names for the certificate are entered here, as well as the general name, normally only Autodiscover and the access name for Outlook, OWA, ECP, ActiveSync etc. are required here, i.e. in this example:
outlook.frankysweb.com
autodiscover.frankysweb.com
-Requestfile: A share on which the request can be saved
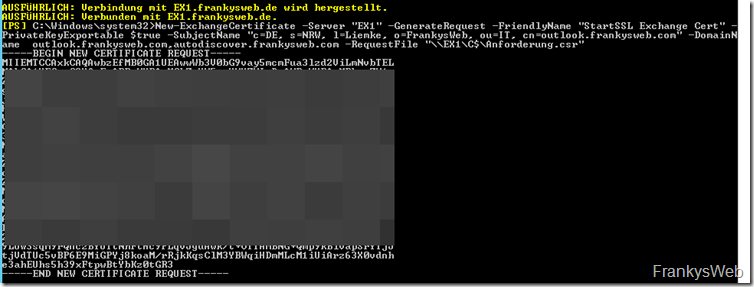
Here is an example of my CSR:
New-ExchangeCertificate -Server "EX1" -GenerateRequest -FriendlyName "StartSSL Exchange Cert" -PrivateKeyExportable $true -SubjectName "c=DE, s=NRW, l=Liemke, o=FrankysWeb, ou=IT, cn=outlook.frankysweb.com" -DomainName outlook.frankysweb.com,autodiscover.frankysweb.com -RequestFile "\\EX1\C$\Request.csr"
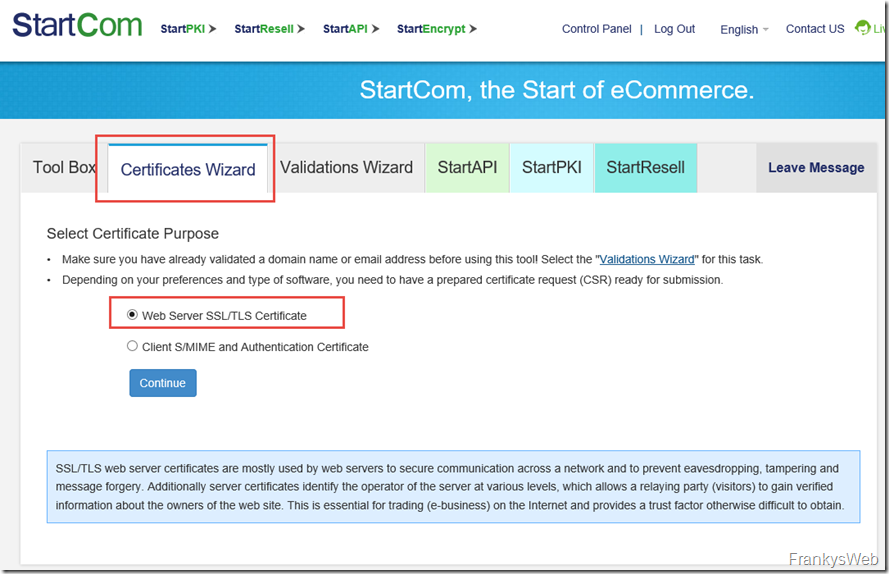
The CSR is also displayed directly here and can now be submitted to StartSSL. To do this, select "Certificate Wizard" and "Web Server SSL/TLS Certificates" at StartSSL
The domains and the CSR must then be entered:
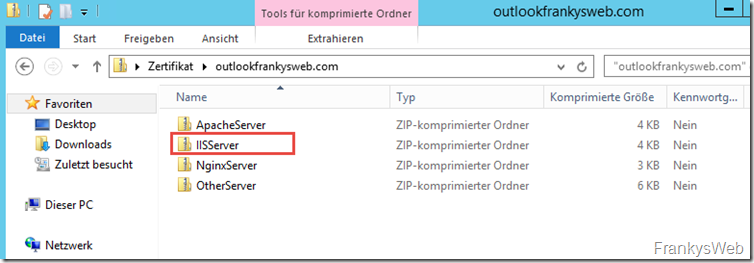
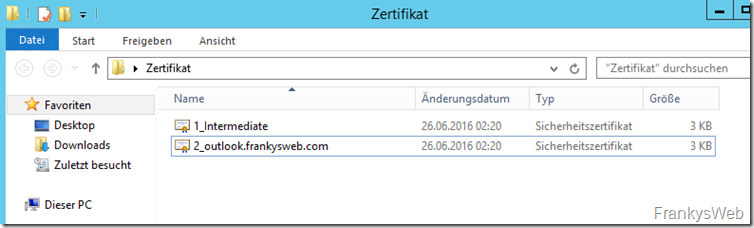
After clicking on "Submit", the certificate can then be downloaded. The download consists of a ZIP archive in which the certificate is available in various formats:
IIS server is the right choice here. The IISServer folder contains the intermediate certificate (1_Intermediate) and the Exchange certificate (2_outlook.frankysweb.com)
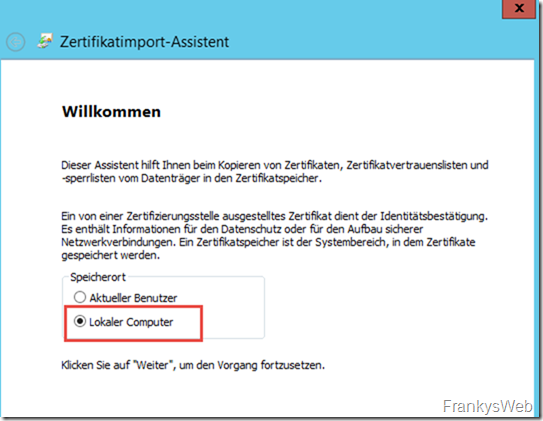
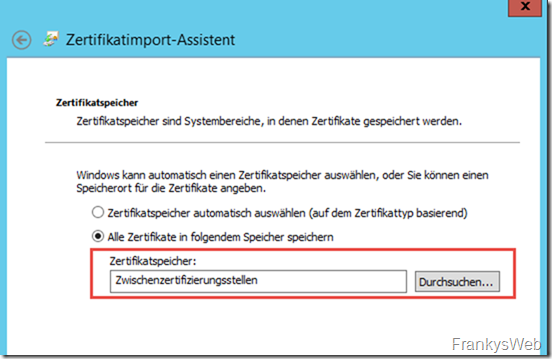
First, the intermediate certificate is installed:
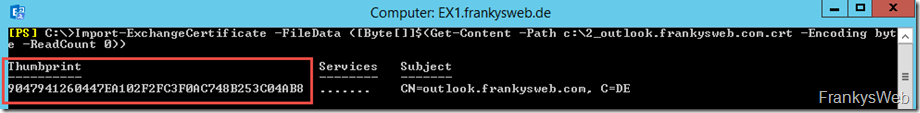
Now the Exchange certificate can be installed with the following command:
Import-ExchangeCertificate -FileData ([Byte[]]$(Get-Content -Path c:\2_outlook.frankysweb.com.crt -Encoding byte -ReadCount 0))
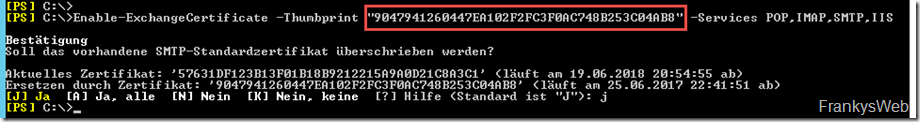
After the certificate has been installed and the request has been completed, the Exchange services still need to be bound to the new certificate (this is the part that the tools unfortunately ignore):
Enable-ExchangeCertificate -Thumbprint "ThumbprintVomImport" -Services POP,IMAP,SMTP,IIS
Important: Set a reminder so that the certificate can be renewed in good time before it expires. Here is a simple Certificate management using Excel and PowerShell.
Update 11.01.17Apple has removed StartSSL and Woosign from the trusted CAs. This means that these certificates can no longer be used with Apple devices. At Let's Encrypt there are still free certificates.
Hallo,
vielen Dank für die tollen Anleitungen!!
Ich habe leider ein Problem mit ActiveSync – habe einen Exchange 2013 im Einsatz und zuerst ein Wildcard-Zertifikat verwendet. Dachte, dass es eventuell daran liegt nach Deiner Anleitung auf ein StartSSL SAN-Zertifikat gewechselt. Leider ist das Ergebnis das gleiche…Autodiscover in Outlook funkt einwandfrei, nur Autodiscover am Smartphone will einfach nicht (getestet mit Galaxy S7/Android 6.0.1).
Hast Du eventuell eine Idee?
Danke LG
Matthias
Ups Doppelpost! Bitte das hier und den Doppelten entfernen! Danke :-)
Hi, erledigt. Du hast Rest Mozilla und Apple haben StartSSL und WoSign wegen Regelverstoß aus den vertrauenswürdigen Stammzertifizierungsstellen entfernt.
Gruß, Frank
Hallo Frank,
vor letzte Woche bin ich am Einrichten von ActiveSync an einem iPhone 7, trotz Public Cert (WoSign, anderer Post von dir!:-)) Gescheitert.
Ein Blick ins Log der Sophos hat mir angezeigt das der Benutzer abgewiesen wurde. Komischerweise funktionierte die Einrichtung mit einem Nokia Lumia Problemlos.
Nach kurzer Recherche stellte sich heraus das Apple diese Zertifizierungsstellen als nicht Vertrauenswürdig eingestuft hat.
Das iOS 10 akzeptiert schlichtweg die Zertifikate von WoSign nicht mehr, StartCom konnte ich nicht verifizieren.
Nachdem ich das Zertifikat auf der Sophos gegen ein Thawte getauscht habe, konnte ich die iPhones via EAS konfigurieren.
Hallo!
Funktioniert bestens.
SOGAR 3 JAHRE !!!!!!!!!!!!!!!!!!!!!!!!
Danke für diese tolle Anleitung! Habe sie zu Hause auch durchgeführt und habe nun kein rotes Warnsymbol mehr im Browser. Der Beitrag nimmt einem die Angst vor Zertifikaten….