Service accounts for starting Windows services or scheduled tasks are often configured with the "password never expires" attribute and then used for years. Often such service accounts are also alienated for a specific purpose and used on many servers for a wide variety of tasks. Service accounts with far-reaching authorizations and passwords that never expire then make it easier for attackers. Group Managed Service Accounts (gMSA accounts) are an alternative.
Group Managed Service Accounts (gMSA accounts) are better suited for launching scheduled tasks and services than normal Active Directory user accounts with never expiring passwords. The main advantage of gMSA accounts is that no password needs to be managed for this account. gMSA accounts are configured on the servers and Windows takes over the password management for the account.
This simplifies the management of service accounts as no manual user interaction is required to change the password regularly. In addition, these accounts are restricted to specific servers, so the gMSA accounts cannot be easily misused and used on many servers for different tasks.
Preparation for gMSA accounts (KDS Root Key)
In order for gMSA accounts to be created and used, a KDS root key is first required to generate the passwords. The KDS root key can be generated with the following command:
Add-KdsRootKey -EffectiveImmediately
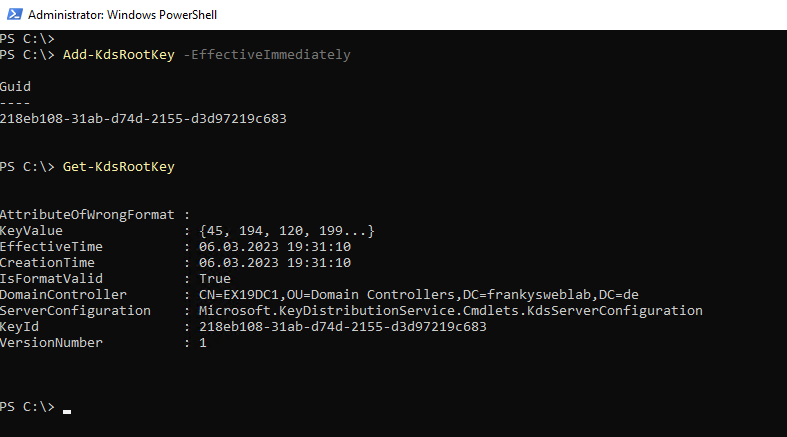
You must now wait 10 hours before the first accounts can be created. This is a function to ensure that all domain controllers have completed replication before the first gMSA accounts are created. This prevents passwords from being generated before all domain controllers are able to respond to password requests / password changes. Even if there is only one domain controller, you still have to wait 10 hours.
Tip: If you don't want to wait 10 hours, you can use the following command, but this only works if there is no KDS root key yet:
Add-KdsRootKey -EffectiveTime (Get-Date).AddHours(-10)
However, the safe way is to wait for the 10 hours and check the successful replication to avoid problems.
Create gMSA accounts
After the 10 hours have passed, new gMSA accounts can be created with the following command:
New-ADServiceAccount -Name msa_ex19ex1 -DNSHostName msa_ex19ex1.frankysweblab.de -PrincipalsAllowedToRetrieveManagedPassword EX19EX1$
The "Name" parameter defines the name of the new account; the name of the account followed by the FQDN of the domain should be selected for the "DNSHostName" parameter. This entry does not have to be created in the DNS. The "PrincipalsAllowedToRetrieveManagedPassword" parameter specifies which servers are allowed to use the account (multiple servers can be specified separated by commas).
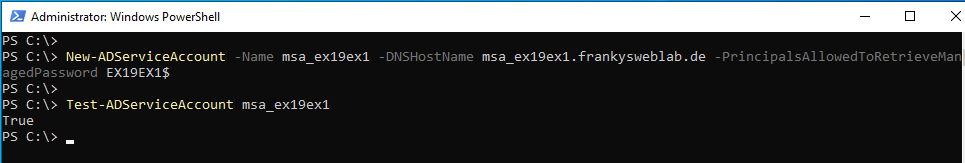
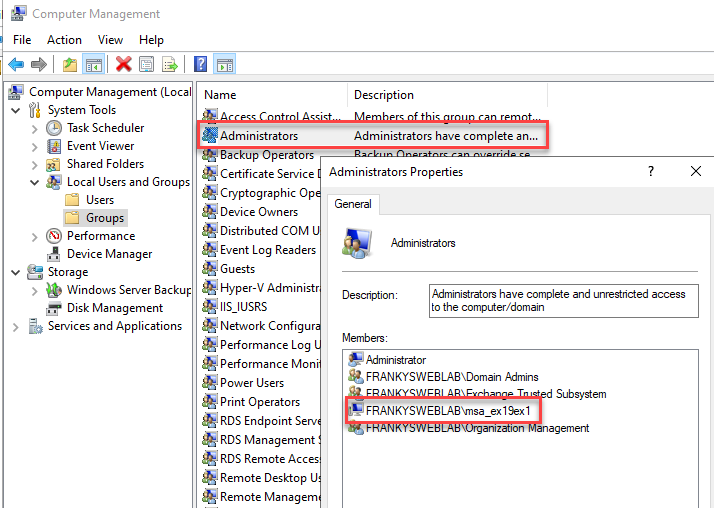
The new account can now be found in the "Managed Service Accounts" OU in the Active Directory:
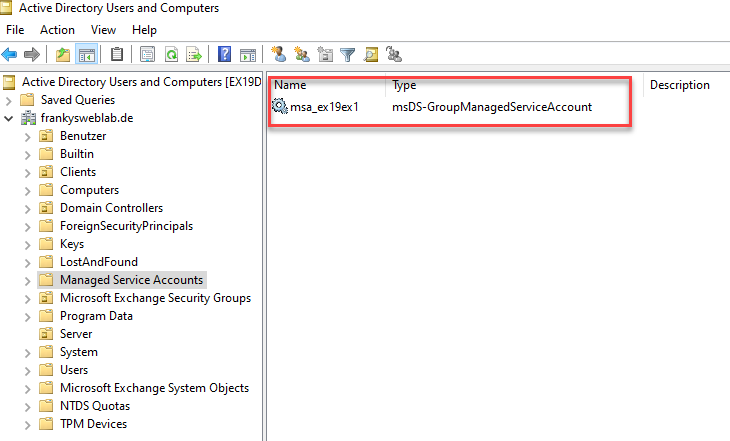
The account can now be assigned the appropriate permissions so that scripts or services can be executed. For example, the gMSA account can now be added to the Exchange group "View-Only Organization Management", so that scripts that require read access to the Exchange organization can be started with this account:
If it is necessary that local administrator rights are required on the server, the account can also be added to the local admin group of the server:
By default, the gMSA account changes its password every 30 days. The password is changed automatically and no manual intervention is required. The following command can be used to create an account with a 60-day password change interval:
New-ADServiceAccount -Name msa_ex19ex1 -DNSHostName msa_ex19ex1.frankysweblab.de -PrincipalsAllowedToRetrieveManagedPassword EX19EX1$ -ManagedPasswordIntervalInDays 60
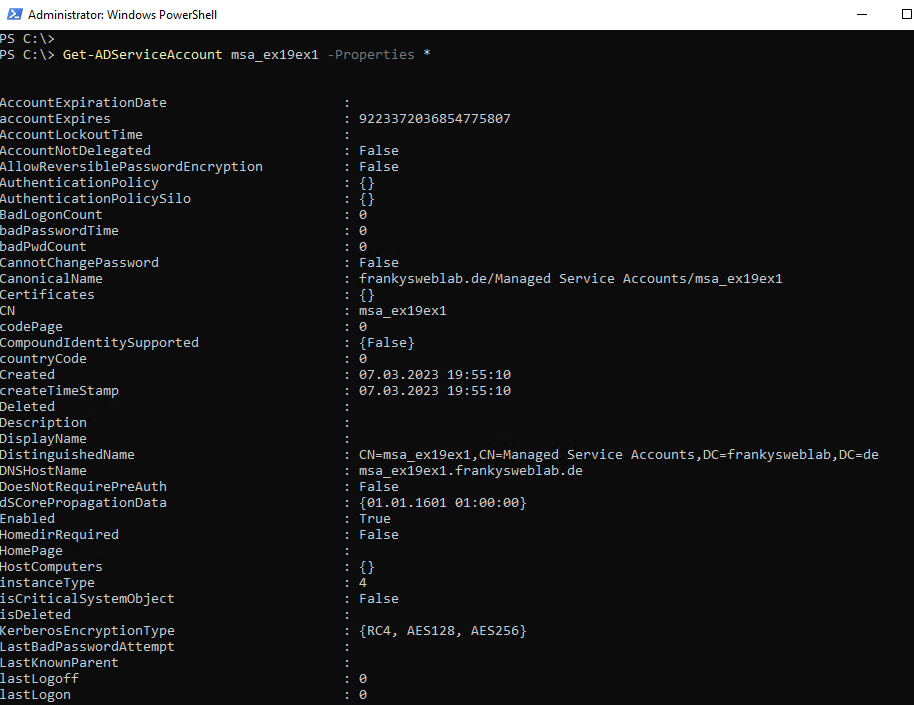
The following command can be used to view all attributes of an account:
Get-ADServiceAccount msa_ex19ex1 -Properties *
Use gMSA accounts
To start a service with a gMSA account, only the corresponding account must be selected, the password field remains empty:
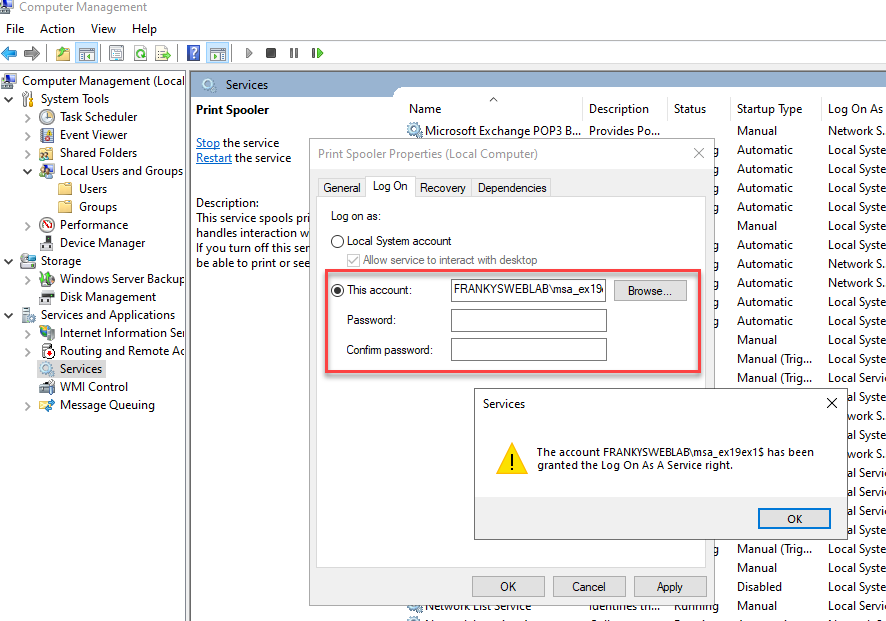
After the service has been restarted, the gMSA account is used. Retrieving and changing the password after the specified time is now done automatically.
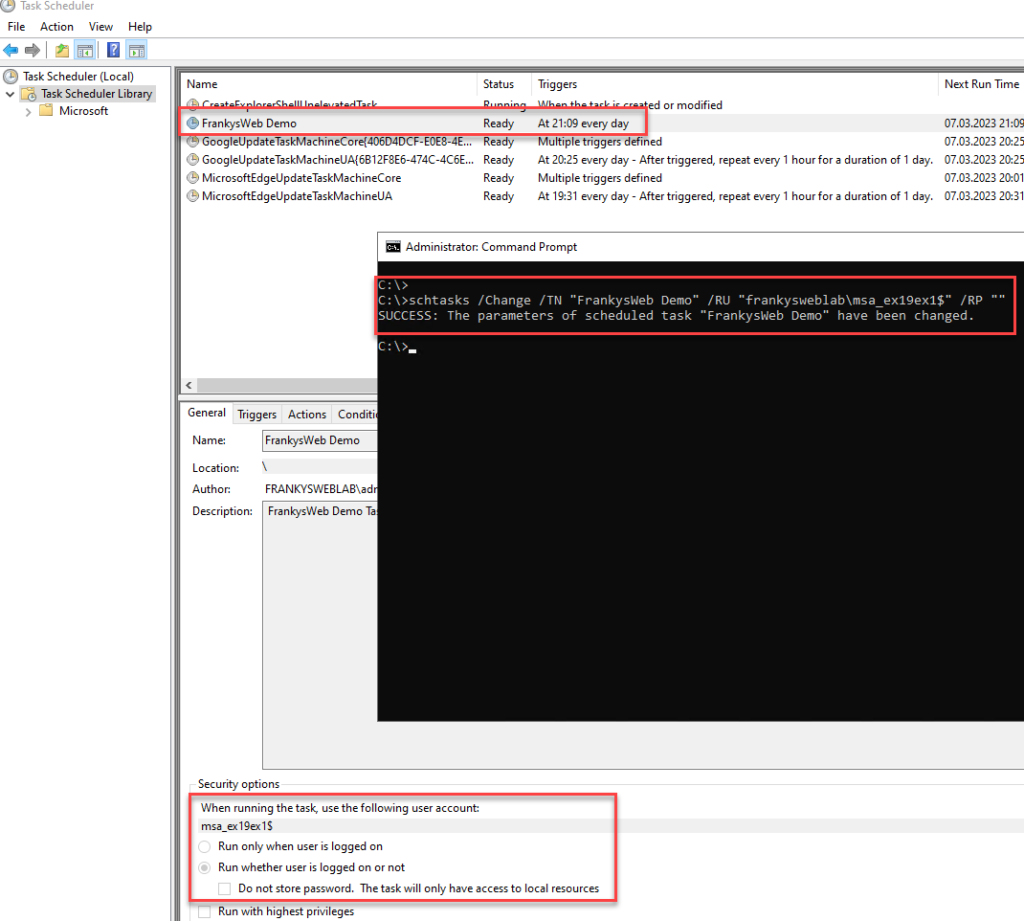
For a scheduled task, assigning the account via the shell works with the following command:
schtasks /Change /TN "FrankysWeb Demo" /RU "frankysweblab\msa_ex19ex1$" /RP ""
Restrictions
Unfortunately, there are also restrictions for gMSA accounts. These accounts are very suitable for scheduled tasks and Windows services, but these accounts cannot be entered and used in applications. For example, many applications require a service account to be able to retrieve information from the Active Directory; these accounts are then usually entered statically in the application. In this case, the automatic password change does not work. In this case, only special, usually quite complex, PAM solutions or good documentation combined with a great deal of discipline and a good audit process can help.

Ich bin neu in dem Thema und habe eine Frage. Wir hatten bisher keine gMSA. Also habe ich wie oben beschrieben den KDSRootkey erzeugt. Eine Abfrage mit Get-KdsRootKey | fl liefert mir 2 Einträge. Einer davon ist der neu erzeugte. Es gibt aber noch einen von 2018 mit folgendem DC:
DomainController : CN=namedesdc\0ADEL:domainid,CN=Deleted Objects,DC=unsere_domäne,DC=de
Dieser DC wurde vor einigen Wochen herabgestuft und durch einen neuen mit dem selben Namen ersetzt.
Test-KdsRootkey gibt für beide KeyIDs den Wert True zurück.
Frage: kann ich diesen alten Key löschen ?
Danke und Grüße,
MG
Ich möchte gMSA verwenden um die WsusDBMaintenance Aufgabe auszuführen.
Mit dem Administratorkonto läuft es.
Nach Umstellung auf gMSA kommt die Fehlermeldung: Es konnte keine Anmeldung gefunden werden, die mit dem angegebenen Namen übereinstimmt. [Client:]
Es ist ein neu installierter Windows Server 2022 mit der Windows internen Datenbank für den WSUS.
Kann mir jemand helfen?
Konntest du es mittlerweile lösen?
Hallo miteinander,
bei mir (Server 2019) besteht das Problem, dass ein Task nicht unter Verwendung der Option „-LogonType Password“ mit Powershell angelegt werden kann. Dann läuft der Task nur, wenn der Service Account angemeldet ist (macht ja wenig Sinn). Die Fehlermeldung sagt falscher User oder Passwort.
Der Fehler bleibt, auch wenn ich erst in der Gui einen Task anlege und ihn später mit
$pric = New-ScheduledTaskPrincipal -UserId domain\service$ -LogonType Password
Set-ScheduledTask -TaskName Name -Principal $pric
ändern will.
Danke
Beste Grüße
Thomas
Hallo Zusammen,
hat jemand RBAC und gMSA aktiv am laufen?
einige Befehle wie Get-Mailbox funktionieren, andere Befehle wie Get-AcceptedDomain, oder Get-MailboxStatistics funktionieren nicht.
Fehler ist wahlweise „Zugriff verweigert“, oder „Objekt nicht gefunden“, je nach Befehl. Der gMSA ist dabei Mitglied von „View-Only Organization Management“ (normaler User darin geht). Sobald der gMSA zur Gruppe Exchange Trusted Subsystem geht auch alles. Ist aber natürlich maximal unschön.
Gruß
Basti
Servus Frank
Das Installieren des MSA auf einem System mit Install-ADServiceAccount ist nicht mehr nötig, oder nicht mehr nötig mit einem gMSA?
LG
Michael
Hallo zusammen,
was macht man wenn man die gMSA nicht einem Task zuordnen kann?
PS C:\Users\XXXXXX> schtasks /Change /TN „Specops Breached Password List Update“ /RU „mydomain\msa.specops$“ /RP „“
ERROR: The user name or password is incorrect.
Den User habe ich wie folgt angelegt:
PS C:\Users\XXXXXX> New-ADServiceAccount -Name msa.specops -DNSHostName msa.specops.mydomain.org -PrincipalsAllowedToRetrieveManagedPassword DC01$,DC02$
Mhhh ggf. liegt ja hier das Problem :/
PS C:\Users\XXXXXX> Test-ADServiceAccount -Identity $MsaIdentity.sAMAccountName
False
WARNING: Test failed for Managed Service Account msa.specops. If standalone Managed Service Account, the account is linked to another computer object in the Active Directory. If group Managed Service Account, either this computer does not have permission to use the group MSA or this computer does not support all the Kerberos encryption types required for the gMSA. See the MSA operational log for more information.
Die vermutlich häufigste Verwendung wird man beim AADC, ADFS und SQL Servern finden. Da gibts dann auch gute Wizards und Anleitungen von Microsoft.