Configuring SCHANNEL settings for SSL 3.0 and TLS 1.0, for example, is possible under Windows using the registry. For a larger number of servers or computers, however, group policies are more suitable for configuration, so I have created corresponding templates that make the settings in the registry.
Foreword
The group policies make changes to the registry on all computers/servers that apply the policy. As problems can occur here depending on the environment, the corresponding settings must be tested carefully.
The changes made to the registry by the GPO remain even after the GPO has been deleted and are not changed back to the default setting. So test extensively beforehand!
In case of problems, the download includes the default registry values for Windows Server 2012 R2 and Windows Server 2008 R2. The .REG files can be merged with the registry to restore the default settings.
Download
The templates for the group policies can be downloaded here:
Enclosed is the HowTo for the creation of corresponding group policies.
Group policy based on an ADM template (ALT)
The classic ADM templates have the advantage that they still work with Windows Server 2003 and Windows XP. Even if Windows 2003 and Windows XP are no longer supported, settings can still be made with the ADM template. However, caution is advised here, as not all settings are supported by Windows Server 2003 and Windows XP. Extensive testing is highly advisable. ADM templates also work with Windows Server 2012 (R2).
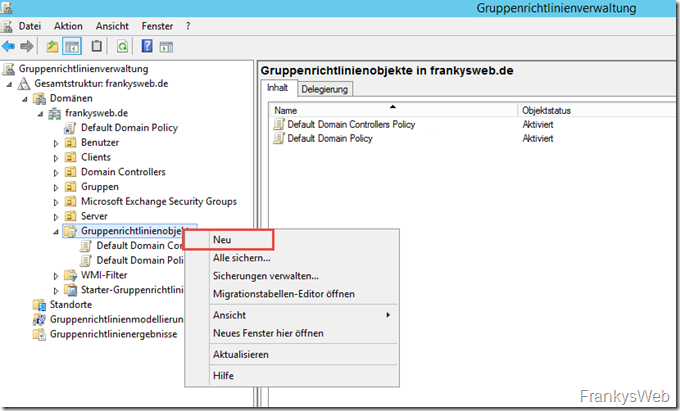
In order for the ADM template to be integrated, a new group policy must first be created in the group policy administration:
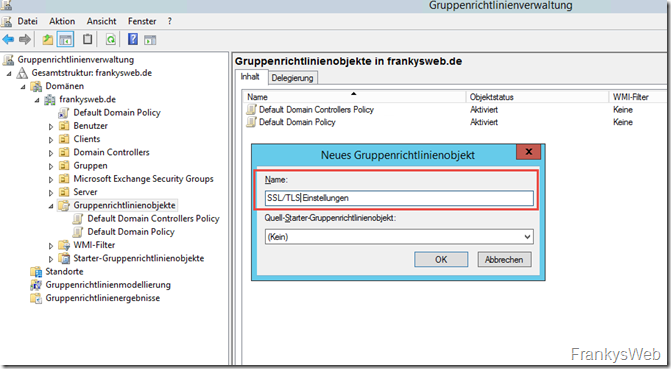
A descriptive name for the future settings is advisable:
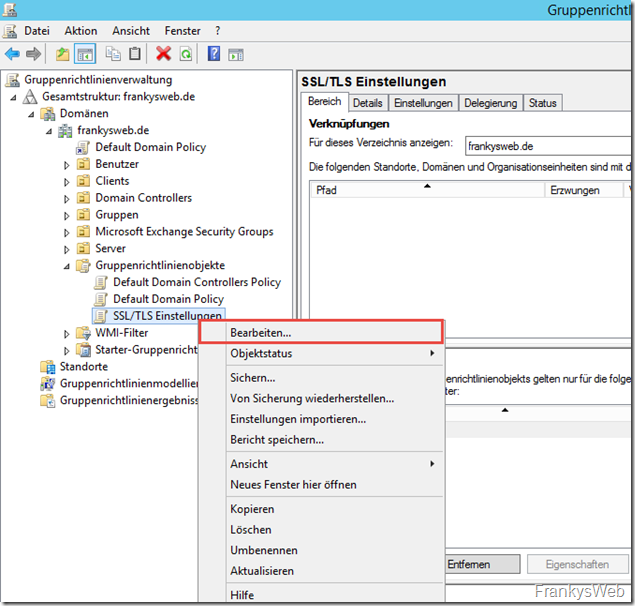
After the group policy has been created, it is edited:
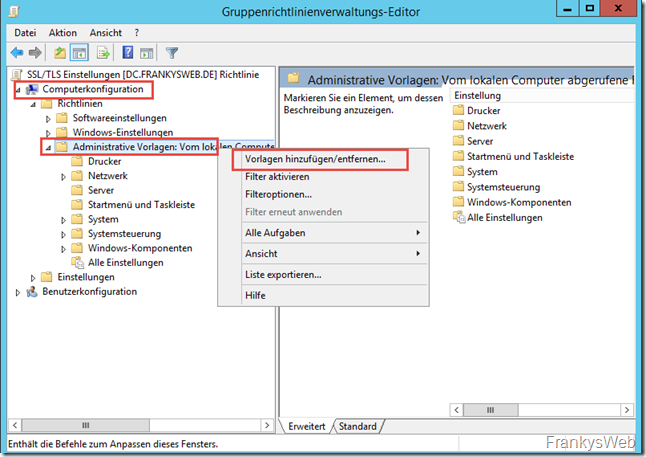
A template can be added by right-clicking under "Computer configuration" / "Administrative templates":
The ADM file is now specified in the following dialog:
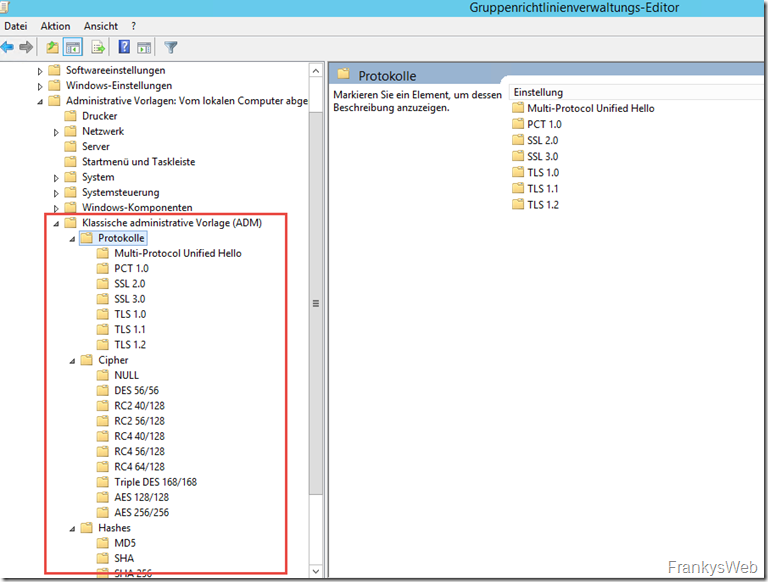
After loading the ADM template, new sub-items with the respective settings are visible:
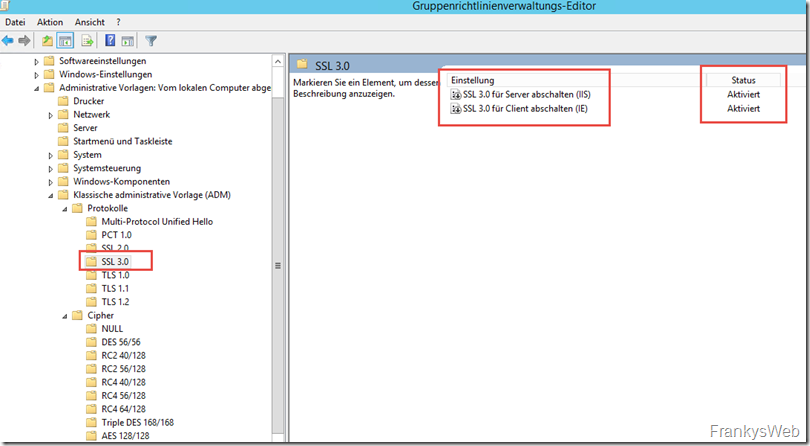
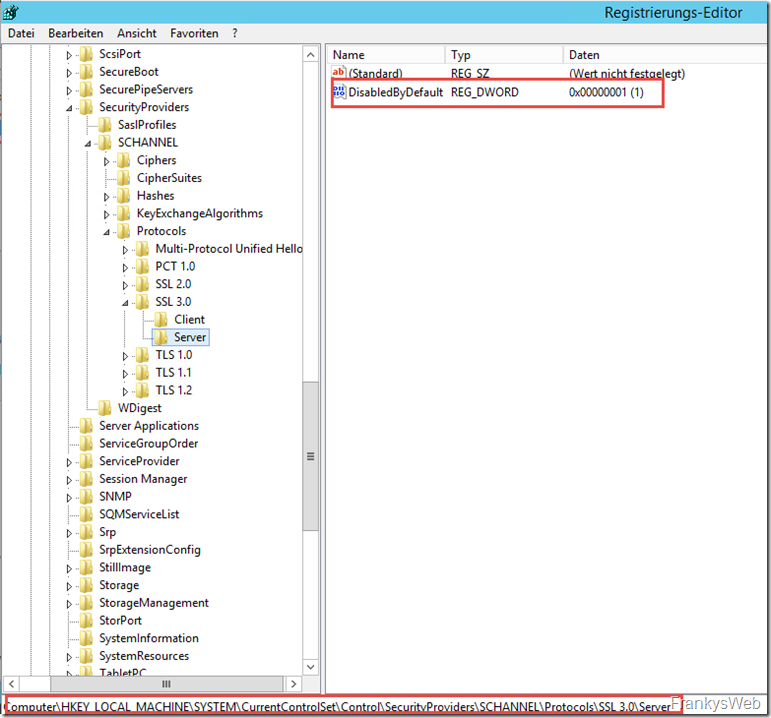
In this example, SSL 3.0 is disabled for servers (IIS web server) and clients (Internet Explorer). As with most guidelines, this must also be read carefully: The setting "Disable SSL 3.0" must be activated to disable SSL 3.0:
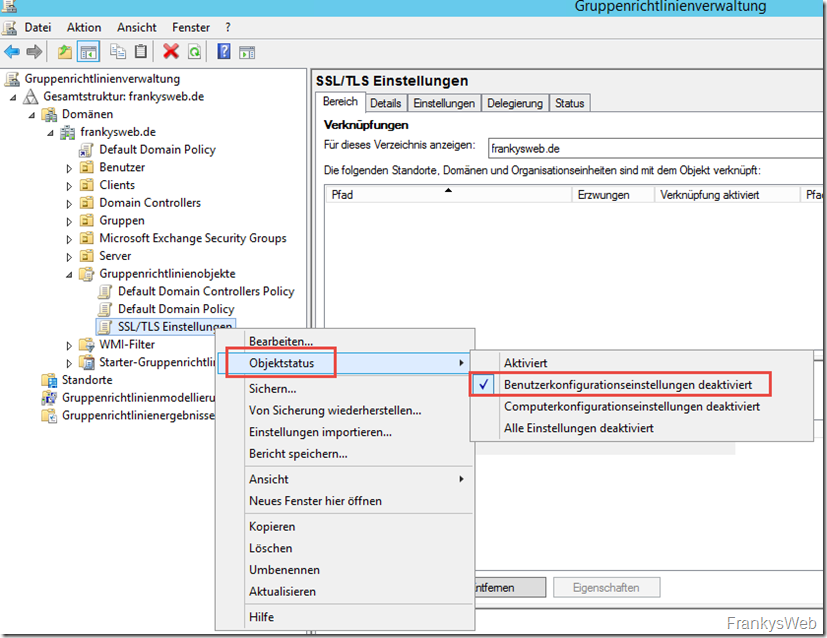
The editor can be closed. In order for the policies to load a little faster, the "User configuration settings" should be deactivated in the group policy administration:
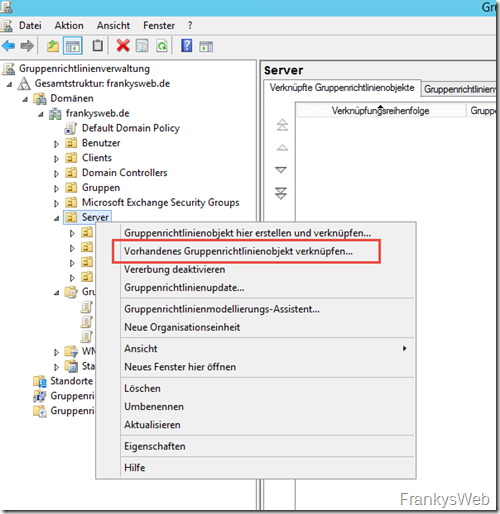
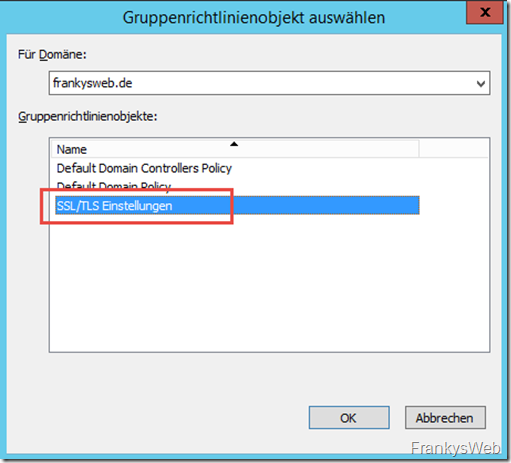
Finally, link the new group policy to a corresponding OU.
Select policy and confirm with OK
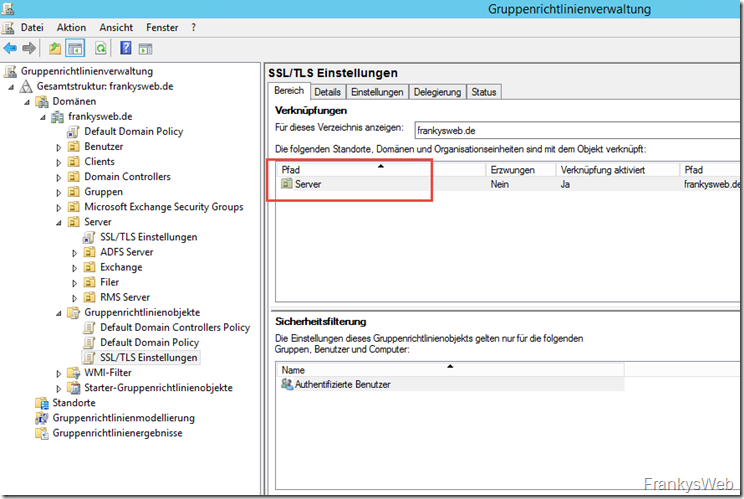
The new group policy is ready
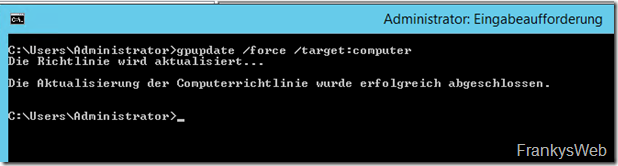
To force the new GPU to be used on a test computer, the following command can be used:
gpoupdate /force /target:computer
The registry can be checked to see whether the corresponding setting has been made:
Finally, the computer must be restarted.
Group policy based on an ADMX template (NEW)
The more modern version of ADM templates are ADMX templates. ADMX templates work from Windows Server 2008 onwards.
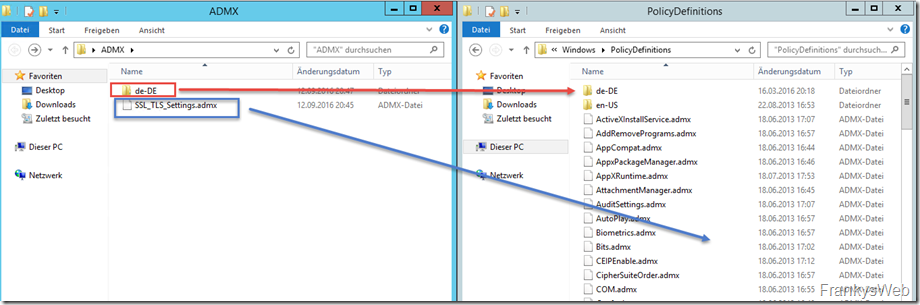
To integrate the ADMX template, the file SSL_TLS_Settings.admx is copied from the ZIP archive to the folder C:\Windows\PolicyDefinitions. The file SSL_TLS_Settings.adml from the subfolder de-DE is copied to C:\Windows\PolicyDefinitions\en-DE:
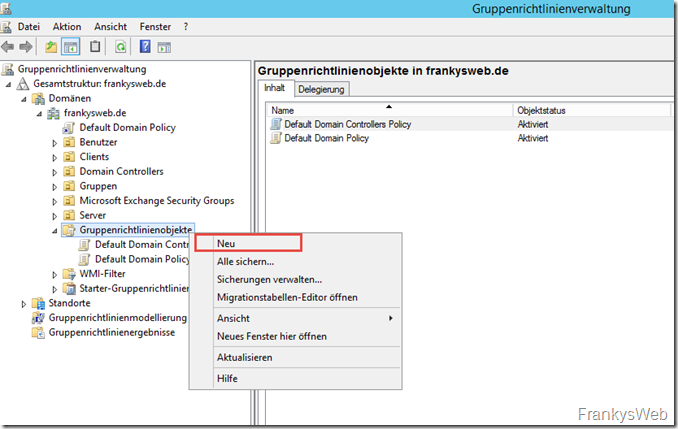
A new group policy can now be created:
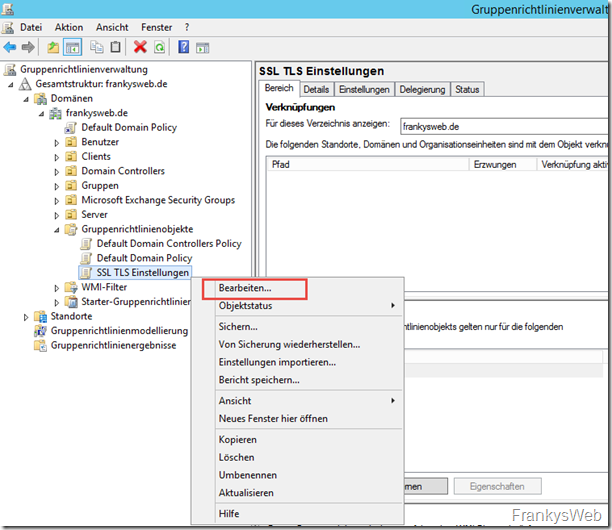
The group policy is edited after it is created:
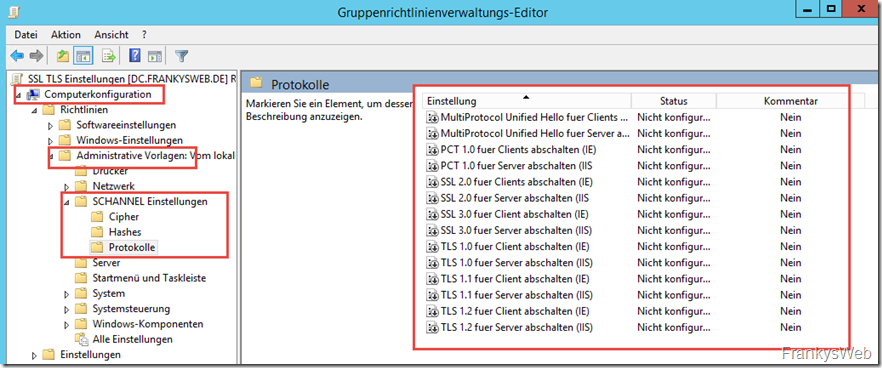
The SCHANNEL settings can now be found in the computer configuration -> Administrative templates -> SCHANNEL settings:
Once the appropriate settings have been made, the rest is again identical to ADM templates (deactivate user configuration settings, link policy, etc.).
Hi Frank,
kann ich das Template auch für Server 2016 und 2019 verwenden oder hast du eine aktualisierte Version?
Danke und Gruß
Bent
Hallo Frank,
ich habe vermutlich auch noch einen Fehler gefunden und zwar muss es bei den Protokollnamen u.A. heißen:
„Multi-Protocol Unified Hello“ im *.adm-file steht allerdings „MultiProtocol Unified Hello“ also ohne den Bindestrich zwischen Multi und Protocol.
Server ist in meinem Fall ein 2008R2 bzw. SBS2011
Gruß
Thomas
Hi Frank,
ich habe dein ADMX File importiert und die Werte gesetzt… allerdings funktioniert bei mir die Umsetzung auf den Windows Server 2008 R2 nicht. Zuvor hatte ich TLS 1.1 / 1.2 manuell eingerichtet über die Registry und es funktionierte einwandfrei. Mit der Richtlinie wollte ich es jetzt etwas komfortabler gestalten. Jedoch klappt das nicht. Jeweils unter TLS 1.1 / TLS 1.2 Client / Server fehlt jetzt der DWORD- Eintrag „DisabledByDefault“. „Enabled“ ist allerdings erfolgreich gesetzt.
Liegt es an einer falschen Einstellung in der GPO oder ist ggf. das ADMX File nicht korrekt?
Vielen Dank,
André