With Windows Server 2016, a new Privileged Access Management feature was introduced, which allows users to be added to a group for a certain period of time only and automatically removed again after this time has expired.
This feature is useful if a user is only to be given administrative rights (e.g. Domain Admin) for a certain period of time. Another use case would be the time-limited inclusion in Exchange distribution groups.
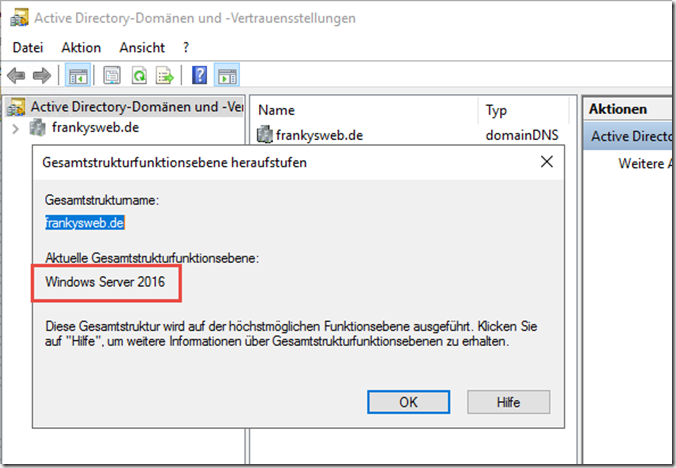
However, the feature is only available if the overall structure function level has already been raised to "Windows Server 2016". In concrete terms, this means that Windows Server 2012 R2 domain controllers must not and cannot be in operation.
In this small example, the overall structure function level has already been raised to Windows Server 2016:
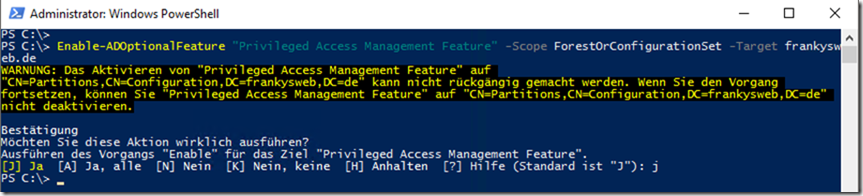
The feature that enables time-limited recording in groups is called the "Privileged Access Management Feature". The feature is optional and must first be activated. Once the Privileged Access Management feature has been activated, it cannot be deactivated again. It is activated using the following command:
Enable-ADOptionalFeature "Privileged Access Management Feature" -Scope ForestOrConfigurationSet -Target frankysweb.de
Once activated, members can be added to groups for a limited time. The type of group is not relevant; these can be security groups or distribution groups.
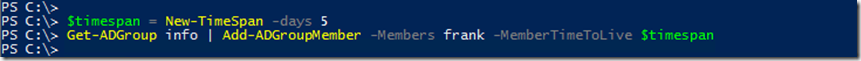
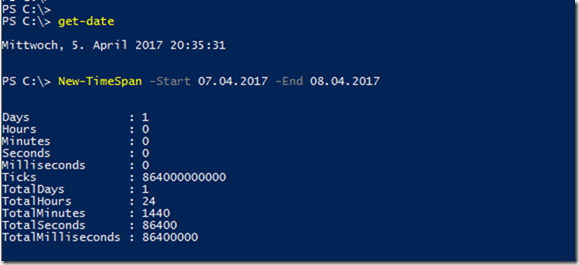
In the following example, the user "Frank" is added to the "Info" group for a period of 5 days:
$timespan = New-TimeSpan -Days 5 Get-ADGroup info | Add-ADGroupMember -Members frank -MemberTimeToLive $timespan
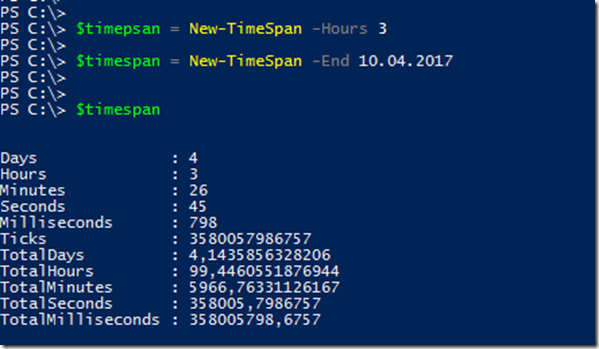
"New-TimeSpan" specifies the time span; hours (-Hours) or an end date (-End) can also be specified here:
However, it is not possible to specify a start and end date in this way. The time period can therefore not be in the future:
The time period shown above would therefore apply for 24 hours when assigning a user and would not start on 07.04.2017, but immediately.
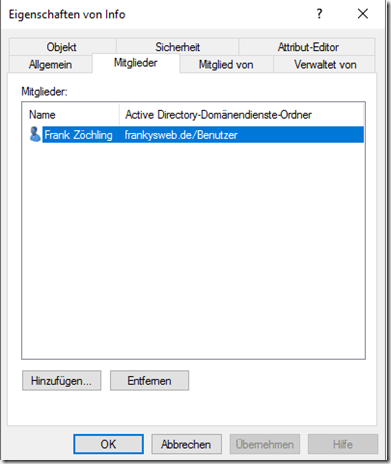
In the "Active Directory Users and Computers" console, it is not clear whether the membership is time-limited:
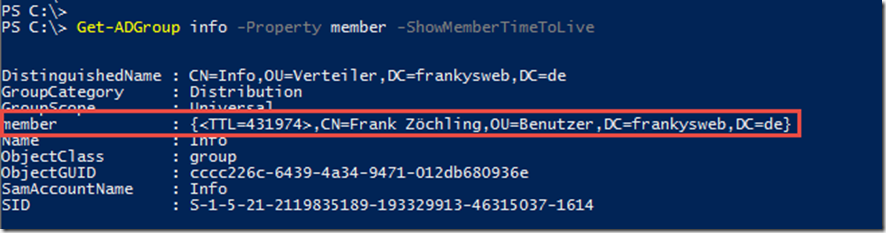
However, the remaining TTL can be displayed using PowerShell. The members and their TTL, if applicable, are specified in seconds:
Get-ADGroup info -Property member -ShowMemberTimeToLive
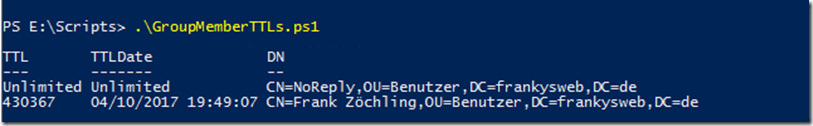
The user "Frank" is therefore still assigned to this group for 431974 seconds. The following script can also be used to make the output a little clearer:
$GroupName = "info"
$GroupMembers = (Get-ADGroup $GroupName -Property member -ShowMemberTimeToLive).Member
$MemberList=@()
foreach ($GroupMember in $GroupMembers)
{
if ($GroupMember -match "TTL=")
{
$TTL = $GroupMember.split(",")[0].split("=")[1].replace(">","")
$TTLDate = (Get-Date).AddSeconds($TTL)
$MemberDN = $GroupMember.Split(">")[1].Replace(",CN", "CN")
$MemberList += new-object PSObject -property @{DN=$MemberDN;TTLDate="$TTLDate";TTL="$TTL"}
}
else
{
$TTL = "Unlimited"
$TTLDate = "Unlimited"
$MemberDN = $GroupMember
$MemberList += new-object PSObject -property @{DN=$MemberDN;TTLDate="$TTLDate";TTL="$TTL"}
}
}
$MemberList
TTLDate is the time at which the user is automatically removed. The assignment to the group is then removed and the user no longer appears as a member of the group:
Now all that remains is to update all domain controllers...
Moin Franky,
wie immer schön flüssig und übersichtlich geschrieben :-) Zu erwähnen wären vielleicht noch zwei Sachen:
1. Im Gegensatz zu einer normalen Gruppenmitgliedschaft beeinflusst die Angabe der TTL auch das Erneuern des Kerberos-Tickets, so dass der User auch aus Sicht seiner lokalen Sitzung sofort aus der Gruppe rausfliegt und nicht im worst case erst 10 Stunden später wie es beim manuellen Entfernen der Fall wäre.
2. Mit Domänen-Admins und anderen hochprivilegierten Gruppen funktioniert der Trick nicht. Die Mitglieder kann man zwar an der PowerShell sehen, die Gruppen kommen aber trotzdem nicht n das Ticken. Ich habe bisher aber keine definitive Info hierzu gefunden…
Danke für die gute Arbeit!
Evgenij
Sehr cooles Feature! Gibt es noch mehr Abhängigkeit wenn man die Gesamtstruktur auf 2016 anhebt? Z. B. Ältere clients?
Mir ist bereits aufgefallen das es ab Server 2016 keine unix Attribute mehr gibt (zumindest keine gui mehr sowie die Login zum hoch zählen) . Da wir diese sehr viel verwenden habe ich das setzen der uids usw via Script gelöst.