Duo makes it very easy to protect OWA in an Exchange on-prem organization with 2-factor authentication. Duo is free for up to 10 users:
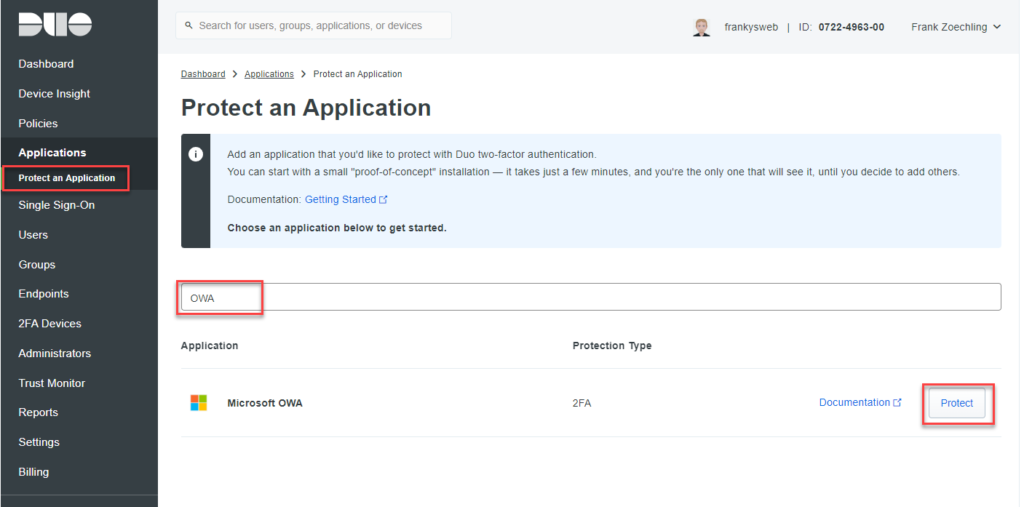
Here is a short how-to for configuration. As soon as you have created a Duo account, you can search for "OWA" in the Admin Portal under "Protect an Application" and click on the "Protect" button:
At the same time, you can download the OWA installer and install it on the Exchange server. The installer can be downloaded here:
The installation is self-explanatory, you just have to click on "Next" a few times:
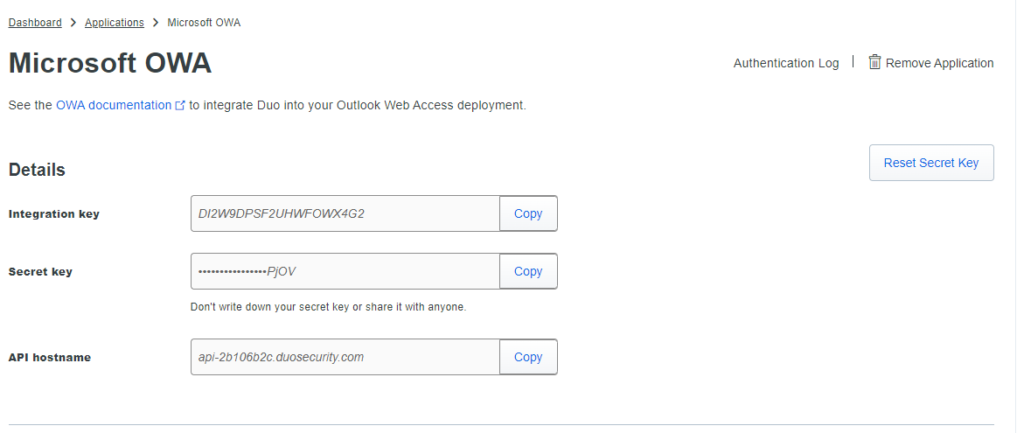
During installation, the details must be copied from the Duo Admin Portal and entered into the installer's installation process:
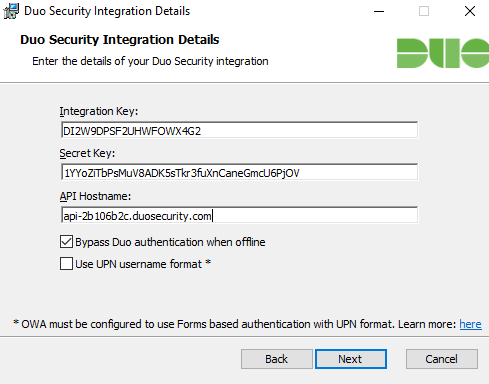
If there are several Exchange servers in the organization, all servers should use the same session key. The following command for the PowerShell creates a session key that can be used for all Exchange servers:
$bytes = new-object "System.Byte[]" 30
(new-object System.Security.Cryptography.RNGCryptoServiceProvider).GetBytes($bytes)
[Convert]::ToBase64String($bytes)
If there is only one Exchange server, the setup can generate a session key:
The installation is now completed:
All you have to do now is click on "Save" in the Duo Admin Portal:
The installation and configuration is now complete. Users can now log in to OWA as usual, but after entering their user name and password they will be prompted to additionally authenticate themselves via Duo.
The first step is the normal login to OWA:
If the user does not yet have the option to authenticate using a second factor, they will be prompted to add a device or a security key:
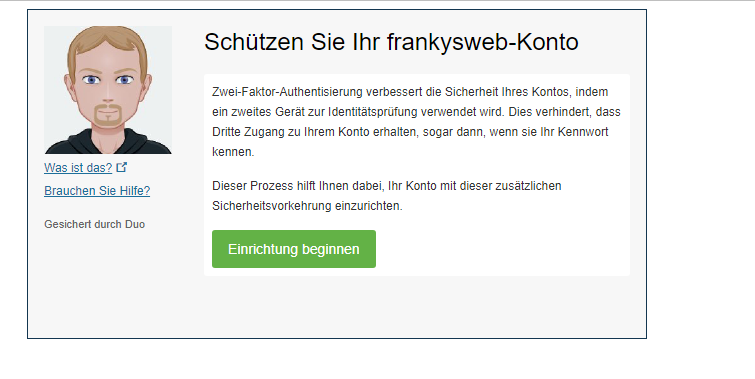
Once the user has completed the setup, they can also use the Duo app for push authentication. It is then no longer necessary to enter a code:
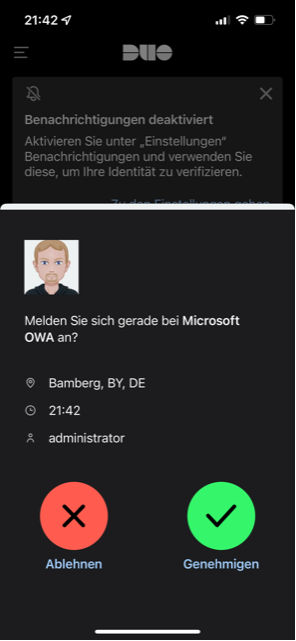
Unfortunately, this 2FA option only works for OWA, not for ActiveSync or Outlook connections. If only OWA is available on the Internet in the organization, Duo, for example, could be used for 2FA. Anyone who has published other Exchange protocols on the Internet should rather switch to "Hybrid Modern Authentication (HMA)". An article on HMA will follow shortly.
Habe ich seit bald zwei Jahren im Einsatz. Läuft absolut geschmeidig. Manchmal kann es nach der Installation eines CU vorkommen, dass man das Setup neu rüberlaufen lassen muss, damit Duo wieder funktioniert. Wichtig dabei ist dann, die .msi als Administrator (über CMD) aufzurufen.
Hi, das kann nicht nur so sein, sondern das ist erforderlich und bei Duo auch so dokumentiert:
https://help.duo.com/s/article/1074?language=en_US
Eine Reparaturinstallation hilft nicht, sondern Deinstallieren und neu Installieren.
Achso, das bezieht sich nur auf CUs. Bei SUs ist es nicht notwendig.
Schöner Artikel, aber ohne die zusätzlichen Dienste nicht wirklich sicherer.
Da könnte auch die sophos mit Waf her halten.
Sollte nicht auch in einer der nächsten Updates for onPrem von Microsoft eine MFA Lösung kommen?