I have already published some approaches to getting the ransomware plague under control here:
- https://www.frankysweb.de/windows-fileserver-vor-ransomware-crypto-locker-schuetzen/
- https://www.frankysweb.de/windows-fileserver-vor-ransomware-schuetzen-update/
- https://www.frankysweb.de/locky-verseuchte-clients-identifizieren/
- https://www.frankysweb.de/clients-vor-infektion-mit-ransomware-schuetzen-locky-cryptolocker/
However, I also receive many emails every day asking what else is possible. I have to say: it depends...
The scripts in the articles do not work in every environment, but probably need to be adapted somewhat. The list of file extensions has also become outdated and needs to be adapted. This needs to be changed from time to time.
I have therefore once the Script from this article slightly adapted to show further possibilities:
$logfile = "c:\Scripts\logfile.csv"
$events = Get-EventLog -LogName application -Source SRMSVC -After (get-date).AddMinutes(-10) | select ReplacementStrings -Unique
if ($events.count -gt 50)
{
stop-computer -force
}
else
{
foreach ($event in $events)
{
$sourceuser = $event.ReplacementStrings[0]
$smbsharepath = $event.ReplacementStrings[1]
#try to find the computer
$openfiles = Get-SmbOpenFile | where {$_.clientusername -like "$sourceuser"}
$PCIP = $openfiles.clientcomputername | select -first 1
$PCFQDN = (Resolve-DnsName $pcip | where {$_.section -match "answer"}).Namehost
$PCUNC = $PCFQDN.split(".")[0]
Output #Infos
write-host "User:" $sourceuser
write-host "Share:" $smbsharepath
write-host "IP of the PC:" $pcip
write-host "FQDN of the PC" $PCFQDN
write-host "PC UNC Name" $PCUNC
#Block share (set share rights for user to deny)
$blockaccess = Get-SmbShare | where {$_.path -like $smbsharepath} | Block-SmbShareAccess -AccountName $sourceuser -Force
$log = "$sourceuser" + ";" + "$smbsharepath" + "$pcname"
$log | add-content $logfile
Shut down #PC of the user
Stop-Computer -ComputerName $PCUNC -force
#Block user account (AD module required for PowerShell)
Get-ADUser $sourceuser | Disable-ADAccount
}
}
The script returns the recognized values, something like this:
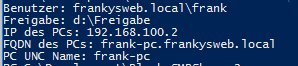
Whether you block the user account in the Active Directory, shut down the user's PC, shut down the file server or deny access rights to the share is up to you. Of course, these methods can also backfire: User accidentally or intentionally saves a file with a corresponding change on a share and shuts down the file server(s)...
So there are many things that have to be taken into account, you could also only have an e-mail sent when a corresponding file is found, it's just stupid if the e-mail is not read at night. But you could adapt the script to the business hours: Within business hours: Mail to the admin, Outside business hours: Shut down the user's PC.
Everything conceivable, everything feasible, with a little PowerShell...
Oh yes, what is also quite helpful: A good and CURRENT backup! When was the last time the restore was tested? J
And that brings us to the next point: If encryption cannot be prevented with certainty, then I have to make sure that data loss is kept to a minimum if the worst comes to the worst. Here you could also think about Windows VSS snapshots. For example, a small script that triggers a VSS snapshot every 30 minutes and leaves 4 versions, for example.
In general, every file server admin needs to think about how best to protect themselves against ransomware. "Money for data" could become the new "penis extension". But nobody falls for emails with "penis extension" anymore...
Initial tests of the Malware Bytes beta also look very promising:
https://forums.malwarebytes.org/index.php?/topic/177751-introducing-malwarebytes-anti-ransomware/
So it remains exciting...
Leider funktioniert das so nicht, mit dem Sperren des Users.
Die Variable $sourceuser wirft DOMÄNE\BENUTZER als Ergebnis aus. Zu sehen oben im Bild von Franky.
Der Befehl Get-ADUser mit oder ohne „-Identity“ kann nur den samAccountName auslesen. Es darf keine Domäne mit drin stehen! Alternativ GUID auch möglich.
Schade
Wo bekommt man denn immer die neueste Liste mit den Dateiendungen??
Eine zusätzliche Sicherheit bringt auch Applocker, allerdings nur sofern diese Funktionalität genutzt werden kann (Stichwort Enterprise / Ultimate). Applocker kann bequem über die Gruppenrichtlinien verwaltet werden.