In a previous article I described where the AMSI log files of the Exchange server can be found. Since the logs are stored locally on the Exchange server, the logs are of little use if nobody reads them and attacks are only detected when it is too late.
However, the logs can also be read in a simple way with PowerShell and thus processed further as required. I have created a small PowerShell function to evaluate the AMSI or HttpRequestFiltering logs:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 | {[()]([(,)]$_ })]){() {= (6 | {$_ }) ','|{$_}}}} |
The function can be easily added to PowerShell and then used:
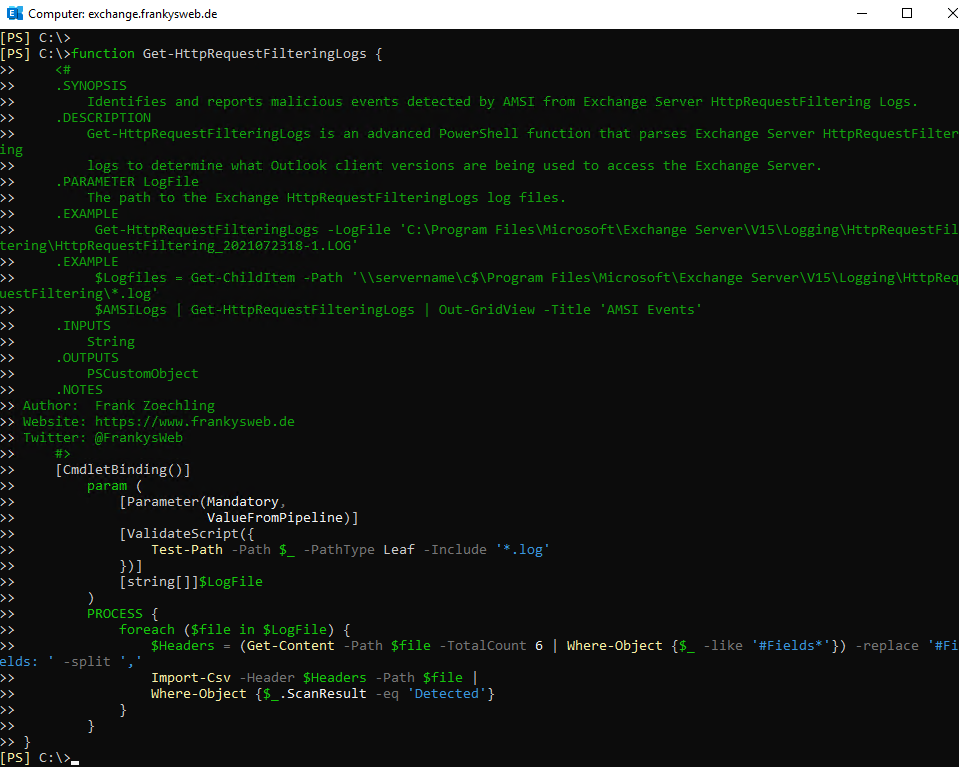
I have provided corresponding examples for the syntax:
1 | |
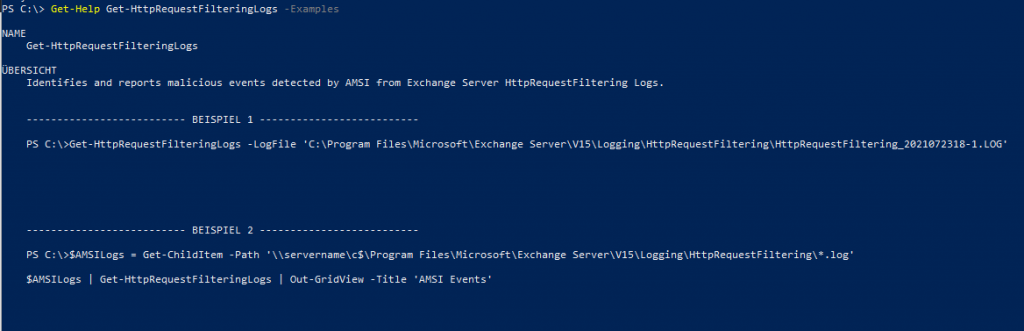
The function can be used to read individual log files or several log files, example 1 shows a single log file, the second example shows the reading of several log files. Here is an example:
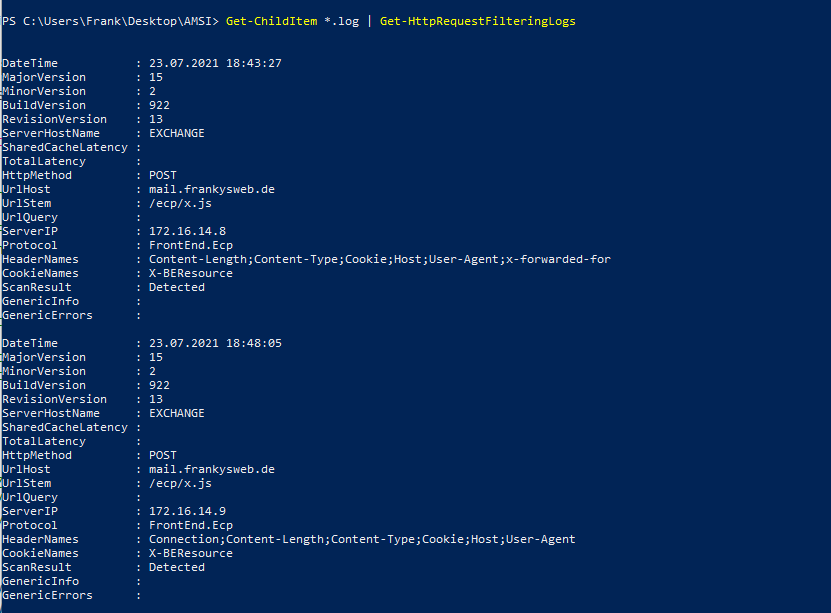
In this way, logs within a certain period can be filtered and read in and the output displayed in a GridView. Here, for example, the logs of the last 7 days:
Get-ChildItem *.log | where {$_.LastWriteTime -gt ((get-date).AddDays(-7))} | Get-HttpRequestFilteringLogs | Out-GridViewThe result then looks like this, for example:
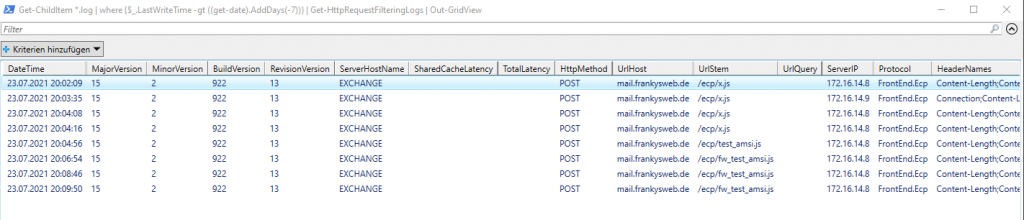
In this way, the AMSI logs can also be sent to other systems and processed further.
Parameter -logfile ist für powershell unbekannt, bei mir funktioniert daher nur example 2
Grüße!
bei uns ist das Verzeichnis leer. Test PS erzeugt eine Datei also muss AMSI aktiv sein. Wir haben Defender am Server. Kann es sein, dass nur positive Treffer geloggt werden.
Thank you for article