In addition to Windows 10, Windows Server 2016 also transfers a lot of data to Microsoft. In many companies, this chatty behavior of the current Windows versions is probably undesirable. Microsoft seems to be well aware of this and has published extensive documentation on which services transfer data to Microsoft.
The documentation is available here:
Manage connections from Windows operating system components to Microsoft services
The list is quite long for Windows Server 2016 alone. I have therefore created a template for a group policy for data protection that already contains most of the settings suggested by Microsoft.
I have left the following points from the above document untouched:
- NTP settings
- Windows Defender settings
- Microsoft Edge settings
This template can save some work, but extensive testing is unavoidable.
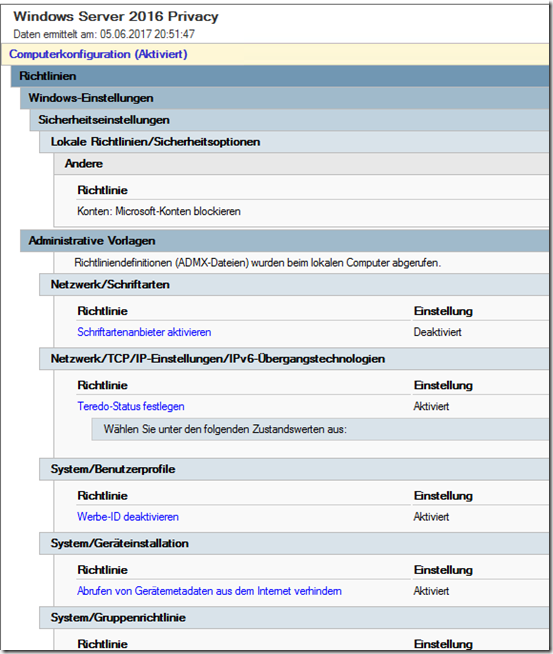
Template settings
- The following settings are included in the template:
- Accounts: Block Microsoft accounts
- Activate font provider
- Set Teredo status
- Deactivate advertising ID
- Prevent retrieval of device metadata from the Internet
- Continue experiences on this device
- Deactivate active tests of the Windows network connection status display
- Configure Windows SmartScreen
- Switch off user control for Insider builds
- Do not allow telemetry
- Deactivate joining Microsoft MAPS
- Send file examples if further analysis is required Deactivate
- Deactivate "Suggested sites"
- Deactivate AutoComplete for web addresses
- Deactivate browser geolocation
- For Microsoft services, do not allow advanced suggestions to be provided when users enter text in the address bar
- Prevent management of SmartScreen filters
- SmartScreen filter mode
- Disable background loading of websites and content to optimize performance
- Deactivate page forward with page prediction
- Deactivate compatibility view
- Preventing the use of OneDrive for file storage
- Prevent automatic detection of feeds and web slices
- Deactivate background synchronization for feeds and web slices
- Switch off AVS online check for KMS client
- Deactivate all apps from the Windows Store
- Deactivate automatic download and installation of updates
- Do not allow Cortana on the lock screen
- Do not allow Cortana
- Do not allow search and Cortana to use location data
- Defining the information to be released in the search
- Do not search the web and do not display web results in the search
- Do not allow web search
- Do not send any additional data
- Deactivate Windows error reporting
Settings can be verified during the import. After the import, the settings can be adapted to your own requirements.
Download
The template for the group policy for data protection for Windows Server 2016 can be downloaded here:
The template can be unpacked on a domain controller. The archive also contains an HTML file with the template settings. The import of the settings is described in the next section.
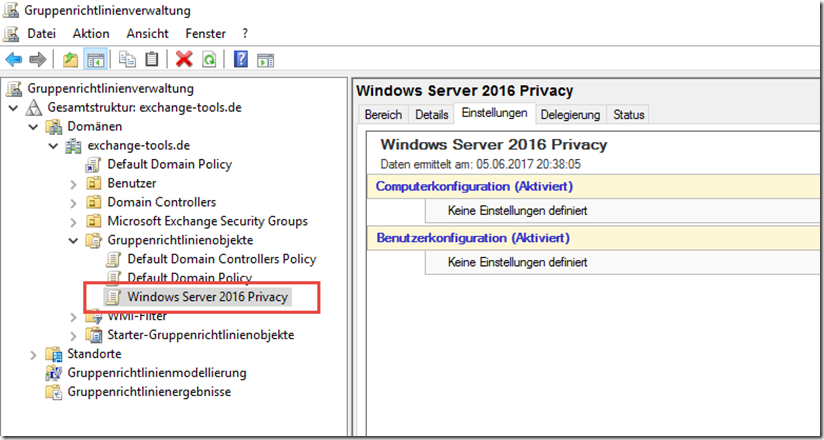
Import group policy
To import the group policy settings, an empty group policy must first be created:
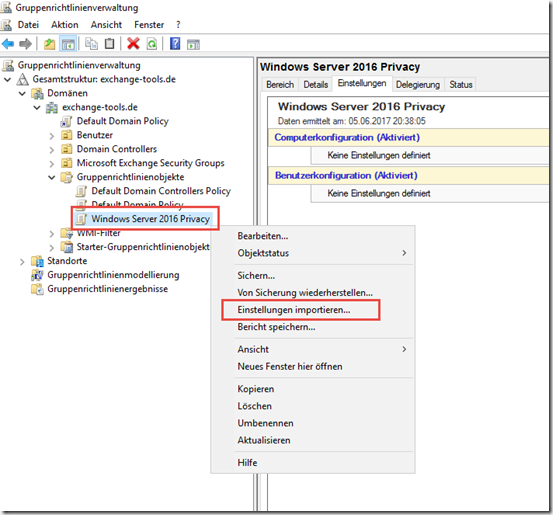
The "Import settings" option can be found in the context menu of the new group policy:
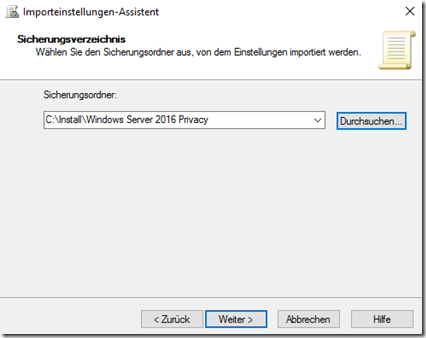
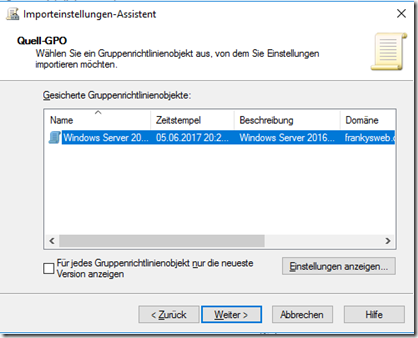
The import settings wizard opens, in the course of which the path to the directory of the group policy with the default settings can be specified:
In the next window of the wizard, you can display the settings and import the policy:
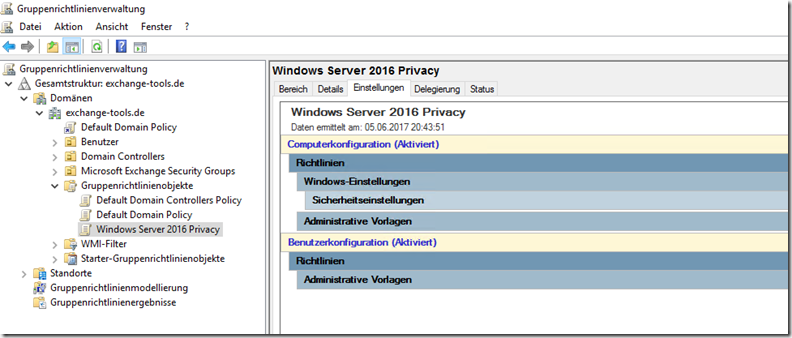
As soon as the group policy has been imported, the settings are stored in the newly created group policy:
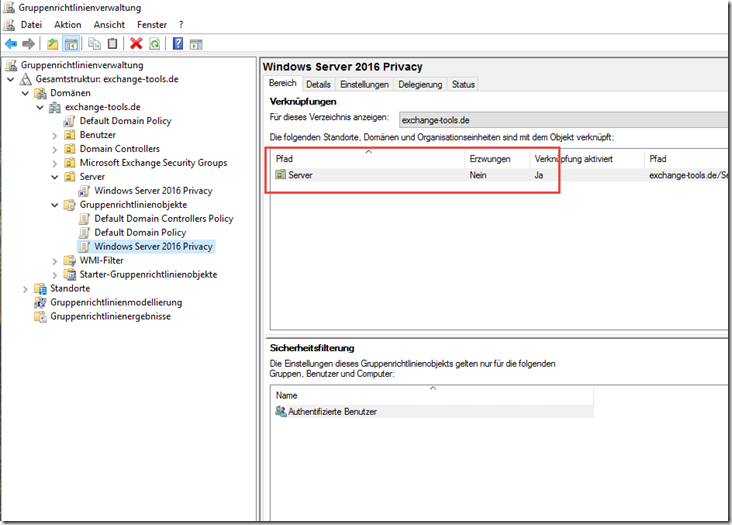
The new group policy now only needs to be linked to an organizational unit:
Optionally, the selection can also be restricted using a WMI filter so that the policy is only applied to Server 2016.
Hallo, schöner Beitrag… ;-) Leider kann ich die Vorlage (ZIP) nicht laden.
Hallo Maik,
probier es noch einmal aus, ich denke das war nur ein temporäres Problem. Bei mir funktioniert der Download.
Gruß,
Frank
Hi Frank,
untere Einstellung ist bei deiner GPO aktiviert, soll das so sein?
Alle Apps aus dem Windows Store deaktivieren:
Wenn Sie die Einstellung deaktivieren, werden alle vorinstallierten oder heruntergeladenen Windows Store-Apps am Start gehindert. Die Apps werden nicht aktualisiert, und darüber hinaus wird der Store deaktiviert. Wenn Sie die Option aktivieren, werden Apps und Store wieder aktiviert. Diese Einstellung gilt nur für die Enterprise- und Education-Edition von Windows.