Anyone who has not yet thought about exchanging their SHA1 certificates for SHA256 (also known as SHA2) should not let too much time pass.
Microsoft has announced that it will no longer support SHA1 certificates from June 2016 and will therefore block them. A corresponding entry can be found here:
http://blogs.windows.com/msedgedev/2015/11/04/sha-1-deprecation-update/
Mozilla has also already announced a similar procedure for Firefox:
https://blog.mozilla.org/security/2015/10/20/continuing-to-phase-out-sha-1-certificates/
Just like Google for Chrome:
https://groups.google.com/a/chromium.org/forum/#!msg/blink-dev/2-R4XziFc7A/YO0ZSrX_X4wJ
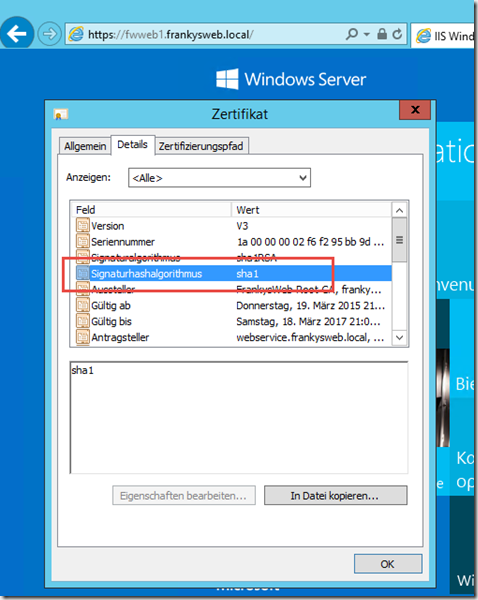
Specifically, we are talking about SHA1 as a signature hash algorithm:
From January 2016, Internet Explorer will issue a certificate warning for certificates signed with SHA1. It was previously planned that SHA1 would no longer be supported from January 2017. This date has now been brought forward to June 2016. The reason for this is that SHA1-signed certificates have been considered insecure for a long time:
https://sites.google.com/site/itstheshappening/
And by a long time, I mean a very long time: (The article is from 2005)
http://www.heise.de/newsticker/meldung/Kryptoverfahren-SHA-1-geknackt-135372.html
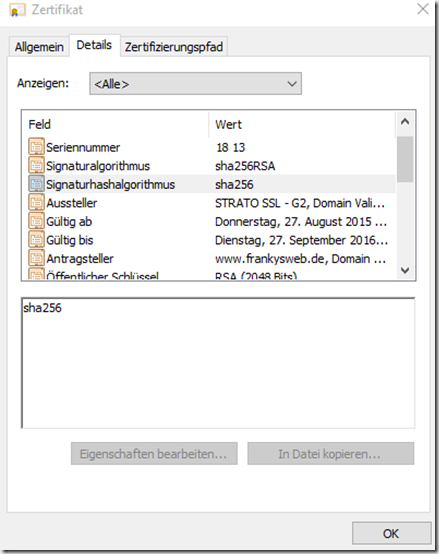
Most public CAs already only issue SHA2 certificates. The public CAs often also offer to exchange existing SHA1 certificates free of charge. This is particularly easy with certificates obtained via the reseller PSW. All you have to do is submit the order number and a new CSR and you will receive a new certificate:
https://www.psw-group.de/ssl-zertifikate/austausch/
With the CAs directly, it is somewhat more complex, but just as possible:
Certificates issued by an internal certification authority are also affected. In order for a Windows CA to be able to issue SHA2 certificates, in most cases only the signature hash algorithm needs to be changed. I have described how to do this here:
https://www.frankysweb.de/migration-stammzertifizierungsstelle-sha1-zu-sha256-hashalgorithmus/
By the way: My site is also accessible in encrypted form (of course already with SHA2)
Another important note at the end:
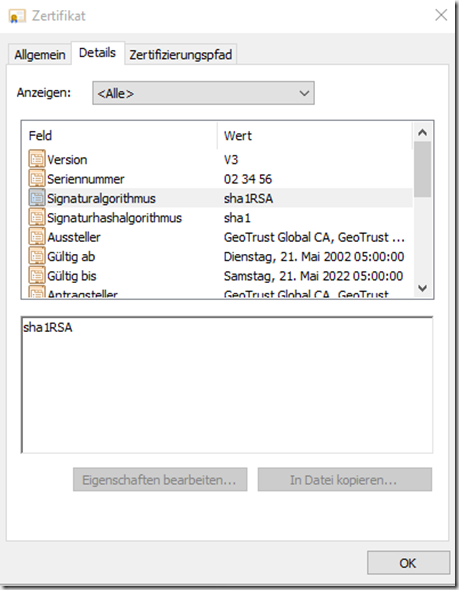
The announcement that SHA1 will no longer be supported relates to the web servers or TLS certificates, not to the certificates of the certification authorities themselves. The root CAs may continue to be signed with SHA1. The example of GeoTrust can also be seen here:

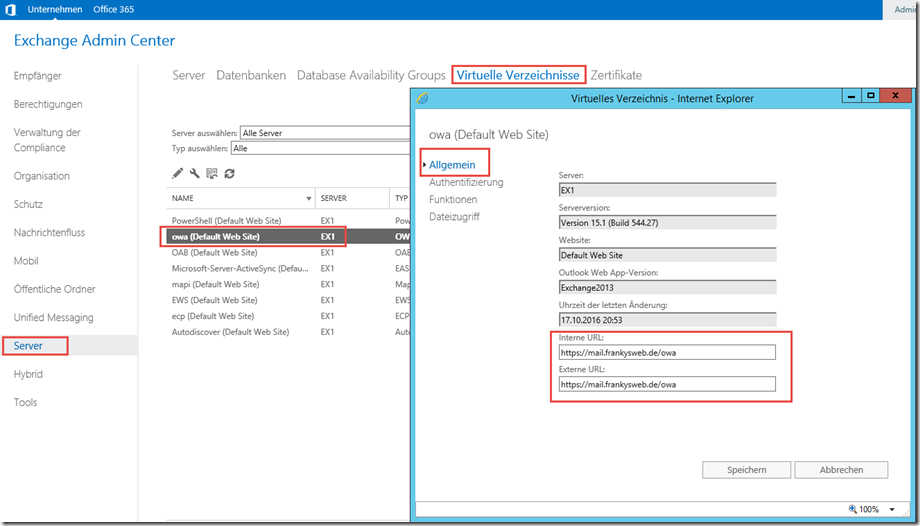
Hallo Frank,
wohl dem der eine PKI betreibt… Ich meine natürlich alle, die lediglich mit selbst-signierten Zertifikaten arbeiten.
Gruß Marco
Hallo Frank,
guter Hinweis… Ob Microsoft an die selbst-signierten Exchange Zertifikate gedacht hat, die bis heute mit sha1 Algorithmus ausgestellt werden? Oder kennst du einen Weg, diese auf sha2 umzustellen?
Grüsse
Hallo Marco,
wieso sollte man an die Zertifikate denken? Man tauscht das Standard Zertifikat einfach aus. Link steht im Artikel.
Gruss, Frank