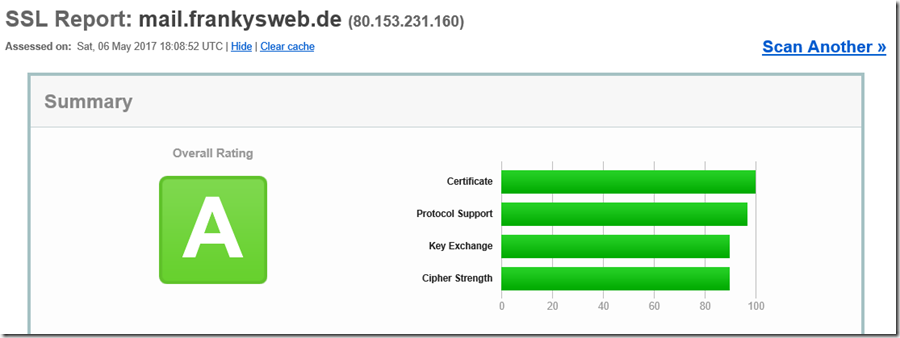
Sophos has recently released the update to version 9.5 for the UTM. One of the new features of UTM 9.5 is the ability to set the TLS version for the web application firewall. However, this is not yet sufficient for the SSL Server Test to receive an A+ rating from Qualys SSL Labs.
An A rating is not necessarily bad, but A+ would be better. So here is my configuration (not supported by Sophos):
Use TLS v1.1 or higher
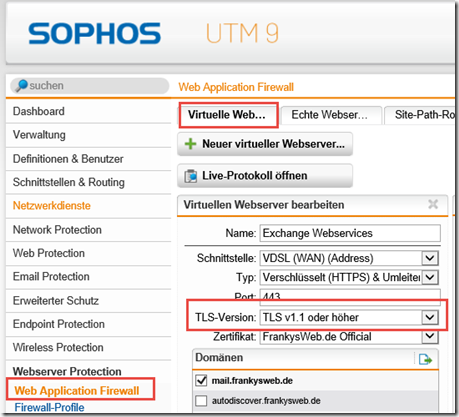
With Sophos UTM 9.5, the TLS version for the virtual web server can now be set; with previous UTM versions, this was not possible via the GUI:
This is a step forward, as TLS 1.0 was still permitted in the default setting. With the setting shown above, it is now at least possible to only use TLS version 1.1 or higher.
To achieve the A+ rating, the setting "TLS v1.1 or higher" must be selected here.
Only use strong ciphers
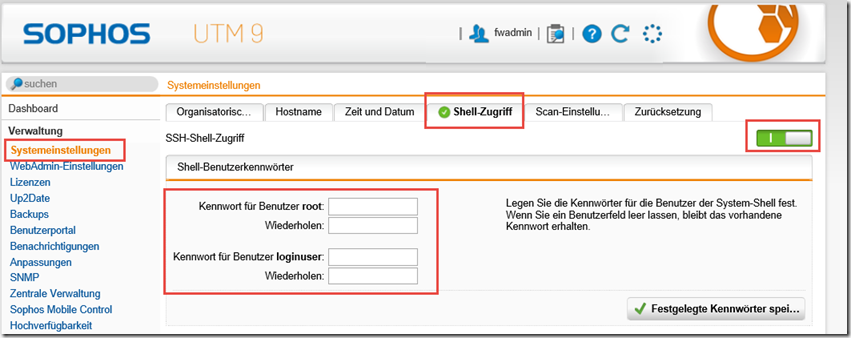
By default, the UTM still offers two cipher suites, which are no longer completely up to date. Unfortunately, the ciphers can only be changed via shell, which has disadvantages (see end of article).
To change the cipher, you must first log in to the UTM via SSH, for which SSH must be activated:
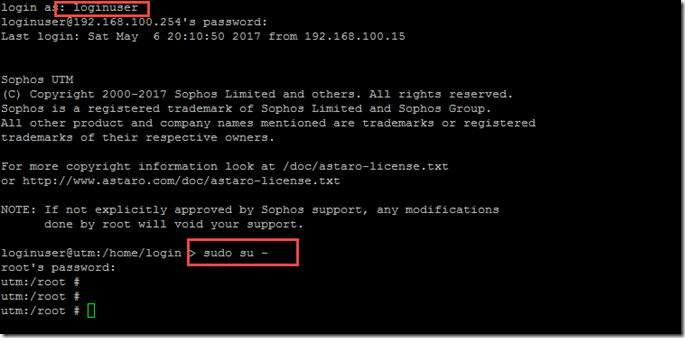
You can then log in to the UTM via SSH with the user "loginuser". The command "sudo su -" is used to obtain root rights:
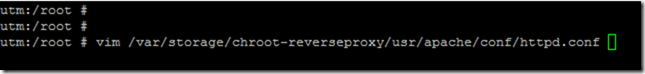
The following file is now opened with vim:
vim /var/storage/chroot-reverseproxy/usr/apache/conf/httpd.conf
Now search for the line with the following content:
SSLCipherSuite ECDH+AESGCM:DH+AESGCM:ECDH+AES256:DH+AES256:ECDH+AES128:DH+AES:RSA+AESGCM:RSA+AES:ECDH+3DES:DH+3DES:RSA+3DES:!aNULL:!MD5:!DSS
and replaces the line with the following content:
SSLCipherSuite ECDH+AESGCM:DH+AESGCM:ECDH+AES256:DH+AES256:ECDH+AES128:DH+AES:RSA+AES:!ADH:!AECDH:!MD5:!DSS:!3DES
This deactivates all weak ciphers. The file can be saved and closed. The shell is also required for the next step.
Activate HTTP Strict Transport Security (HSTS)
HSTS must also be activated via the shell for the A+ rating. A short description of HSTS can be found on Wikipedia.
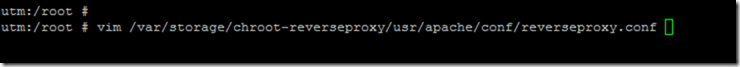
To activate HSTS, the following file must be opened via VIM:
vim /var/storage/chroot-reverseproxy/usr/apache/conf/reverseproxy.conf
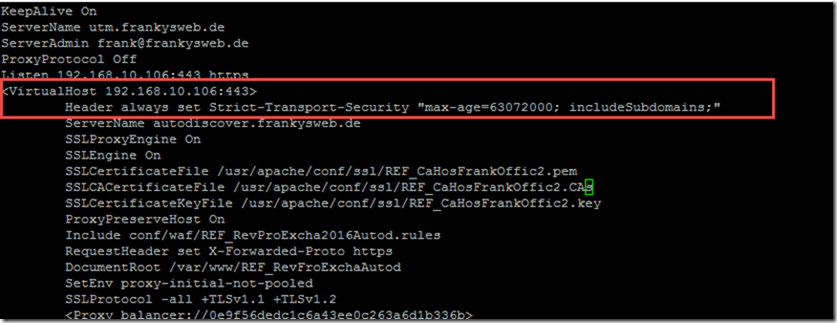
The following line must now be added to the configuration for each virtual host that is accessible via HTTPS (port 443):
Header always set Strict-Transport-Security "max-age=63072000; includeSubdomains;"
The entries can occur several times depending on the configuration of the WAF; all servers that are to receive an A+ rating require the HSTS entry.
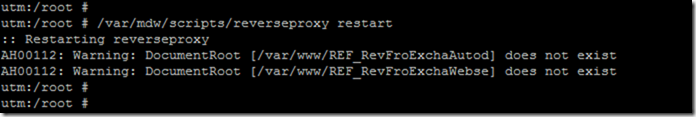
In order for the changes to the cipher and the VirtualHost configuration to take effect, the reverse proxy must be restarted:
/var/mdw/scripts/reverseproxy restart
Incidentally, the two warnings already appeared before and have nothing to do with the changed settings.
SSL Server Test from Qualys SSL Labs
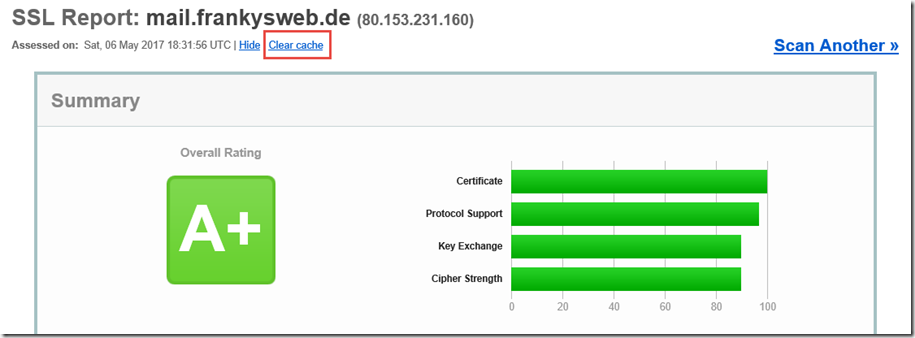
After all settings have been made as described above and the certificate has been issued by a public CA, Qualys SSL Labs issues the A+ rating:
If the test has been started several times, the "Clear Cache" link must be clicked so that the test is repeated.
Disadvantages
The change via shell is not supported by Sophos, in my environment I can still get over this disadvantage, but in productive environments this is a showstopper.
Another disadvantage: As soon as the WAF configuration is changed via the GUI, the manual changes made via the shell are no longer valid and are overwritten, meaning that the A+ rating is lost again.
The question remains as to why Sophos does not make these fairly simple steps available in the GUI. This should not really be a major effort.
Hallo Frank,
sag mal, kennst du ein persistentes Verzeichnis auf der UTM?
Man könnte dieses Problem hier mit einem cronjob in der cron.misc Datei „Workaround/Hotfixen“ wenn man nur irgendwo ein Script ablegen könnte, dass nicht nach jedem Neustart gelöscht wird.
A+ Ratings bekomme ich mit über WAF (UTM 9.3) veröffentlichte Apachen bereits jetzt schon, wenn ich HSTS und HPKP im Apache nutze (Test für IIS stehen noch aus). Die WAF scheint die Header des Webserver bisher wenig zu beeinflussen. Hier Einstellungen zu setzten ist sicher eleganter. Grade eine Verwaltung für https key pins würde sich lohnen.