In Article 2 I had already written my opinion on RPCoverHTTP (Outlook Anywhere) in conjunction with Sophos XG and two public DNS names. Here again briefly for repetition:
The background to this is that most of the web server protection mechanisms for Outlook Anywhere must be switched off. This then also applies to the remaining web services such as OWA and EWS. If Outlook Anywhere, i.e. the classic RPCoverHTTP, is still required, I recommend adding a third host name to the certificate (e.g. rpc.frankysweb.de) and adapting the Exchange configuration to this host name (as also provided by Sophos).
However, I have received a few emails in which exactly this configuration is required. The background to most of the emails is relatively simple: Exchange 2010 is still in use and does not yet speak MAPIoverHTTP. In some cases, the certificate has also just been renewed, which means that replacing the certificate with one with three DNS names is not possible without additional costs.
So I was tempted to publish the corresponding configuration with two DNS names and Exchange 2016. I have not yet tested whether this configuration also works with Exchange 2010.
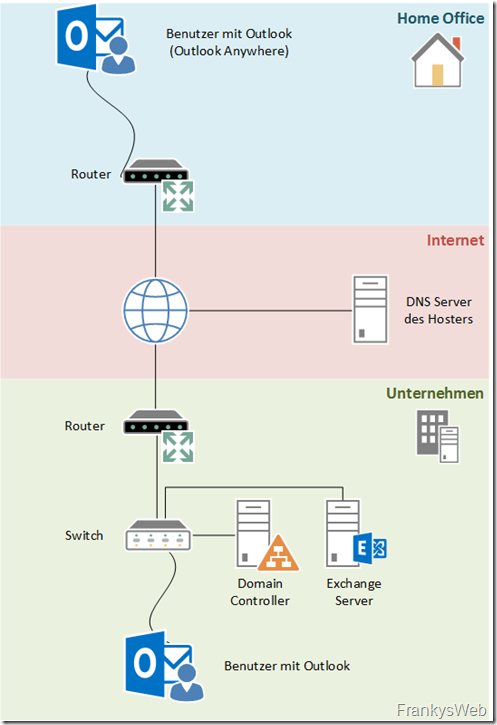
This configuration is based directly on the configuration described Part 1 and Part 2 on.
Customization for RPCoverHTTP (Outlook Anywhere)
The existing firewall rule "Exchange 2016 Webservices" must be edited to also support Outlook Anywhere:
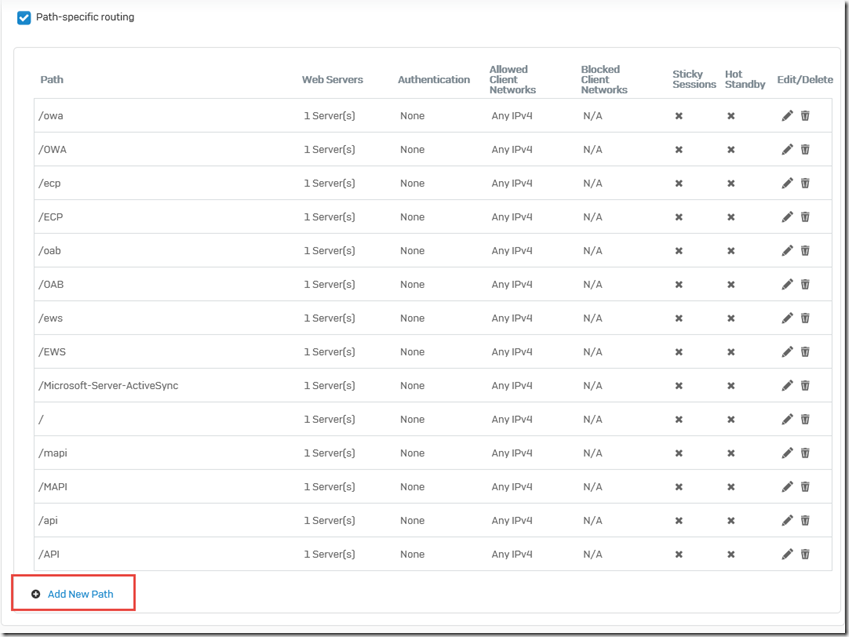
Two additional paths are added in the "Path-specific routing" section:
The following paths must be added to the rule:
- /RPC
- /rpc
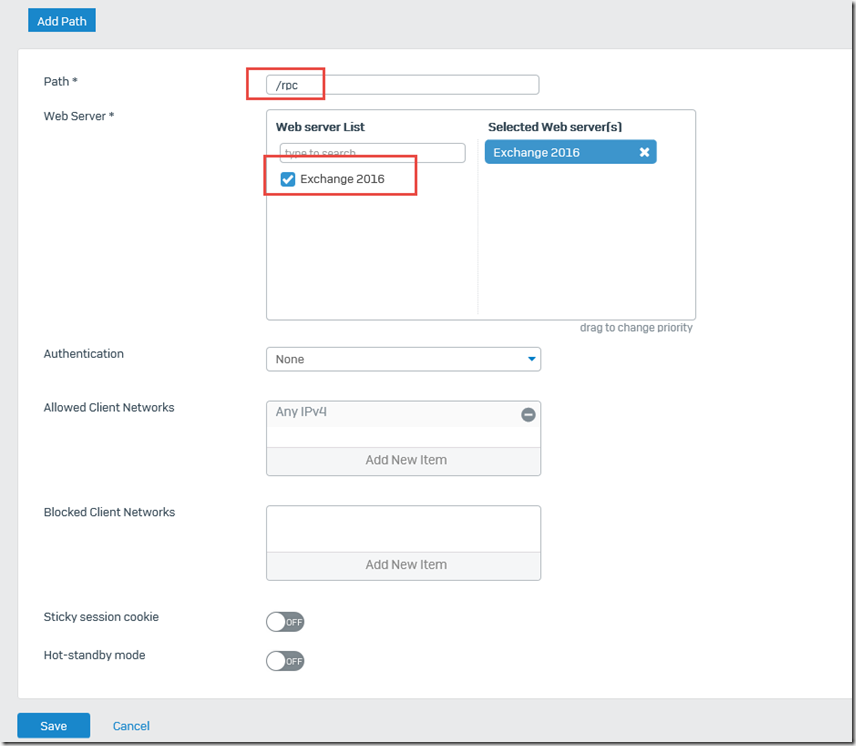
As before, the Exchange 2016 host serves as the web server:
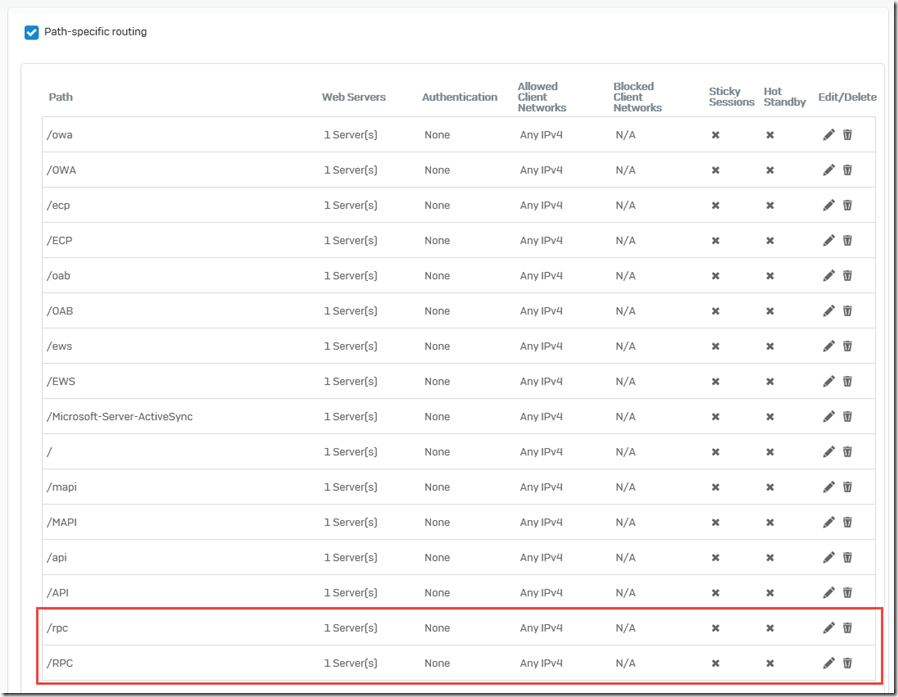
After the rule has been edited, the "Path-specific routing" section now looks as follows:
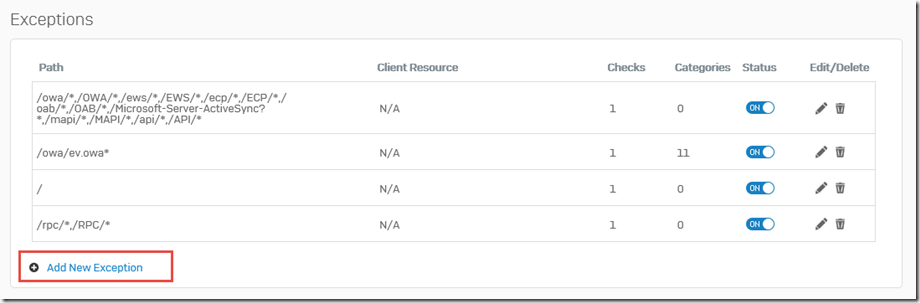
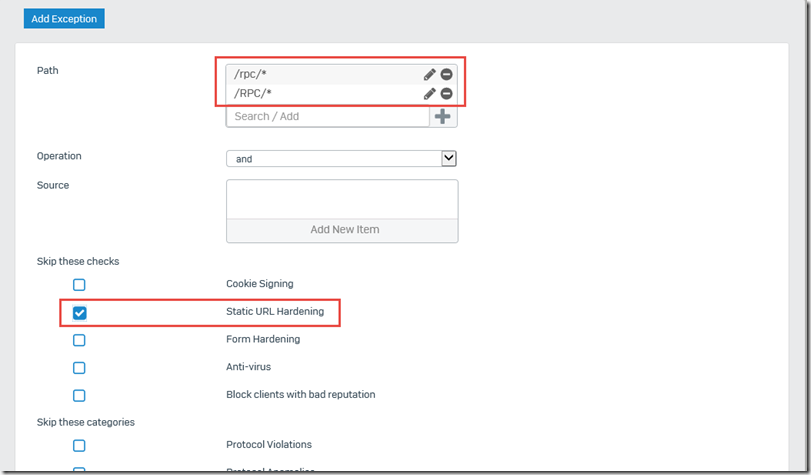
Furthermore, the two paths must also be added in the "Exceptions" section:
The following exceptions must be excluded from "Static URL Hardening":
- /rpc/*
- /RPC/*
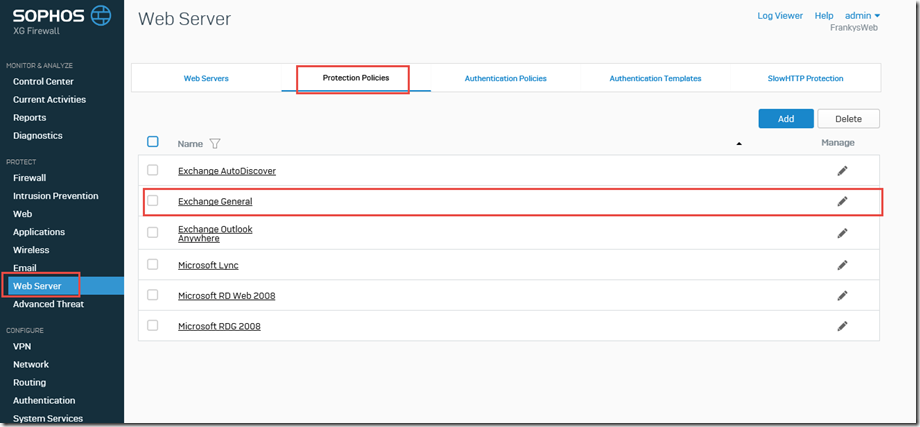
Up to this point, it's not so bad, but for Outlook Anywhere to work, the "Protection Policy" must also be adjusted:
To avoid having to change the "Exchange 2016 General" policy, a new policy can also be created; this must first have the same settings as "Exchange 2016 General" and is then adjusted as follows:
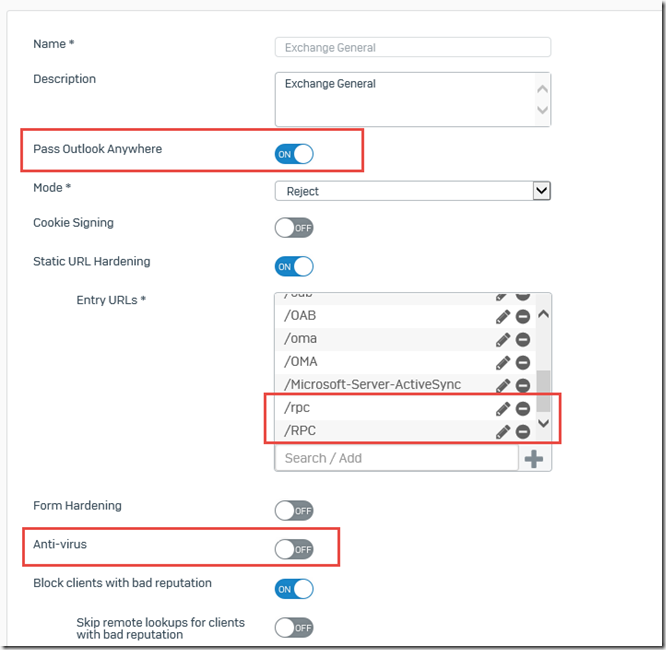
"Pass Outlook Anywhere" is activated and the entry URLs /rpc and /RPC are added, AntiVirus is deactivated:
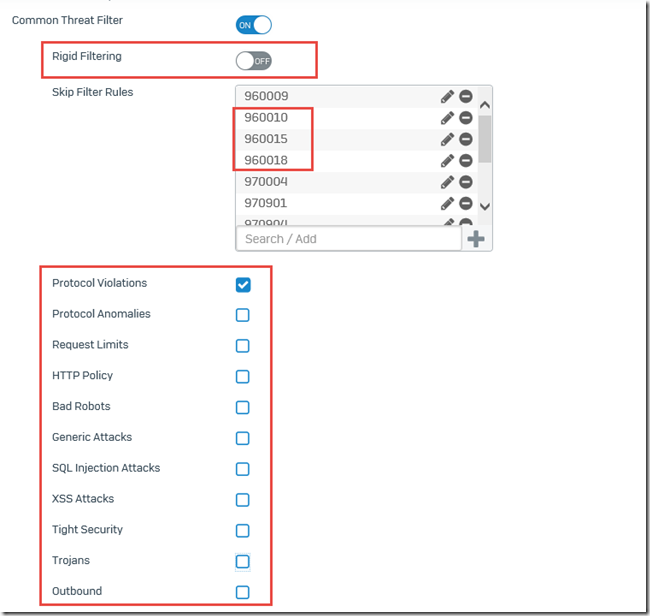
"Ridgid Filtering" must then be deactivated and the following rules must be excluded:
- 960010
- 960015
- 960018
- 981203
- 981204
All checks up to "Protocol Violations" must be switched off, which virtually deactivates the WAF:
Outlook Anywhere now works, but the WAF is almost ineffective in my opinion due to this type of configuration.
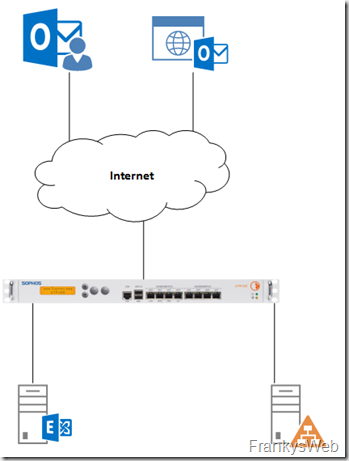
I would therefore prefer to buy a certificate with three DNS names, and I will supply the corresponding configuration of the Sophos XG later.

Hallo,
danke für den Artikel.
Was ich jedoch nicht verstehe ist, es gibt doch bereits eine Protection Policy die Exchange Outlook Anywhere heisst?
Sollte die nicht den gleichen Zweck erfüllen?
Sollte ich doch eine Kopie der“ General “ erstellen müssen, muss ich dann alle andren URLs (owa, ocp.. etc) ebenfalls in die Kopie übernehmen oder reicht es nur RCP und rcp aufzunehmen.
VG
VD
Hi Frank ,
vielen Dank für das tolle Blog.
ich bin neu zu Sophos XG and habe das V18 Installiert auf ESXI Host, leider mit v18 gibt es keine Business Anwendung rule .
ich weiße nicht wohin soll ich anfangen !
kannst du mir vielleicht ein tip geben .
vielen Dank
Mit freundlichen Grüßen
Hallo Frank, die Anleitung hat bei meiner XG super funktioniert. Nur an die neue GUI kann und will ich mich nicht gewöhnen…. Habe gestern Abend beim Versuch per Internet-Stream ein Video am TV zu sehen den Aberglauben bekommen. „Ihre Internetanbindung ist zu langam….“ 100MBit down- und 5MBit upload sollten wohl reichen. Alle beschränkungen waren extra für den Test aufgehoben! CPU und A-Speicher der VM sind auch voll ausgeschöpft für die XG 16.5.7 MR-7 (laut Vorgabe Sophos).
System runtergefahren – alte UTM9 wieder hochgefahren – alles gut. Auch VPN geht wieder so wie es soll :-). Vielleicht bin ich auch zu blööööd das XG zu konfigurieren… aber mit UTM9 habe ich ja auch hinbekommen…
Gruß H.
Hallo,
Es ist ja bekannt, dass bei der UTM Version kein LB (für EX DAG) geht, wenn man WAF verwendet.
Weisst du ob es bei der XG geht?
Gruss Andi