Forefront TMG has now been discontinued and a replacement will have to be found sooner or later. There are now several manufacturers who are filling the gap left by Forefront TMG. I will test some promising solutions and publish a howto for each of them. Finally, there will be an article comparing the solutions and listing the pros and cons from my point of view. So much for the plan.
I have therefore created a standard test environment that I will use for all solutions. The test environment has a relatively simple structure:
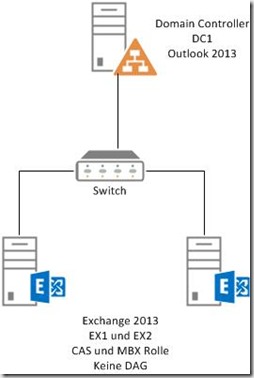
There is a Windows Server 2012 R2 with the name DC1 on which the Domain Controller role and Outlook 2013 are installed. Exchange 2013 is also installed on Server 2012 R2. The Exchange servers have the names EX1 and EX2. This is always the starting point for all solutions.
I defined a few evaluation criteria in advance in order to be able to draw a conclusion later. Mind you, these are my own criteria, which probably say little about the quality of the individual products. But more on that later.
This article is about the "Edge Security Pack" from Kemp which has been part of the load balancers for some time. Here is an overview:
http://kemptechnologies.com/tmg-edge-security-authentication
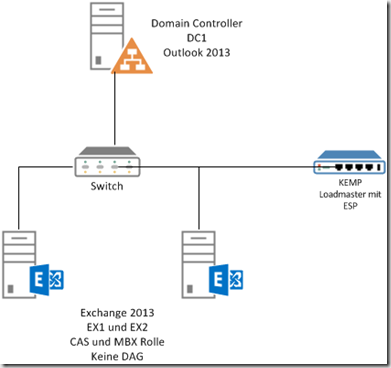
So I have the Test version and integrated the appliance into my test environment as follows. Very simple: single arm, same subnet, as simple as possible (yes, Edge Security and same subnet, or rather this test environment contradicts itself, I know... But I didn't feel like rebuilding the environment) ![]()
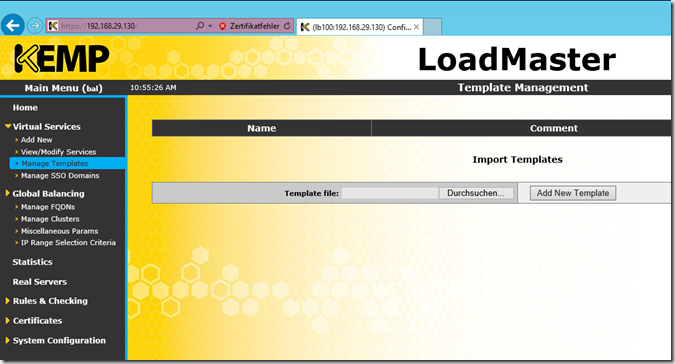
Commissioning the appliance is self-explanatory, as soon as the IP, DNS and gateway are assigned, the appliance can be configured via the browser. There are already templates that take most of the configuration work off your hands. The templates can be downloaded here:
http://kemptechnologies.com/loadmaster-documentation#c7842
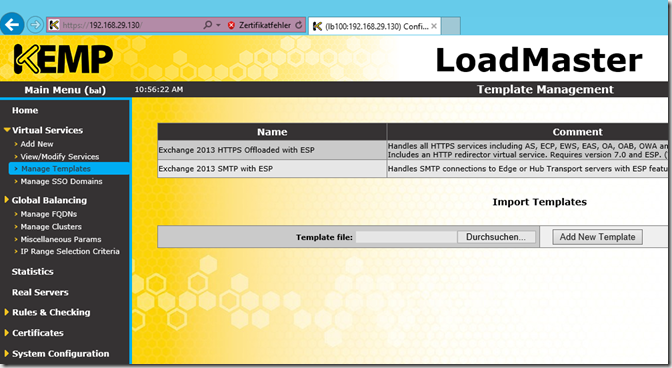
I used this template: "Exchange 2013 ESP services: SMTP with ESP and Unified HTTP/HTTPS with ESP"
The file can be uploaded under "Virtual Services" -> "Manage Templates"
If the import was successful, 2 entries should be visible
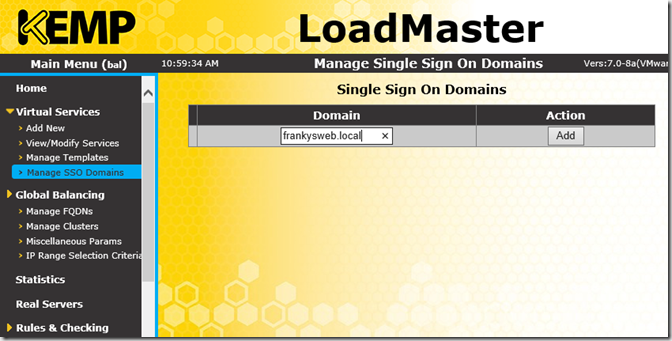
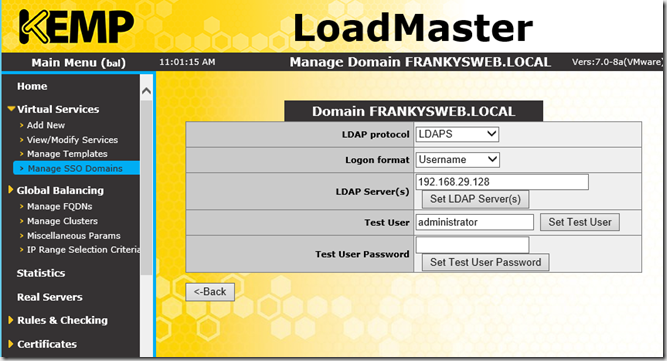
Next, I enter my Active Directory under "Manage SSO domains":
A domain controller is to be entered here as the LDAP server. "Test user" does not mean testing the connection, but a user who can read the Active Directory. For the sake of simplicity, I use the administrator
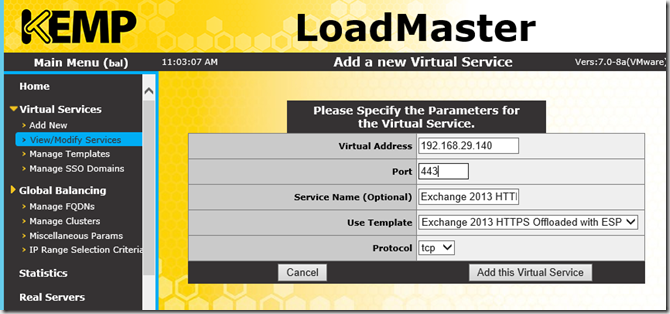
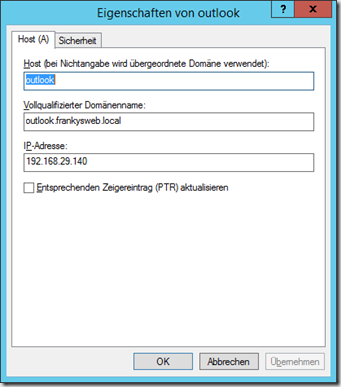
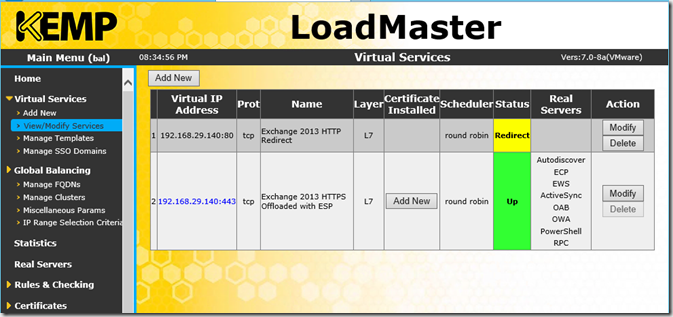
The Virtual Service can now be created. Click on "Add New" under "Virtual Services". Then enter a free IP address and select the appropriate template. I have chosen the IP 192.168.29.140. I have created a new Host-A entry in the DNS server to match the IP
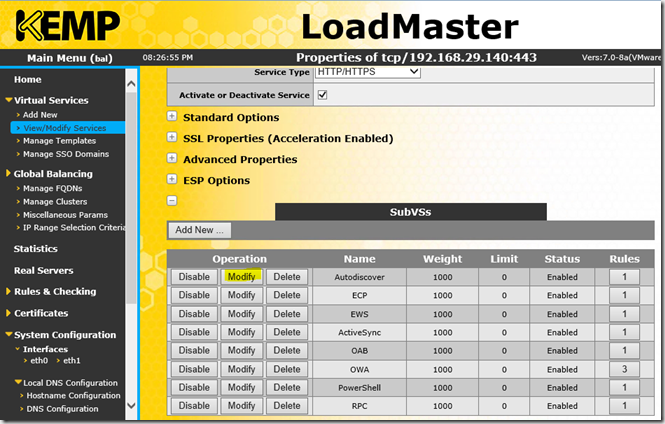
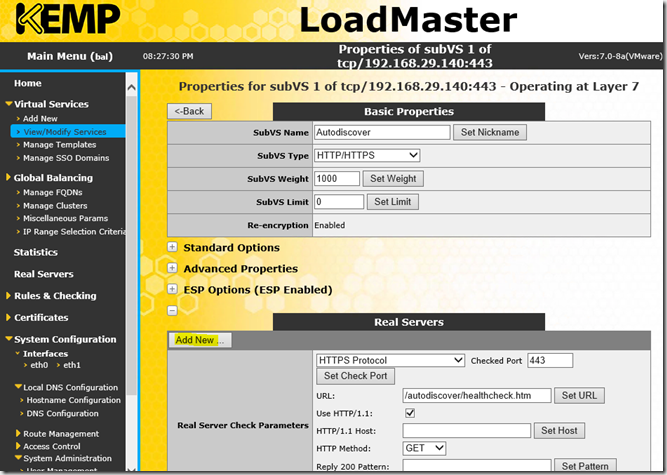
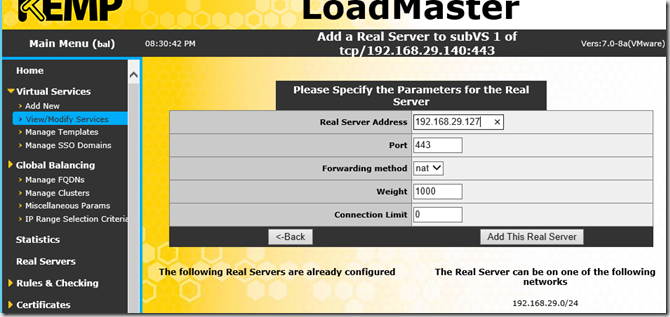
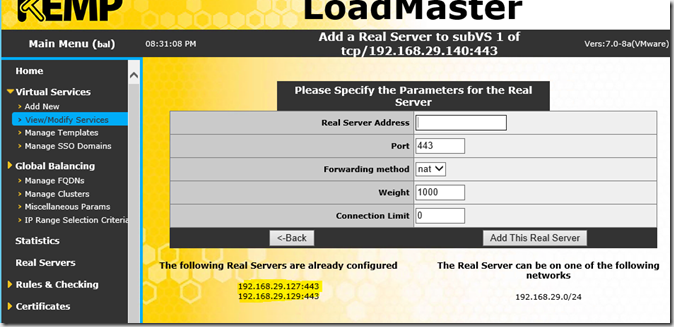
Now the real servers can be assigned, this is done separately for each service. These steps must therefore be carried out for all services (ECP, EWS, OAB etc)
After the real servers, i.e. the Exchange servers, have been entered for all services, it should now look like this:
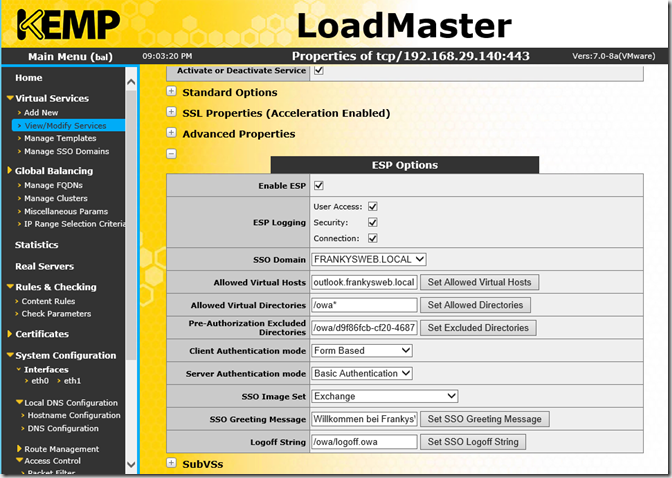
The ESP must now be switched on and configured
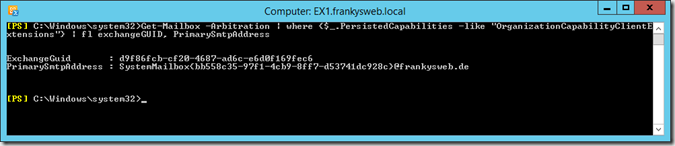
Simply adjust or adopt the values as shown in the image above. Only the path to "Pre-Authorization Excluded Directories" is a bit tricky. To determine the path, you can enter the following command on the EMD:
Get-Mailbox -Arbitration | where {$_.PersistedCapabilities -like "OrganizationCapabilityClientExtensions"} | fl exchangeGUID, PrimarySmtpAddress
The command returns your e-mail address and GUID:
From the GUID and the domain part of the e-mail address you can now compose the path, in my case like this:
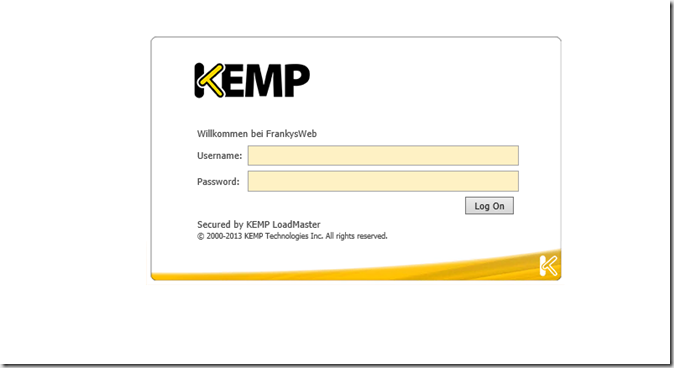
After everything has been configured, the OWA login page looks like this:
Apparently this cannot be adjusted either, Exchange 2010 Login and Exchange 2013 OWA, of course the colors do not match at all. Apparently this cannot be changed at the moment. What a pity! I'll now play around with it a bit and maintain my results table, then I'll move on to the next product.
Hallo Frank!
Vielen Dank für den genialen Artikel! Unsere Erfahrungen werden hier widergespiegelt und, ganz ehrlich, das Interface im KEMP-Look wird wohl keiner einsetzen wollen. ;-)
Aktuell gibt’s das Exchange-Design und ein Blank-Design. KEMP meint, dass es noch andere Styles geben wird. Wir hoffen auf eine Whitelabel-Variante, die sich ans Corporate Design anpassen lässt.
Ansätze zum TMG-Austausch gibt’s ja wirklich einige. Ich bin gespannt auf weitere Tests und Vergleiche. Im Vergleich zur einfachen Konfiguration von KEMP und Sophos wirken ARR und Webanwendungsproxyrolle jedenfalls reichlich kompliziert.
Beste Grüße,
Hendrik
So sieht es wohl aus. In der UTM 9.2 scheint einiges zu passieren. Da bin ich mal gespannt. Selbst die HAProxy Variante ist meines Erachtens einfacher als Webanwendungsproxy oder AAR. Wobei beides nicht das Gelbe vom Ei ist.
Hi Frank,
toll das Du Dich darum bemühst. Auf einen TMG Ersatz warten einige.
Dienste wie EAS, OWA, OA, VPN Einwahl und IPSec site2site VPN muss man ja wieder mit der neuen Firewall sinnvoll und sicher in den Betrieb bringen.
Hast Du Sophos und Barracuda auf deiner Testliste?
Der Netscaler von Citrix soll ja alle Dienste beherrschen. Der Preis denke ich, könnte hier ein Problem sein.
Bin gespannt….;-)
Gruß
Frank
Hi,
ja im nächsten Artikel wird es um Sophos UTM gehen und an Barracuda hab ich auch gedacht. Mal sehn ob man da eine Testversion bekommt. Natürlich kommen auch noch die Windows Bordmittel und dann mal sehen was sich ergibt :-)
Gruß, Frank