E-mails are known to be the main gateway for malware, viruses and all sorts of other nasty things. Unfortunately, the Exchange Server does not come with a proper spam filter, so other products must be used for effective defense against spam and malware.
Unfortunately, even the best spam filter lets a malicious email through from time to time and, of course, computers can become infected in this way.
The Emotet malware is particularly dangerous again at the moment. Emotet is not actually a classic malware that can be easily detected with a virus scanner, but rather a kind of "framework" to infect computers and entire networks. Framework is perhaps not quite the right word here, but in essence it describes the way it works quite well: In the first phase of an Emotet wave, masses of emails are sent out. The emails are often fairly well-crafted malware emails, which are initially intended to infect one or more computers in the network. In phase 2, starting from the first computer, as many other computers in the network as possible are infected. The way in which the other computers are infected is variable; for example, vulnerabilities such as BlueKeep are used, and it is also possible to steal Kerberos tickets. In the third phase, the actual malware is downloaded. The malware is then usually executed almost simultaneously on all infected computers. In the third phase, for example, ransomware can encrypt the data. However, as Emotet is very modular, the attacker is virtually free to decide what type of malware is used on the infected computers, which is precisely what makes Emotet so dangerous.
I therefore simply started a little self-test to check how my spam filter behaves with slightly "better spam mails". To be more precise, I tested it with three different spam filters.
I have tried various scenarios. I was able to get the following mail through all the filters I tested:
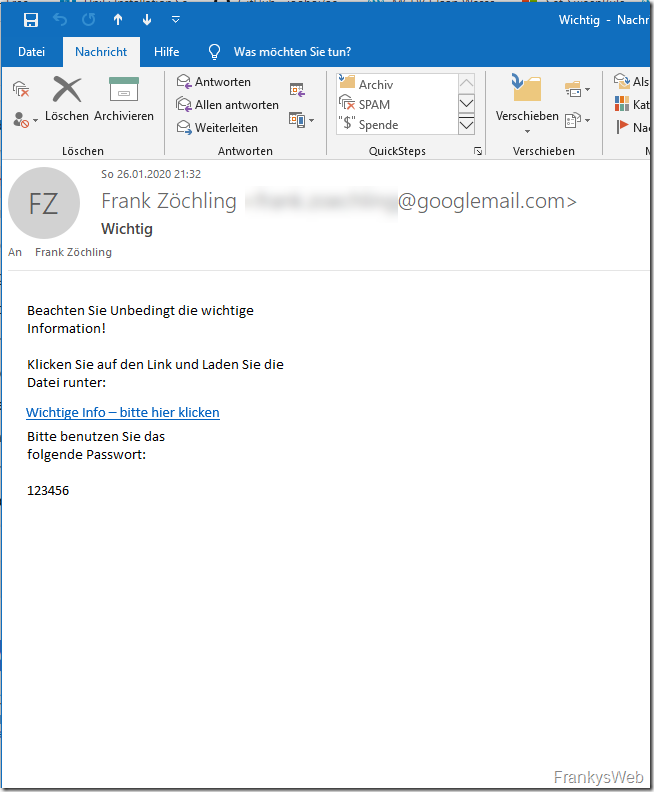
I simply created a GMail account for this mail and sent it to myself. This mail is difficult for many spam filters to recognize for the following reasons:
- The visible text consists of images embedded in the e-mail. The images are harmless.
- The broken link (important info - please click here) was shortened by a URL shortener
- There is completely harmless text in the mail, which is not visible due to the white font color
The mail therefore actually looks like this:
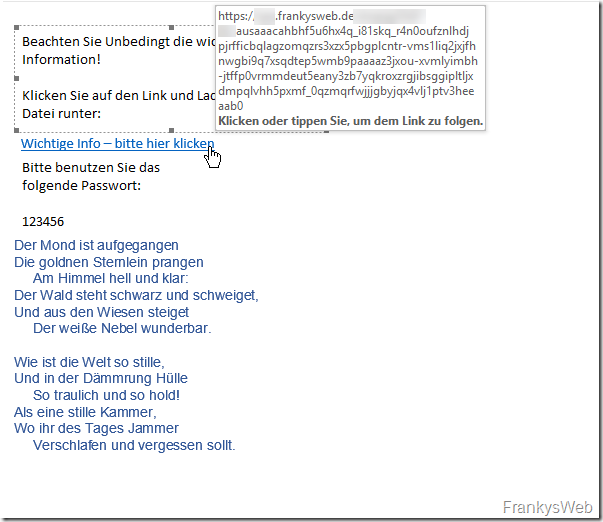
The two visible texts are images that were embedded in the mail, the malicious link was shortened by a URL shortener to disguise the malicious URL. Harmless text follows with white text on a white background (shown here in blue). Incidentally, the original URL is the EICAR Test Virus (https://www.wicar.org/test-malware.html), any virus scanner should be able to recognize this...
In my case, there is now even a special feature: The link shortened via URL Shortener (cutt.ly) was rewritten by my spam filter; this function is called differently depending on the manufacturer and product. In this case, the rewriting of the link, which was supposed to be an additional security feature, had the exact opposite effect: My domain is recognizable, what's the harm in that, the filter will sort it out...
If I click on the link, I land on the EICAR test page, but Chrome then blocks the call, but only Chrome:
If I had sent a link to download a password-protected Word document with a malware macro, the download would have worked and the simple password is already in the email. By the way: Chrome blocks the malware URL, if Internet Explorer is set as the default browser, the download works without any problems.
In this case, of course, it is just a simple personal test. Emotet works in a very similar way, and in some places even more cleverly. In the Emotet malware mails, for example, reference is made to previous conversations. There is a very interesting article about this here:
Just like my test mail above, this type of mail often ends up in recipients' inboxes. Even the best spam filters (regardless of the manufacturer) do not offer one hundred percent protection here (I have tested it with 3 well-known e-mail security products, for example, and all three have failed, I won't mention any names).
Even the user can hardly be blamed if a malicious link is clicked on or a malicious document is opened. Emotet emails in particular can currently only be recognized by the original sender address, but who always pays attention to that?
As you can see in my example, rewriting links in emails, which is often touted as a security feature, is not necessarily a security gain. In a well-crafted phishing email, this could even give the recipient the impression of additional authenticity. Such a feature should therefore also be treated with caution.
Another popular method is to send mails with initially harmless links. The trick is that a malicious download is only activated a few minutes later after the link has been sent. This allows the initially harmless link to pass through the filters. Once the mail is in the recipient's mailbox, the malware behind the link is activated.
As you can see from your small example, it is usually quite easy to smuggle a malware mail past spam filters. Even anti-spam products with a sandbox feature can be fooled quite easily with the delayed links.
The next article deals with measures to prevent an Emotet infection.