During a server migration, the problem occurred that a certificate could not be exported. During the migration, only the operating system was to be replaced with a current version and the certificate was to continue to be used if possible. In this specific case, it was a wildcard certificate, but the setting "Mark this key as exportable" was not set during import.
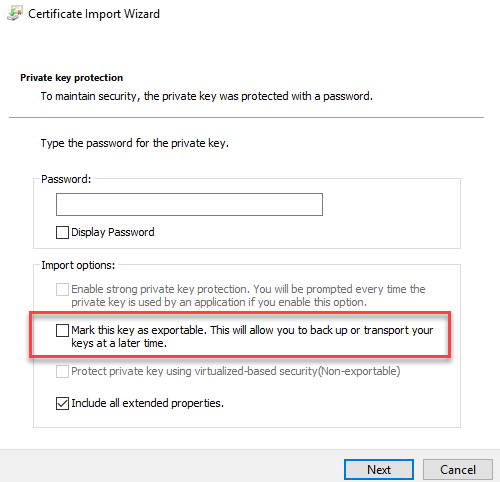
The certificate with the private key can therefore not simply be exported via MMC and imported on the new server. In order to be able to use the certificate on the new server anyway, you have to use a little trickery. I have simulated the procedure in a test environment.
In my test environment, I have a certificate that was not imported with the "Mark this key as exportable" flag. In this case, it is the certificate with the common name "DC1.ad.frankysweblab.de" (as an example).
Source server (export certificate and key)
In order for the certificate including the private key to be transferred to another server, some information must be collected. First of all, the thumbprint of the certificate that is to be transferred from the source server to the target server is required. The following command can be used to display the thumbprint and CNs on the source server:
Get-ChildItem -Path Cert:\LocalMachine\my
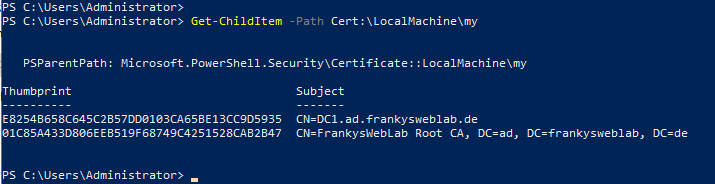
As already mentioned, the private key of the certificate with the CN "DC1.ad.frankysweblab.de" cannot be exported.
In order to transfer the certificate to the target server, the name of the private key in the file system is required. The name can be found using the thumbprint of the certificate:
(Get-Item Cert:\LocalMachine\My\E8254B658C645C2B57DD0103CA65BE13CC9D5935).PrivateKey.CspKeyContainerInfo.UniqueKeyContainerName
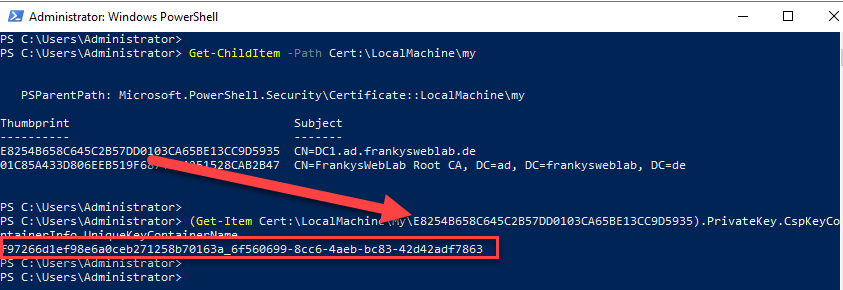
This is now the file name of the private key which is saved under the path "C:\Users\All Users\Microsoft\Crypto\RSA\MachineKeys". To make it a little easier, the private key is copied to C:\:
Copy-Item "C:\Users\All Users\Microsoft\Crypto\RSA\MachineKeys\f97266d1ef98e6a0ceb271258b70163a_6f560699-8cc6-4aeb-bc83-42d42adf7863" c:\
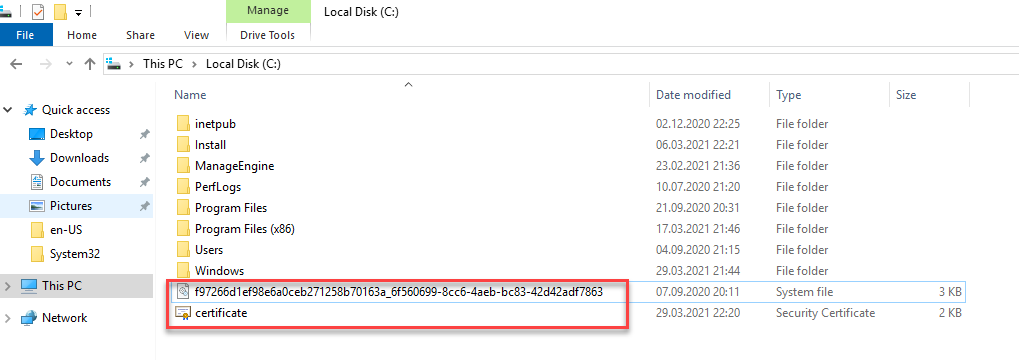
Now the certificate must be exported without the private key, this can be done via MMC. The .CER file can also be saved under C:\:
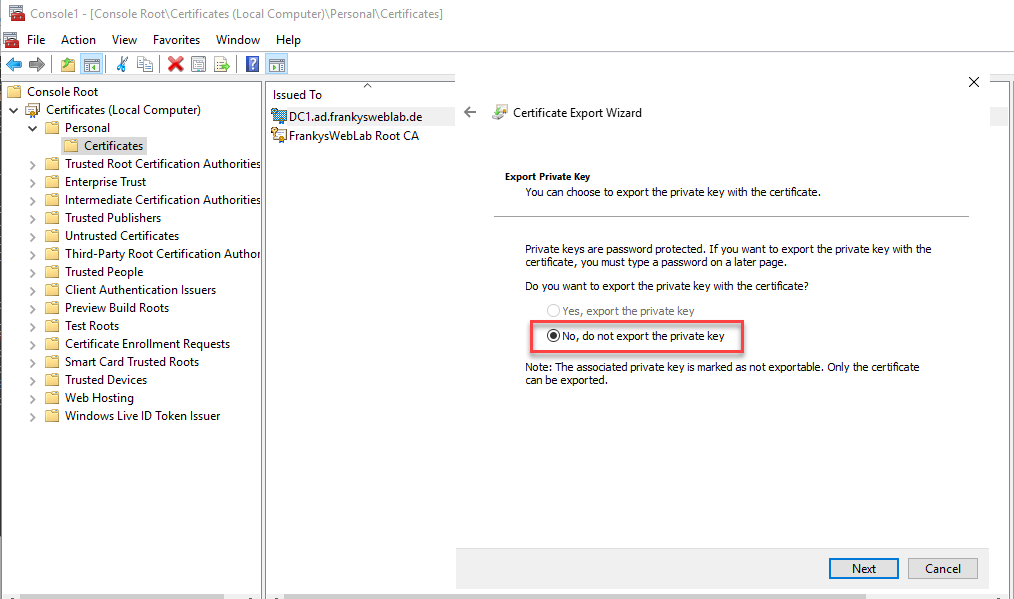
There should now be 2 files under c:\, one with the exported private key and one containing the certificate:
Target server (import)
Both files must now be copied to the target server. The certificate (without the private key) can be imported directly into the computer's certificate store:
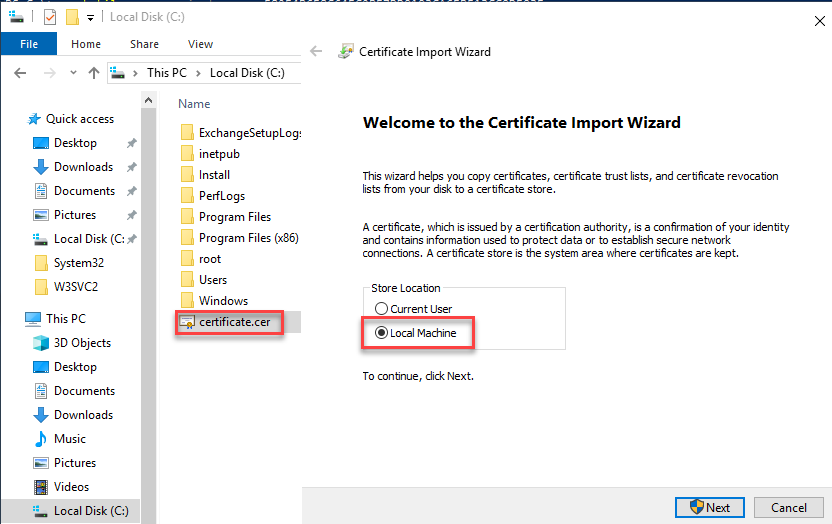
The certificate must be imported to the same storage location (Personal Certificates) so that the certificate and private key can be reunited on the target server. The certificate has now been imported, but the private key is still missing:
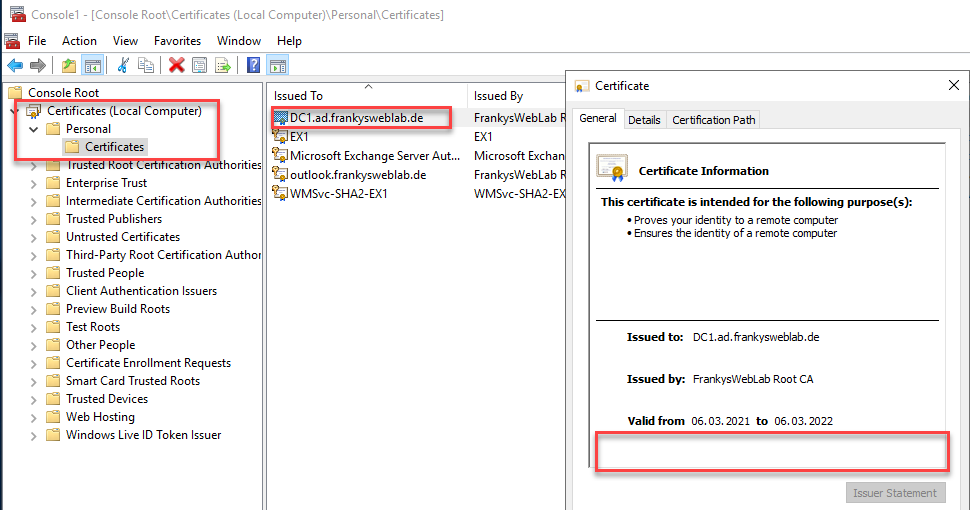
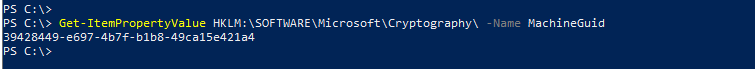
In order for the private key to be imported on the target server, the file with the cryptic name must be renamed. The second part of the file name is the GUID of the source server (the character string after the underscore "_"), this GUID must now be replaced with the GUID of the target server. The GUID of the target server is now required for this, this can be queried on the target server with the following command:
Get-ItemPropertyValue HKLM:\SOFTWARE\Microsoft\Cryptography\ -Name MachineGuid
To make it a little clearer, I have left the original file and the renamed file in the folder, as you can see, the character string after the underscore has been replaced with the GUID of the target server:
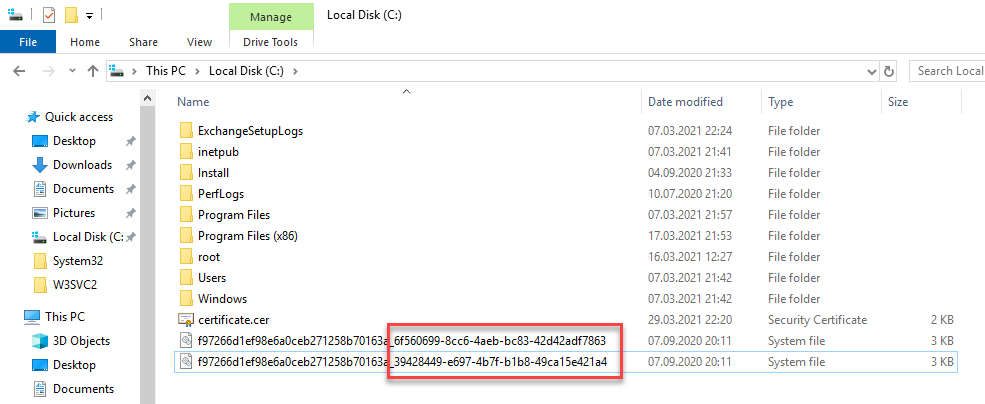
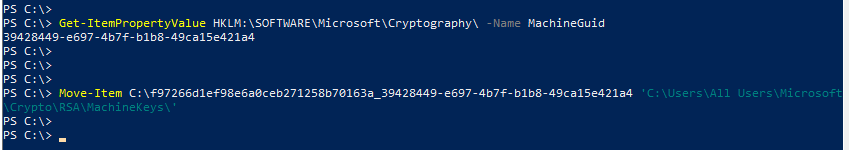
The renamed file must now be copied back to "C:\Users\All Users\Microsoft\Crypto\RSA\MachineKeys" on the target server, a PowerShell with admin rights is sufficient here:
Move-Item C:\f97266d1ef98e6a0ceb271258b70163a_39428449-e697-4b7f-b1b8-49ca15e421a4 'C:\Users\All Users\Microsoft\Crypto\RSA\MachineKeys\'
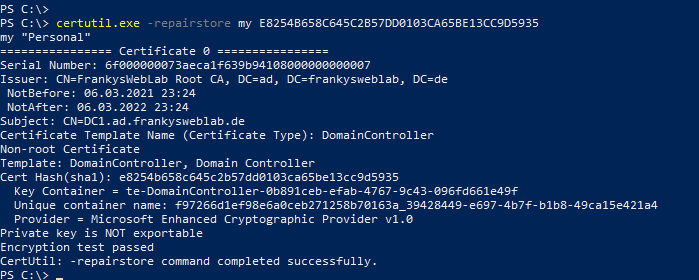
The thumbprint of the certificate is now required again. The certificate and private key can be reassembled on the target server using the thumbprint of the certificate:
certutil.exe -repairstore my E8254B658C645C2B57DD0103CA65BE13CC9D5935
Done. The MMC now also shows that the private key for the certificate is available:
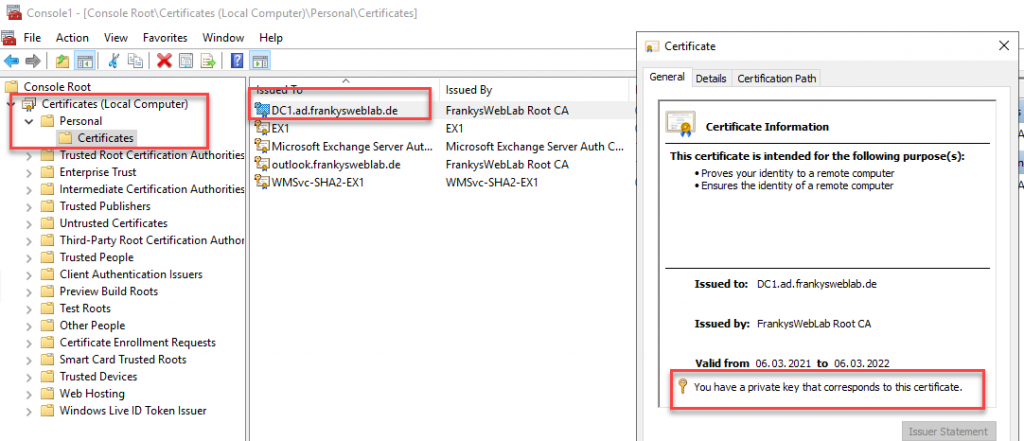
Incidentally, the private key is protected against export on the target server.
Unterscheidet sich das beschriebe Vorgehen wenn es sich um ein Zertifikat/Key handelt, welche als CurrentUser gespeichert sind?
Hallo Frank,
leider benötige ich diese Prozedur.
Beim letzten Step erscheint bei mir jedoch eine SmartCard Abfrage.
Bis dahin hat alles super funktioniert.
Kannst du mir sagen was ich falsch mache?
Viele Grüße Dirk
Hi,
hier das gleiche Problem. Auch hier erscheint beim letzten Schritt die Abfrage einer SmartCard :-(
Gruß
Michael
Hallo,
Gibt es schon eine Lösung?
Grüße
Ich habe auch das Problem mit der Smartcard und bis das nicht behoben ist läuft mein Exchange nimmer. Hat jemand ne Idee oder kann helfen?
Hey – ich glaube ich habe das Problem ohne die Zertifikate hinbekommen, so dass ich das alte nicht mehr benötige.
Am neuen Server alle Adressen auf den neuen angepasst. Neues Zertifikat von der Zertifikatstelle erstellt und am neuen importiert.
Alten Server mal testweise vom Netz getrennt. Anscheinend funktioniert soweit alles.
Lass das mal so bevor der alte deinstalliert wird.
Hallo, und Danke für den informativen Artikel!
Eine Frage zum generellen Verständnis hätte ich noch:
Gibt es eigentlich noch irgendeinen Weg (abgesehen vom vorherigen Beitrag), ein Zertifikat samt privatem Schlüssel zu exportieren? Ich habe das Problem mit einem Exchange 2016, der läuft bei uns in einer Domäne mit eigener PKI. Zum einen hätte ich gerne aus Sicherheitsgründen das Exchange-Zert samt Schlüssel nochmals weggesichert. Zum anderen – was macht man mit Usern, die gerne auf ihrem Apple, Android usw. ihr Mail-Konto haben wollen? Mir fehlt da gerade der Ansatz…
mfG
Karsten
der Private Schlüssel darf unter keinen Umständen herausgegeben werden!
Wenn der Exchange mit einem nicht öffentlichen Zertifikat betrieben wird, dann müssen die User auf ihren Mobilgeräten auch das Root und alle Ziwschenzertifikate einspielen.
Dann sollten sie dem Zertifikat des Exchange auch vertrauen.
Wobei es heute eigentlich keinen Grund mehr gibt, gerade der Exchange öffentlich erreichbar ist, auf ein selbst signiertes Zertifikat zurückzugreifen, da Lets’Encrypt kostenlose Zertifikate ausstellt und Frank auch diverse Anleitungen dazu veröffentlich hat.
…oder man macht einfach einen Certificate-Jailbreak und exportiert ganz normal über die MMC:
https://github.com/iSECPartners/jailbreak
…na das is‘ ja mal… ’n Ding. Bin sprachlos. Ist das ein Bug oder by Design?
Bug By Design, aber der Windows Defender haut es direkt weg.
Konnte das Zertifikat in meinem Fall dadurch nur direkt per CMD exportieren. Die „SYSTEM“ Zertifikate hat er mir nicht in der mmc geöffnet.
Lustig fand ich die Warnung vom Windows Defender (Schriftzeichen nicht geändert!):
„Τђїŝ άρρŀįςąŧĭōň ώаś гèmθνεđ ъ℮сàύŝę ιŧ ϊş ьłõĉκëδ āςςōгđілğ ťσ тђĕ Μіςгоŝόƒť Đéƒėņð℮ř ƒõř Ëńđρòìпτ φõĺĭςý.“