I am not entirely sure whether the following problem also occurs in environments in which standard Windows DNS servers are used. Companies that do not run their DNS infrastructure on Microsoft DNS servers might be interested in the following article.
The following behavior of Windows 10 computers could be reproduced on a "non Windows DNS" server:
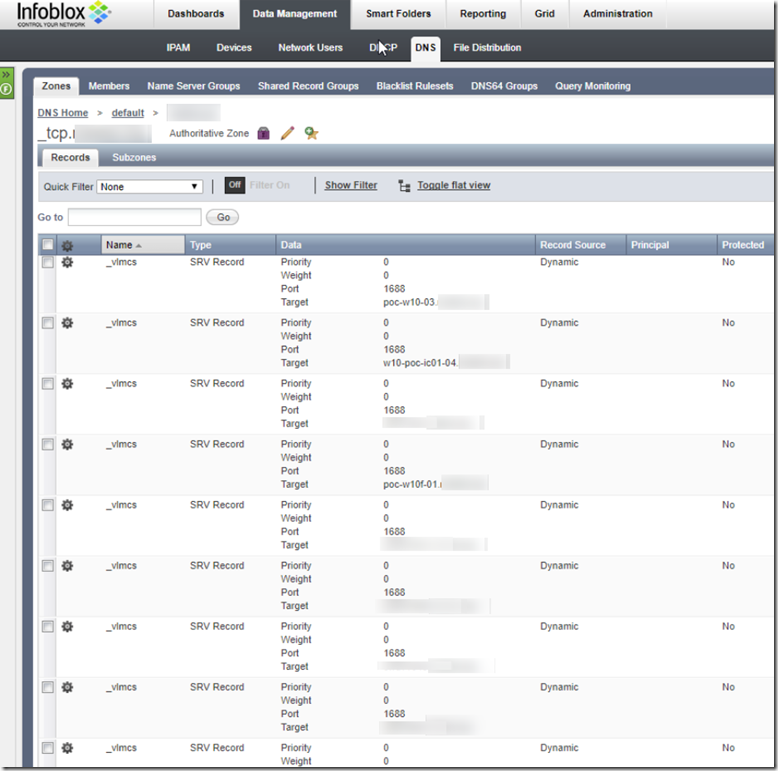
Some Windows 10 clients create an SRV entry in the _tcp DNS zone of their Active Directory domain. The SRV entry is _vlmcs._tcp.addomain.tld and points to the client hostname with port 1688. Here is a screenshot of the _tcp zone with the corresponding entries:
In this case, the update of the DNS entries in the DNS zone belonging to the Active Directory is permitted via GSS-TSIG, so in this case a Windows 10 client may also make corresponding entries in the DNS zone. This also includes the _VLMCS SRV records.
Normally Microsoft KMS servers are made known with a _vlmcs SRV entry in the DNS, so the question I asked myself is: Why does a Windows 10 client create this type of DNS entry?
After some research, this behavior seems to be due to the type of product key, if Windows 10 clients are installed with a KMS product key, the clients register with a _vlmcs entry in the DNS. Windows 10 computers that are not installed with a KMS key do not create a corresponding entry in the DNS.
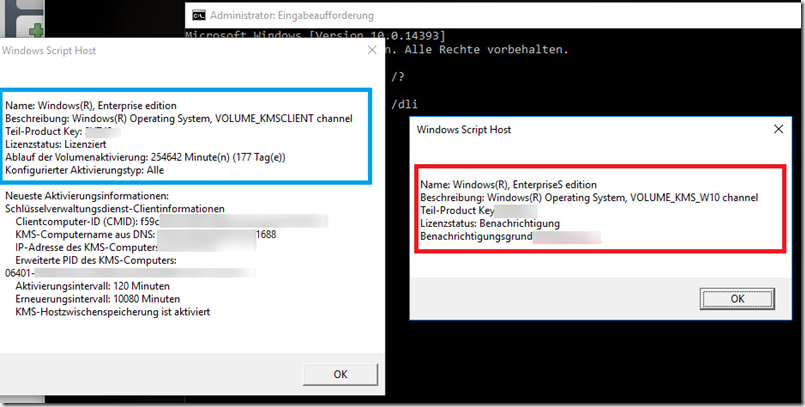
For comparison, here is a screenshot of a Windows 10 client with a KMS key (red) and a client without a KMS key (blue). The red client creates corresponding SRV entries in the DNS, the blue client does not create an SRV entry.
In this case, some Windows clients were equipped with an image that contained the wrong product key. This can be checked with the following command:
slmgr.vbs /dli
To prevent corresponding Windows 10 clients from creating SRV entries in the DNS, the following command can be used:
slmgr.vbs /cdns
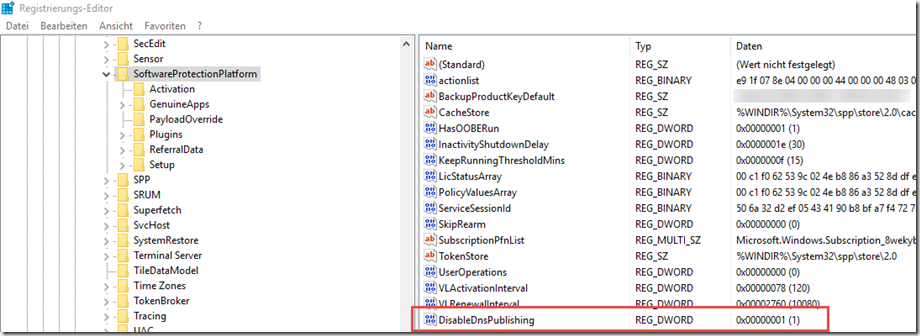
This prevents the corresponding computers from creating the _vlmcs entry in the DNS. The command above only sets a registry key, so the registry key can also be easily distributed via GPO:
- Path: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform
- Name: DisableDnsPublishing
- Type: REG_DWORD (32-bit)
- Value: 1 (decimal)
In this way, the many SRV entries can be prevented and the computers concerned can be supplied with the correct product key.

Das sollten so einige ChrMü’s dieser Welt wohl auch besser tun ;)
Der ist „ausnahmweise“ unschuldig. Hat es aber heute trotzdem ausbaden müssen :-D
Da kann ich SW nur zustimmen. Ganz normales Verhalten. Um das zu Umgehen, sollten für Deployments diese KMS Client Keys genutzt werden: https://technet.microsoft.com/en-us/library/jj612867(v=ws.11).aspx
Das war mir unbekannt, siehste mal, ich bleib lieber beim Exchange Server. :-)
Das ist seit eh und je ein Standardverhalten von Windows – liegt ausschließlich am verwendenden KMS Key und tritt genauso auch auf Windows DNS Servern auf.