Windows Server 2025 offers new features for Active Directory (AD DS) and Active Directory Lightweight Domain Services (AD LDS) for the first time in a long time. With the new features, Active Directory scales better even in very large environments and brings additional improvements for security and stability.
Optional function for 32k database page size
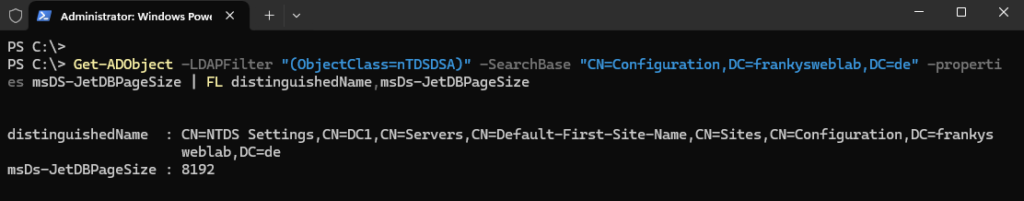
Since the introduction of Active Directory in Windows 2000, a database called Extensible Storage Engine (ESE) or JET Blue has been used, which stores data in 8k pages. This 8k structure led to certain restrictionsfor example, that a single AD object may not be larger than 8k bytes. The switch to a new 32k page format removes many of these old limitations. For example, multi-value attributes can now store up to around 3200 values. The optional feature can be activated if all domain controllers are running on Windows Server 2025. The following command can be used to determine the current database page size (SearchBase must be adjusted accordingly):
1 | |
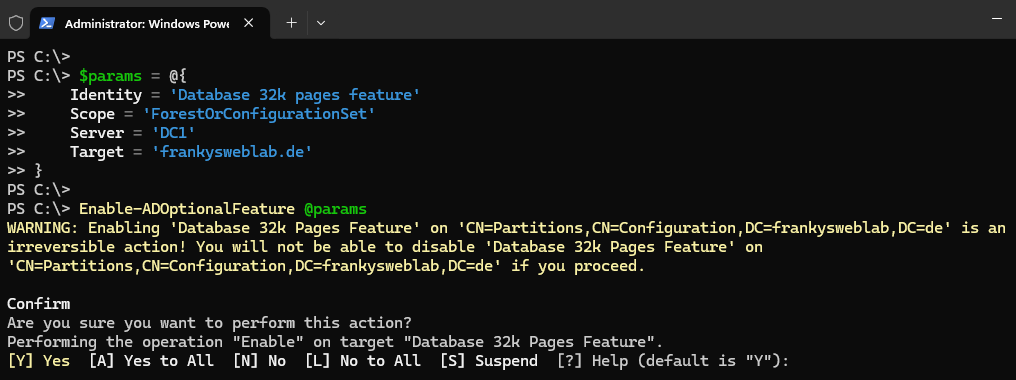
The database page size can be increased to 32k with the following command:
1 2 3 4 5 6 7 | = @{} |
New DCs with 32k-page database
New domain controllers (DCs) can now be installed with a 32k-page database that uses 64-bit IDs and runs in "8k-page mode" to remain compatible with older versions. An existing DC will retain its current 8k page database format. However, to switch to 32k database pages, all DCs in the overall structure must have a 32k-capable database.
AD schema updates
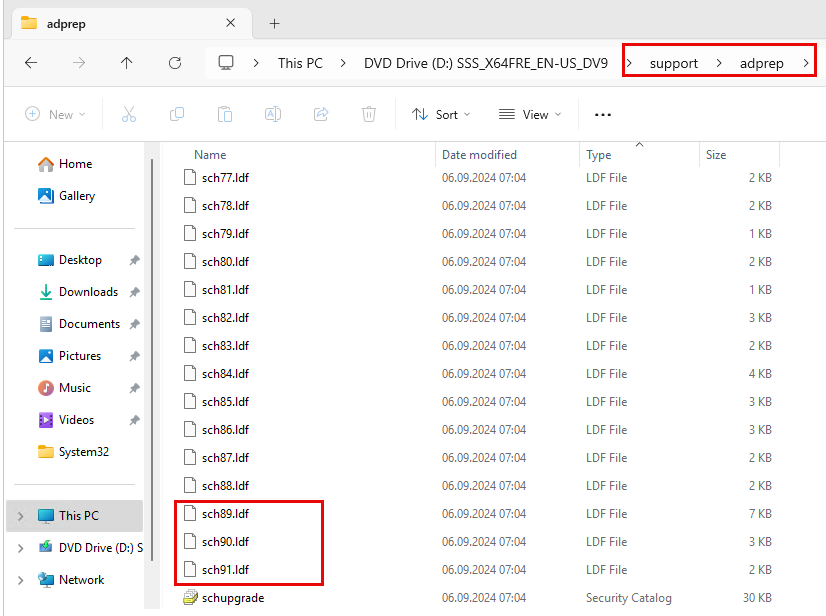
A schema update is required so that new features can be used. Three new log files (sch89.ldf, sch90.ldf and sch91.ldf) extend the AD schema. For AD LDS there are suitable updates in the file MS-ADAM-Upgrade3.ldf. The schema update files can be found in the Server 2025 ISO in the folder "support\adprep":
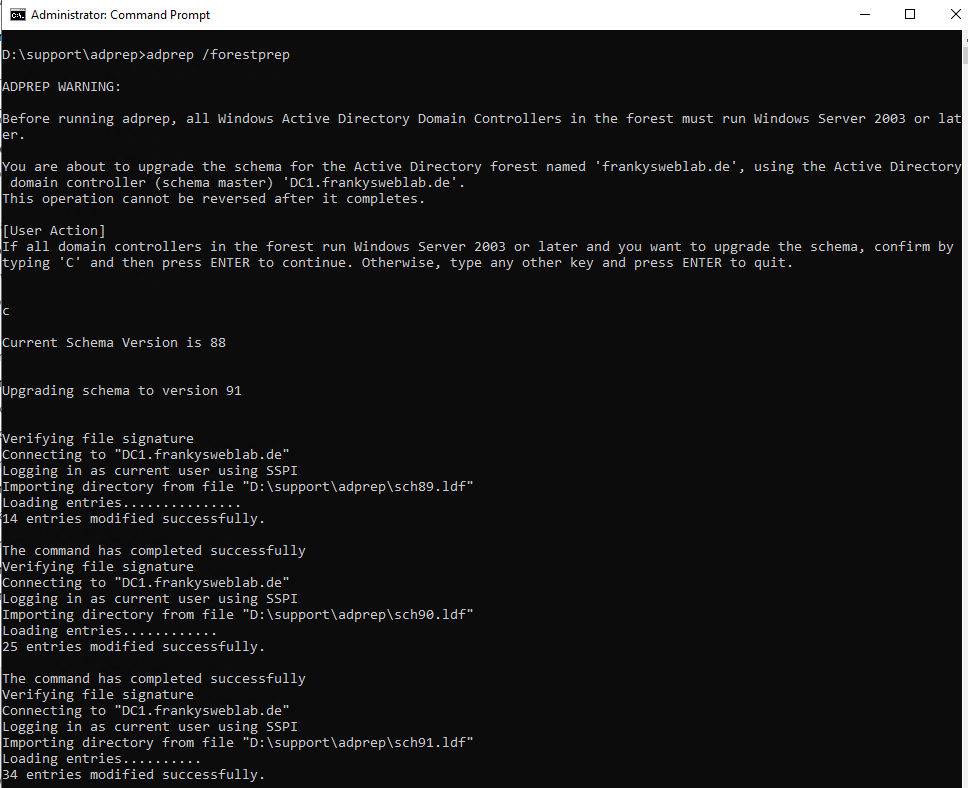
The schema update can be executed with the following commands:
1 2 | |
AD object repair
AD now allows domain admins to fix objects that are missing important attributes such as SamAccountType and ObjectCategory. These changes are made via a new function called fixupObjectState.
Channel Binding Audit support
The event log events 3074 and 3075 can now be activated for channel binding with LDAP. If the channel binding setting is made more secure, an administrator can see which devices in the network do not support channel binding or have problems with it.
Improvements to the DC location algorithm
The DC detection algorithm helps computers in the network to find the nearest domain controller (DC) that performs the authentication requests.
This algorithm has been improved in the new version: It can now distinguish better between the shorter NetBIOS domain names (e.g. "frankysweblab") and the DNS domain names (e.g. "frankysweblab.de") and assign them correctly.
Overall structure and domain function level
The new Active Directory function levels provide support for the new features and are necessary in order to be able to use the new 32k database page size. The new function levels have the version number 10 for DomainLevel and ForestLevel.
Improved algorithms for name/SID lookups
The forwarding of name and SID queries between computers no longer runs via the old Netlogon channel. Instead, the Active Directory now uses Kerberos authentication and the DC detection algorithm for this.
Improved security for confidential attributes
DCs and AD LDS instances only allow LDAP to add, search for and change confidential attributes if the connection is encrypted.
Improved security for standard computer account passwords
Active Directory now uses randomly generated default passwords for computer accounts. Windows 2025 DCs prevent computer accounts from being set up with the default password of the computer account name.
Kerberos PKINIT support for cryptographic agility
The Kerberos Public Key Cryptography for Initial Authentication in Kerberos (PKINIT) protocol implementation has been updated to enable cryptographic agility by supporting more algorithms and removing hard-coded algorithms.
LAN Manager GPO setting
The GPO setting "Network security: Do not save LAN Manager hash value on next password change" is no longer available or applicable in new versions of Windows.
LDAP encryption by default
After SASL authentication, all LDAP client communications use LDAP sealing by default.
LDAP support for TLS 1.3
LDAP uses the latest SCHANNEL version and supports TLS 1.3 for connections via TLS.
Obsolete SAM-RPC password change behavior
Secure protocols such as Kerberos are the preferred method for changing domain user passwords. The latest password change method, SamrUnicodeChangePasswordUser4 with AES, is supported by default.
NUMA support
AD DS now utilizes NUMA-capable hardware by using CPUs from all processor groups.
Performance Counter
New performance counters are available for line monitoring and troubleshooting:
- DC Locator - Specific indicators for clients and domain controllers (DC).
- LSA Lookups - Query names and SIDs via LsaLookupNames, LsaLookupSids and similar APIs. These indicators are available for both client and server versions.
Replication priority
Replication priority allows administrators to increase the system-calculated replication priority for a specific replication partner and naming context. This feature provides more flexibility when configuring the replication order for specific scenarios.
It seems that with windows 2025, it is not possible to connect Devices like NAS and Firewalls to use the Active Directory.
Do you know of a solution? would be greatly appreciated