The new Windows Server is now available and I started configuring my template for a standard installation straight away. I clone my production and test VMs from this template.
The following settings are based on the standard Windows installation with desktop. Initially, only the operating system and all available Windows updates are installed. All customizations are described in the following article.
General Windows settings for the template
In the following section you will find my general Windows settings for the template.
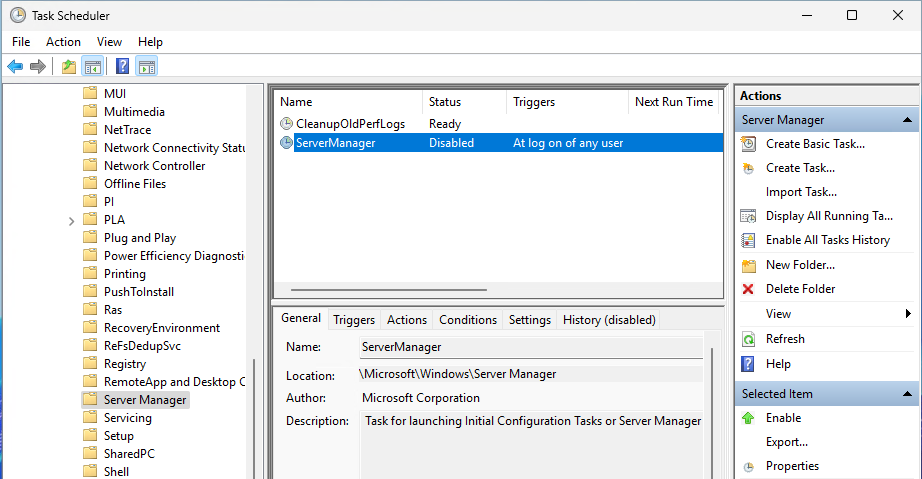
Server Manager does not start at user logon
I start the Server Manager when I need it, every time a user logs on the Server Manager is just annoying. To disable the Server Manager for all users (including new users), you can simply deactivate the task:
Deactivated services
I have deactivated the following Windows services, which are automatically loaded at startup:
- Print Spooler
- Windows Audio
- Windows Audio Endpoint Builder
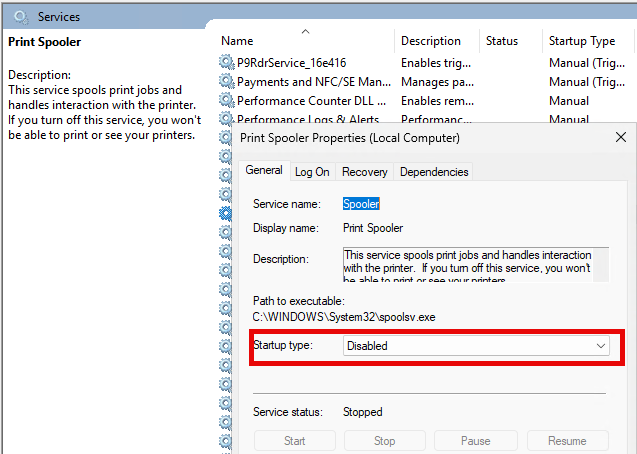
The print spooler is usually only required on print servers and audio services are not normally needed.
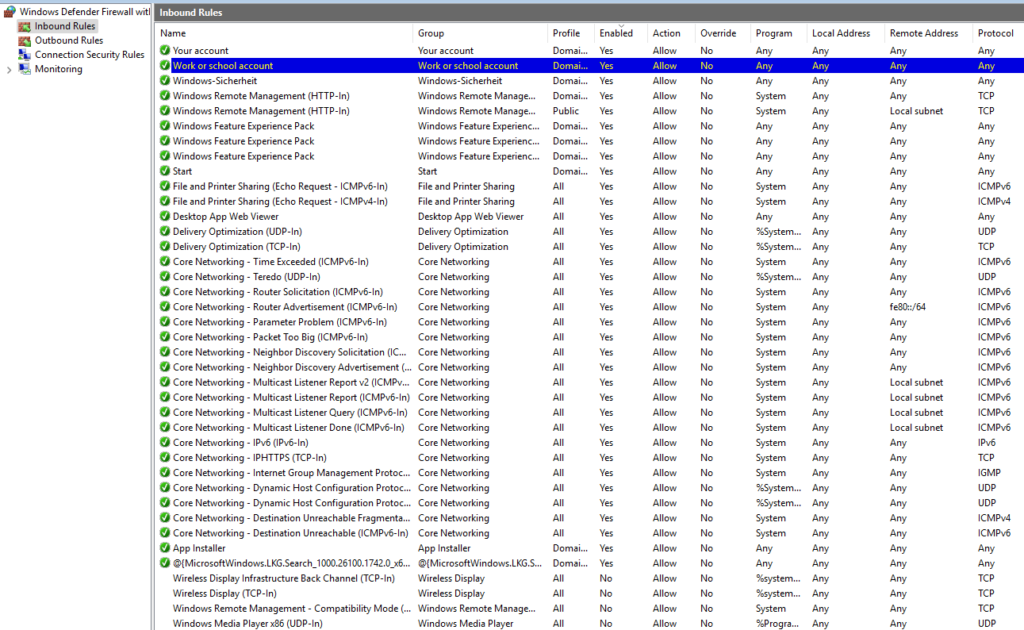
Disabled / Enabled firewall policies
After the installation of Windows Server 2025, there are a number of activated firewall rules. The mDNS rules in particular are at least problematic in terms of security. I have therefore deactivated the following firewall rules:
- AllJoyn Router (TCP-In)
- AllJoyn Router (UDP-In)
- Cast to Device functionality (qWave-TCP-In)
- Cast to Device functionality (qWave-UDP-In)
- Cast to Device SSDP Discovery (UDP-In)
- Cast to Device streaming server (HTTP streaming-in)
- Cast to Device streaming server (RTCP streaming-in)
- Cast to Device streaming server (RTSP streaming-in)
- Cast to Device UPnP Events (TCP-In)
- DIAL protocol server (HTTP-In)
- DIAL protocol server (HTTP-In)
- Feedback Hub
- mDNS (UDP-In)
- Microsoft Edge (mDNS-In)
- Microsoft Media Foundation Network Source IN [TCP 554]
- Microsoft Media Foundation Network Source IN [TCP 554]
- OpenSSH SSH Server (sshd)
- Wireless display (TCP-In)
- Wireless Display Infrastructure Back Channel (TCP-In)
- WFD ASP Coordination Protocol (UDP-In)
- WFD Driver-only (TCP-In)
- WFD Driver-only (UDP-In)
I have activated the following rules:
- File and Printer Sharing (Echo Request - ICMPv4-In)
- File and Printer Sharing (Echo Request - ICMPv6-In)
This means that significantly fewer rules are active and the rules can be easily reactivated if required:
Activate Remote Desktop (RDP)
I have activated remote desktop connections via Server Manager:
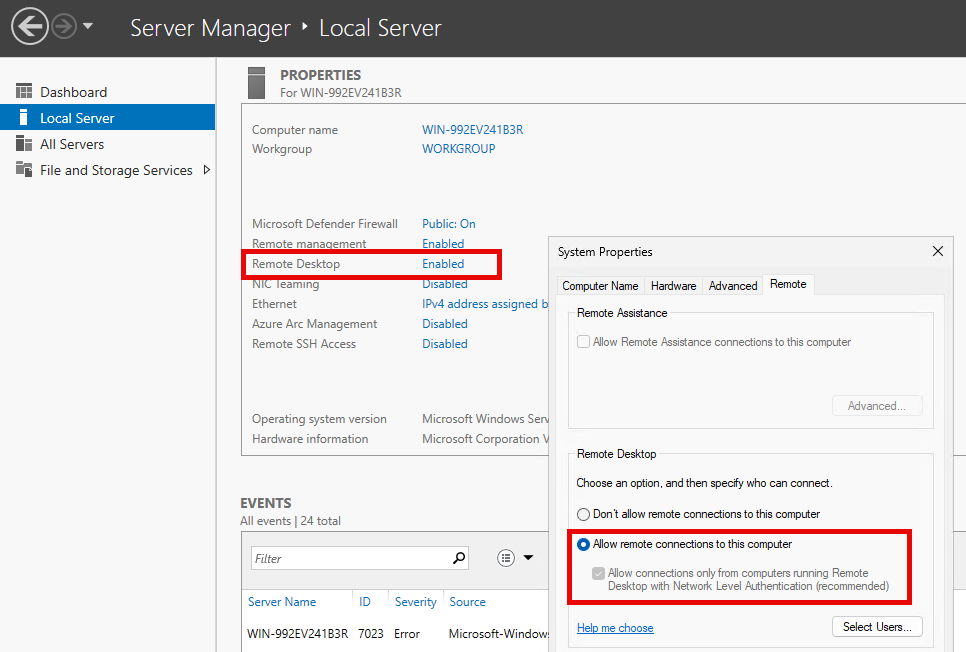
You could also use a local policy or later a group policy for the remote desktop settings.
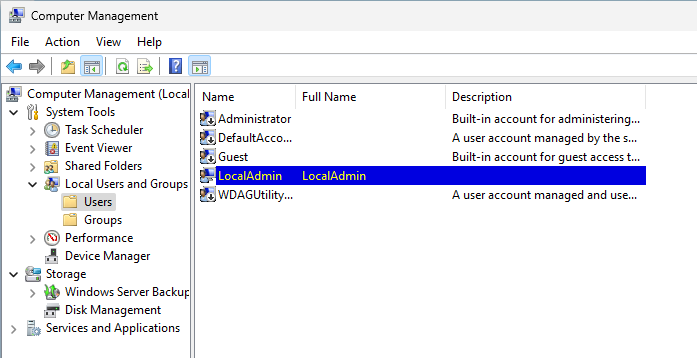
Local administrator account
I have created a new local account called "LocalAdmin" and added the account to the local group "Administrators". I have deactivated the local administrator account:
Microsoft Security Baseline (Template Hardening)
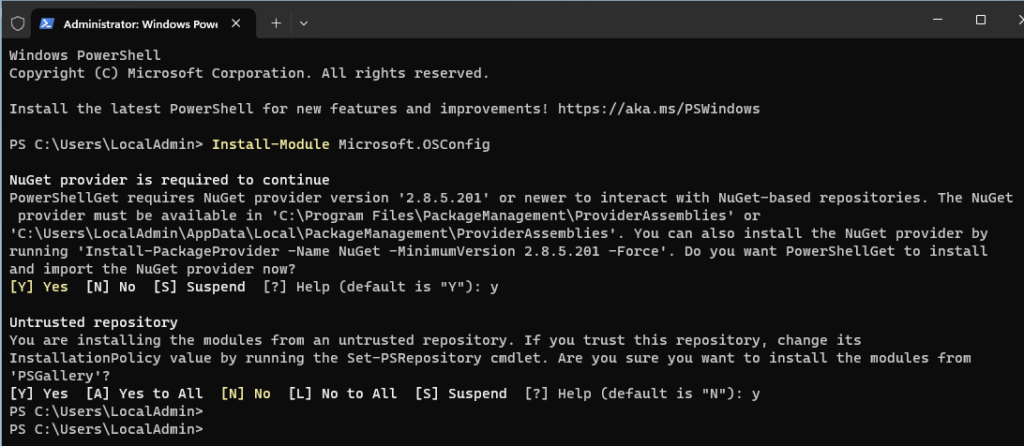
A minimum level of security can also be integrated directly into the template. Microsoft provides the security baseline for this purpose. The PowerShell module Microsoft.OSConfig can be used with Windows Server 2025. The module makes it very easy to use the Security Baseline as a Desired State Configuration. Microsoft.OSConfig can be installed with the following command:
Install-Module -Name Microsoft.OSConfig
Alternatively, OSConfig can also be downloaded and installed directly from the PowerShell Gallery. The corresponding link can be found here:
- PowerShell Gallery Microsoft.OSConfig
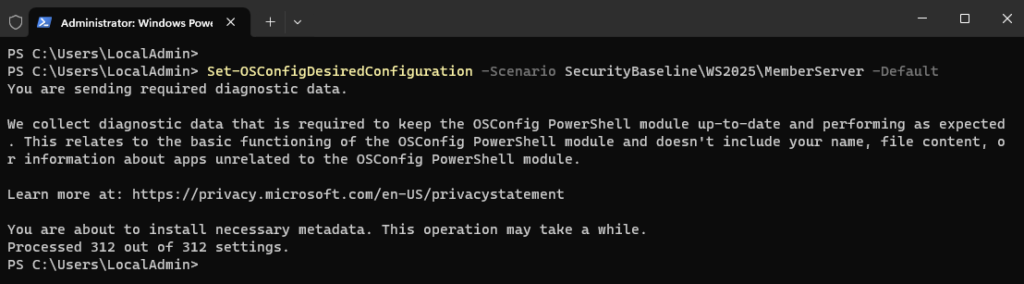
OSConfig supports several security profiles, including for domain controllers and servers without an AD connection. There is also a corresponding profile for member servers of an Active Directory, which can be applied with the following command:
Set-OSConfigDesiredConfiguration -Scenario SecurityBaseline\WS2025\MemberServer -Default
Further information on the security baseline can be found here:
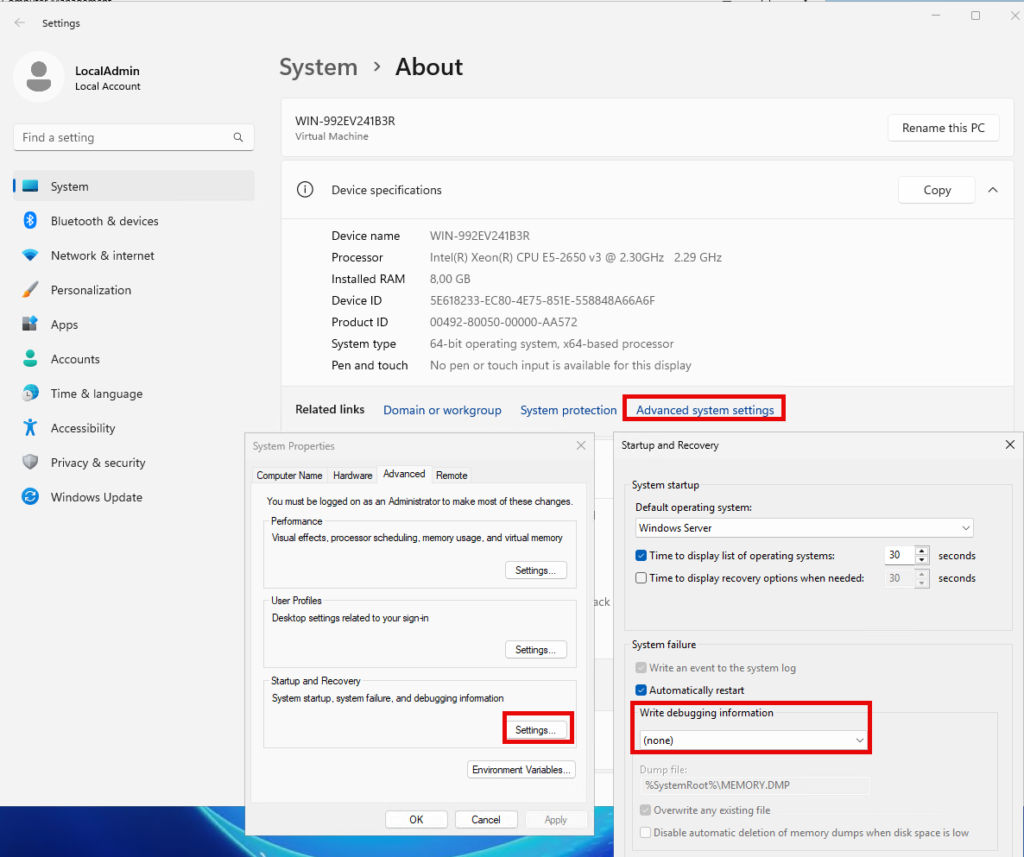
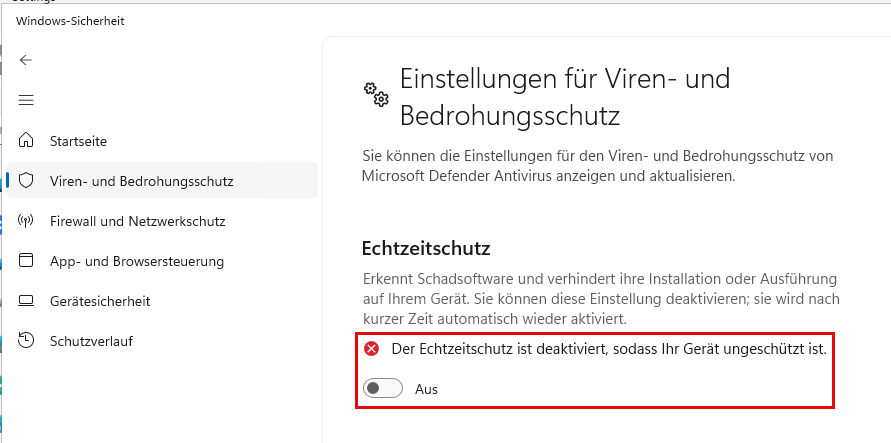
I also switch off memory dumps. Memory dumps can contain passwords and private keys in plain text and should therefore not be left in the file system after a server crash:
If you want to delve deeper into the topic of hardening, you can find the CIS benchmarks at the "Center for Internet Security":
As of today (04.11.2024) there is still no benchmark for Windows Server 2025, but you can follow the recommendations for Windows Server 2022 quite well.
However, I would implement these very extensive policies as a group policy rather than in the template. The basic security settings are made via the baseline security policy in the template, while fine tuning is better done via group policy.
Remove apps from standard template
Windows Server 2025 is delivered with just a few apps installed. But I don't need an Edge browser or Paint on a server:
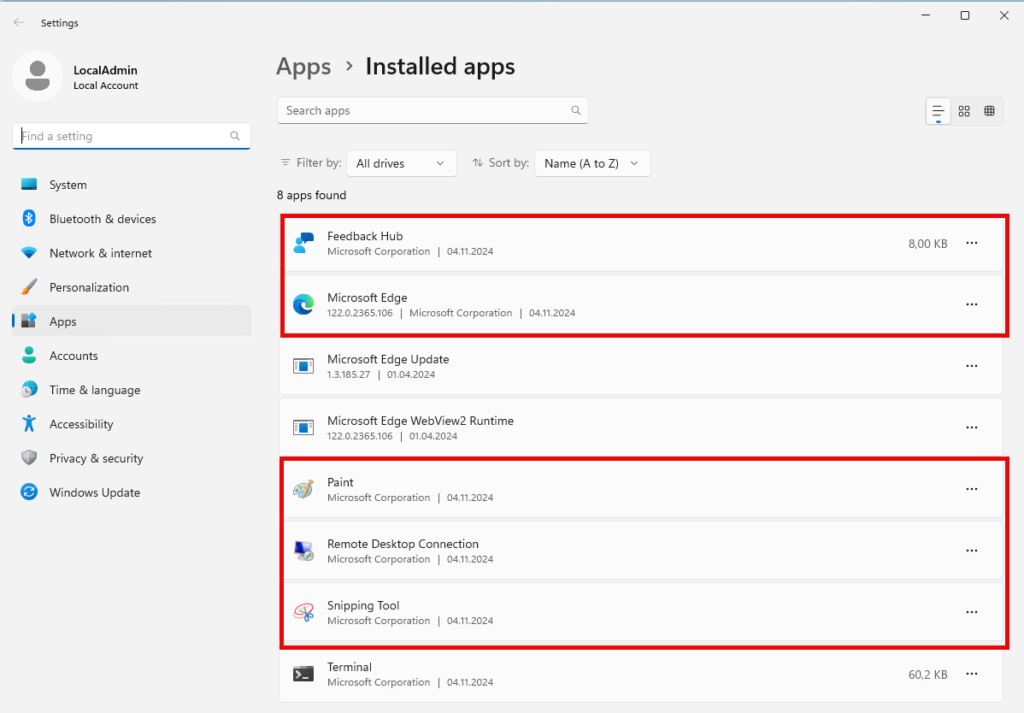
I uninstalled the apps and only kept the Edge WebView2 runtime and the terminal:
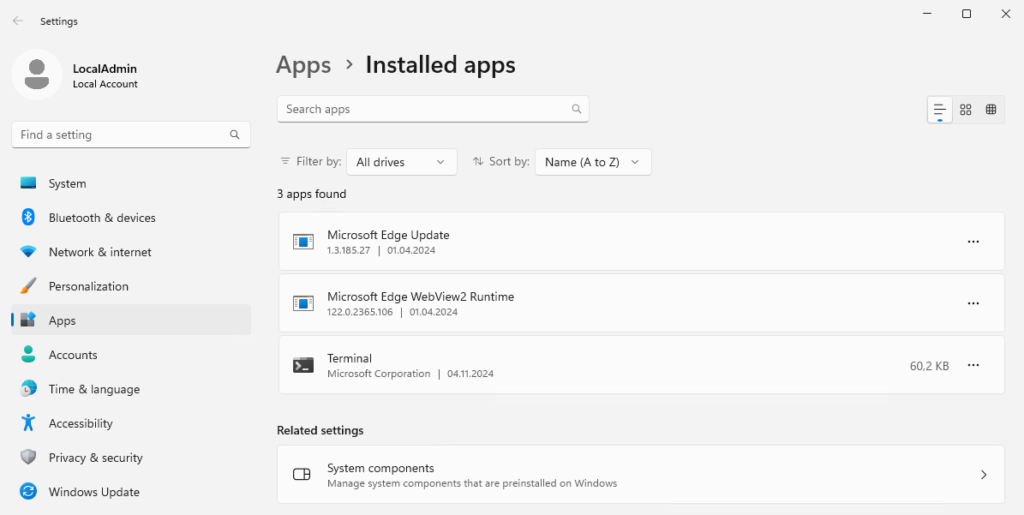
The "Remote Desktop Connection" app is usually not required on a server; an RDP connection is established to the server, but not from the server to the next server.
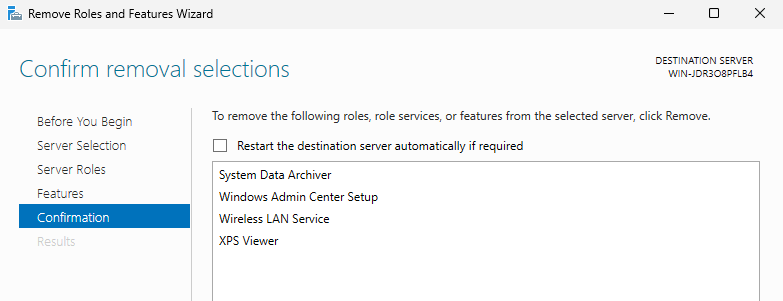
I have also uninstalled the following features via Server Manager:
- System Data Archiver
- Windows Admin Center Setup
- Wireless LAN service
- XPS Viewer
No further adjustments are currently necessary in my template. If I notice any further points during the tests, I will update the article.
AzureArc Setup und SysTray kann man noch entfernen wenn man die Server on-premises verwendet:
Remove-WindowsCapability -Name „AzureArcSetup~~~~“ -Online
Ist der System Data Archiver wirklich nur für die Server Insides, um einen Trend zu sehen?
Ist es problemlos diesen zu entfernen?
Auch von mir ein Danke für deine Arbeit lieber Frank.
Hallo,
nice! Danke
für 2022 was ähnliches gefunden… gibt´s das auch für 2019?
MfG
Nice work
werd mich auch mal ran setzen